Would the Security Technology Requirements document be used to determine a customer’s security requireme
During which phase of the Steps to Success methodology for Cisco SMB Security Solutions would the Security Technology Requirements document be used to determine a customer’s security requirements?
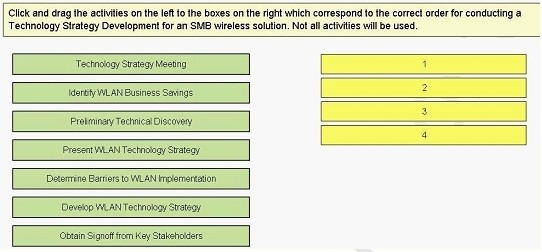
Click and Drag the activities on the left to the boxes on the right which correcr order for conducting a techn
which important tool can be used to determine the bandwidth used by different codecs with various voice protoc
When determining a customer’s technical requirements for a Cisco Unified Communications solution, which important tool can be used to determine the bandwidth used by different codecs with various voice protocols over different media?
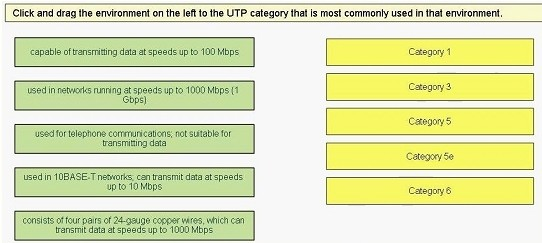
Click and Drag the environment on the left to the UTP category that is most commonly used in that environment
Which two interfaces are enabled for 802.1Q encapsulation?
which service?
In addition to writing information to a trace file, the Cisco CRS System sends standard event logging messages to a syslog server through which service?
which two statements are correct for ports that have been configured with the Smartport role of "IP Phone
In an environment in which multiple VLANs have been defined on Catalyst Express 500 switches, which two statements are correct for ports that have been configured with the Smartport role of “IP Phone+Desktop”? (Choose two.)
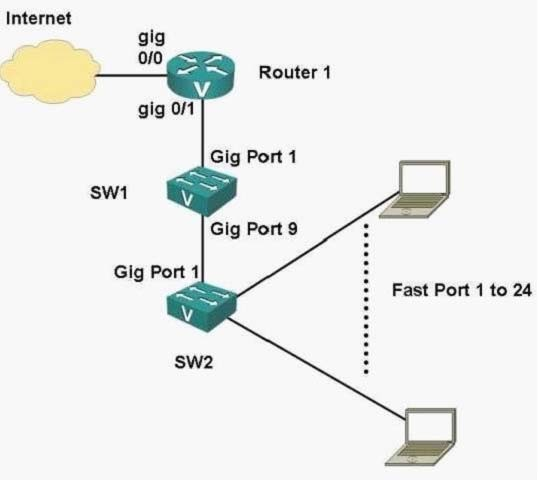
which factors affect the router configuration you select?
Refer to the exhibit. In a Cisco Single-Site Secure Network Foundation implementation, which factors affect the router configuration you select?
which ways does remote monitoring allow the monitored call to be selected?
By which ways does remote monitoring allow the monitored call to be selected? (Choose two.)
where does Quote Builder fit into the deal process flow?
When using the Steps to Success Methodology, where does Quote Builder fit into the deal process flow?