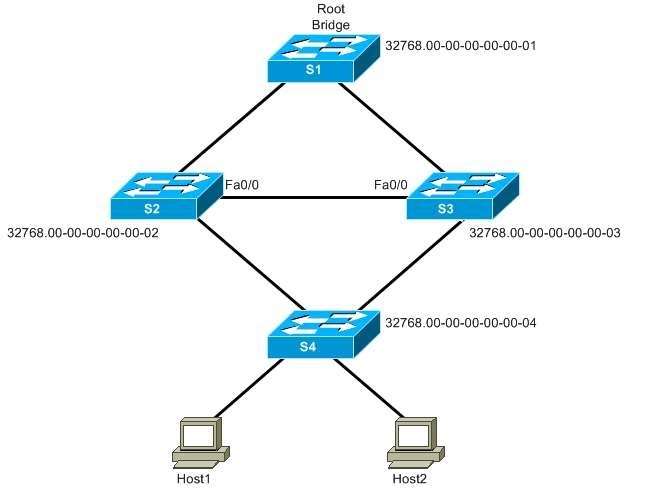
what will occur if the link between S1 and S2 is broken?
Refer to the exhibit.
The network you administer consists of the devices shown in the exhibit. Each link is 100 megabits per second
(Mbps) and is connected to a FastEthernet port. Switch S1 is the root bridge. You enable root guard on Fa0/0
on switch S2 and switch S3 by issuing the spanningtree guard root command in interface configuration mode
on both switch ports. You also enable the UplinkFast feature on S2 and S3 by issuing the spanningtree
uplinkfast command in global configuration mode on both switches.
Which of the following statements best describes what will occur if the link between S1 and S2 is broken?
(Select the best answer.)
Which of the following statements is true regarding the…
Which of the following statements is true regarding the autocommand keyword when used with the username
command on Cisco routers? (Select the best answer.)
Which of the following statements is true regarding sta…
Which of the following statements is true regarding stateful firewalls? (Select the best answer.)
Which of the following SNMP actions are used by an NMS …
Which of the following SNMP actions are used by an NMS to extract information from an SNMP agent? (Select2 choices.)
which of the following vulnerability classifications do…
You are analyzing recent intrusion events in FireSIGHT Defense Center and notice several events with blueicons.
To which of the following vulnerability classifications do the blue icons correspond? (Select the best answer.)
Which of the following statements is true regarding tra…
Which of the following statements is true regarding traditional stateful packetfiltering firewalls? (Select the best
answer.)
Which of the following best describes how an IPS is sim…
Which of the following best describes how an IPS is similar to an IDS? (Select the best answer.)
which of the following features provides a cloudbased s…
Implementing which of the following features provides a cloudbased subscription method of URL filtering that
can be used with Cisco’s ZFW? (Select the best answer.)
Which of the following statements is true regarding the…
Which of the following statements is true regarding the SA lifetime specified in a matching IKE policy? (Select
the best answer.)
Which of the following is an independent cryptographic …
Which of the following is an independent cryptographic processor that provides hardwarebased authentication
services for PCs? (Select the best answer.)