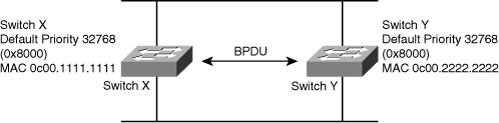
Which switch is designated as the root bridge in this topology?
Which security measure must you take for native VLANs on a trunk port?
Which security measure must you take for native VLANs on a trunk port?
which type of Layer 2 attack does an attacker broadcast BDPUs with a lower switch priority?
In which type of Layer 2 attack does an attacker broadcast BDPUs with a lower switch priority?
Which syslog level is associated with LOG_WARNING?
Which syslog level is associated with LOG_WARNING?
Which type of management reporting is defined by separating management traffic from production traffic?
Which type of management reporting is defined by separating management traffic from production traffic?
How are Cisco IOS access control lists processed?
How are Cisco IOS access control lists processed?
Which type of network masking is used when Cisco IOS access control lists are configured?
Which type of network masking is used when Cisco IOS access control lists are configured?
Which option represents a step that should be taken when a security policy is developed?
Which option represents a step that should be taken when a security policy is developed?
Which two options represent a threat to the physical installation of an enterprise network?
Which two options represent a threat to the physical installation of an enterprise network? (Choose two.)
Which four configurations are required (with no defaults)?
You want to use the Cisco Configuration Professional site-to-site VPN wizard to implement a site- to-site IPsec VPN using pre-shared key.
Which four configurations are required (with no defaults)? (Choose four.)