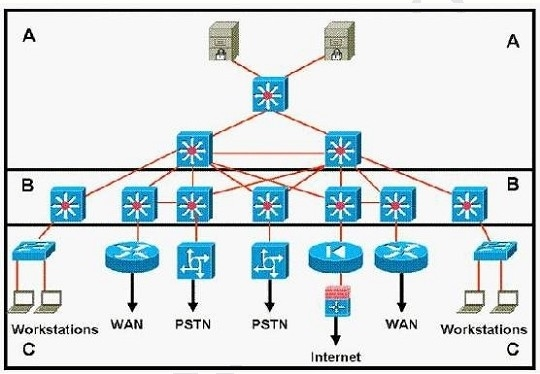
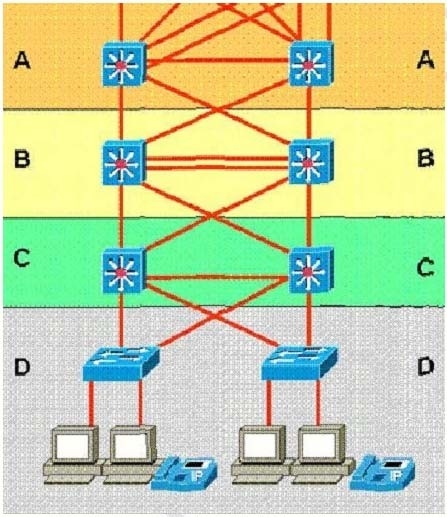
Refer to exhibits:
DRAG DROP<br /><br />Refer to exhibits:<br /><a href="//cdn.briefmenow.org/wp-content/uploads/640-816/H/13-1.png"><img class="aligncenter size-full" src="//cdn.briefmenow.org/wp-content/uploads/640-816/H/13-1.png" alt="" /></a><br /><br />
DRAG DROP….Drag the description on the left to the correct router mode on right…
DRAG DROP<br /><br /><a href="//cdn.briefmenow.org/wp-content/uploads/640-816/H/12-1.png"><img class="aligncenter size-full" src="//cdn.briefmenow.org/wp-content/uploads/640-816/H/12-1.png" alt="" /></a><br /><br />Drag the description on the left to the correct router mode on right.<br /><br />
DRAG DROP.Drag and drop. Match the items on the left with its corresponding definition on the right….
DRAG DROP<br />Drag and drop. Match the items on the left with its corresponding definition on the right.<br /><a href="//cdn.briefmenow.org/wp-content/uploads/640-816/H/17-1.png"><img class="aligncenter size-full" src="//cdn.briefmenow.org/wp-content/uploads/640-816/H/17-1.png" alt="" /></a><br /><br />
Which statement accurately represents the characteristics of the core layer in this design?
Which Cisco security management solution provides the means to identify, isolate, and counter security.threats
Which Cisco security management solution provides the means to identify, isolate, and counter security
threats to the network?
Which three types of WAN topologies can be deployed in the Cisco Enterprise Architecture Enterprise.Edge WAN m
Which three types of WAN topologies can be deployed in the Cisco Enterprise Architecture Enterprise
Edge WAN module? (Choose three.)
Which two statements correctly identify the layers of the Enterprise Campus module?
DRAG DROP..Drag and drop question. Drag the items to the proper locations….
DRAG DROP<br /><br />Drag and drop question. Drag the items to the proper locations.<br /><a href="//cdn.briefmenow.org/wp-content/uploads/640-816/H/1-1.png"><img class="aligncenter size-full" src="//cdn.briefmenow.org/wp-content/uploads/640-816/H/1-1.png" alt="" /></a><br /><br />
DRAG DROP..The left describes some types of connections, while the right describes some types of cables..Drag
DRAG DROP<br /><br />The left describes some types of connections, while the right describes some types of cables.<br />Drag the items on the left to the proper locations<br /><a href="//cdn.briefmenow.org/wp-content/uploads/640-816/G/25-1.png"><img class="aligncenter size-full" src="//cdn.briefmenow.org/wp-content/uploads/640-816/G/25-1.png" alt="" /></a><br /><br />
You are required to fill in the protocol, address, and mask in this command using the choices below:
DRAG DROP<br /><br />You are configuring the office. In particular the host C, with the IP address 192.168.125.34/27, needs to be configured so that it cannot access hosts outside its own subnet. You decide to use the following command:<br /><br />access-list 100 deny protocol address mask any<br /><br />You are required to fill in the protocol, address, and mask in this command using the choices below:<br /><a href="//cdn.briefmenow.org/wp-content/uploads/640-816/G/24-1.png"><img class="aligncenter size-full" src="//cdn.briefmenow.org/wp-content/uploads/640-816/G/24-1.png" alt="" /></a><br /><br />