What are two ways to secure traffic across a network?
What are two ways to secure traffic across a network? (Choose two)
Which command can be used to verify that RIPv2 is running on a router?
Which command can be used to verify that RIPv2 is running on a router?
What is the cause of the problem?
Which two of these might have caused this problem?
A user is unable to connect to the Cisco Router and Security Device Manager via HTTPS. Which two of these might have caused this problem? (Choose two.)
Which companion switch is recommended to be installed with Cisco Smart Business Communications System?
Which companion switch is recommended to be installed with Cisco Smart Business Communications System?
what is the cause of the problem?
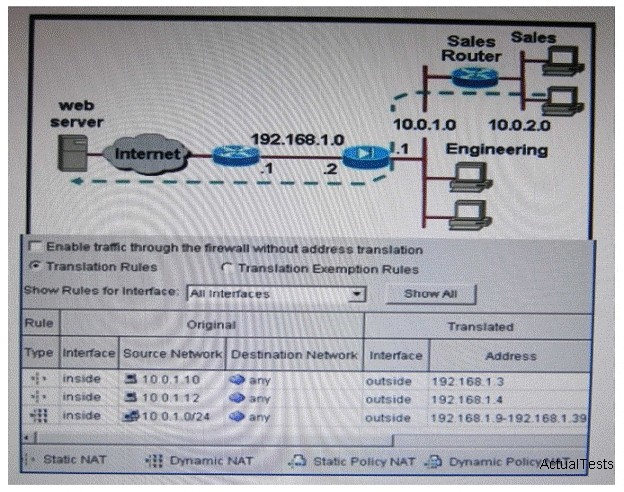
Refer to the exhibit. A host on the Sales subnet (10.0.2.0/24) is not able to initiate a web connection to an outside website. According to the network diagram and partial Cisco Adaptive Security Device Manager configuration shown in the exhibit, what is the cause of the problem?
Which two statements best describe the wireless core feature set using autonomous access points when implement
Which two statements best describe the wireless core feature set using autonomous access points when implementing Wireless Domain Services? (Choose two)
which topology would be the easiest for this customer to set up and manage?
A customer with a small enterprise network of 15 remote sites is trying to optimize its VPN by migrating some remote sites using Frame Relay connections to the Internet to using cable connections to the Internet. Minimizing costs is one of the customer’s highest priorities. Only a moderate amount of IP traffic is passing through the network, most of which is from the remote sites to the central site. IPSec should be used to provide VPN functionality and basic confidentiality is desired.
Based on the traffic patterns, which topology would be the easiest for this customer to set up and manage?
Which critical issue should you account for when implementing an integrated network security management design
Which critical issue should you account for when implementing an integrated network security management design?
Which command allows you to enter the VLAN database?
You are configuring a VLAN and the switch you are using requires that you do so within the VLAN database. Which command allows you to enter the VLAN database?