what would be the last legitimate host address in this …
You have been assigned a network ID of 172.16.0.0/26. If you utilize the first network resulting from this ID,
what would be the last legitimate host address in this subnet?
Which two are the limitations of the service password-e…
Which two are the limitations of the service password-encryption command? (Choose two.)
Which of the following items are NOT required to match …
Which of the following items are NOT required to match for two routers to form an OSPF adjacency?
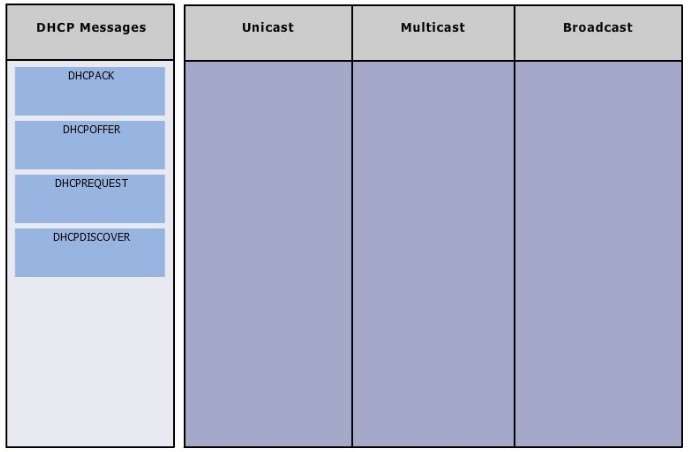
Group the special DHCP messages exchanged over the network…
Which command will save a dynamically learned MAC addre…
Which command will save a dynamically learned MAC address in the running-configuration of a Cisco switch?
Which Cisco Internetwork Operating System (IOS) command…
Which Cisco Internetwork Operating System (IOS) command would be used to define a static route for network
192.168.11.0 through default gateway 192.168.43.1?
Which of the following statements are true of Class C I…
Which of the following statements are true of Class C IP addresses?
Which protocol is used in redundant network topologies …
Which protocol is used in redundant network topologies to avoid receiving multiple copies of the same frame?
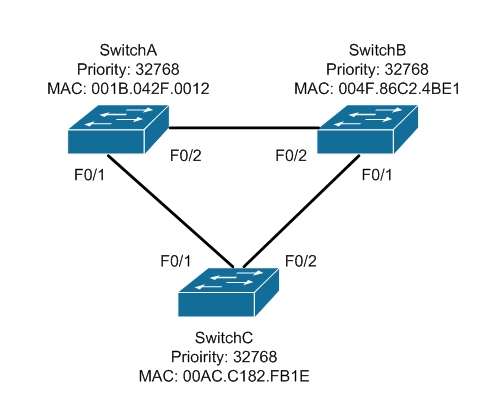
Which switch will become the root bridge?
Which command will display the Virtual LAN (VLAN) frame…
Which command will display the Virtual LAN (VLAN) frame tagging method for a switch link?