What would be other recommended ways of protecting the …
As part of a new initiative to tighten the security of your Cisco devices, you have configured the firewall to
restrict access to the devices from the outside.
What would be other recommended ways of protecting the integrity of the device configuration files on the
devices while ensuring your continued ability to manage the devices remotely? (Choose all that apply.)
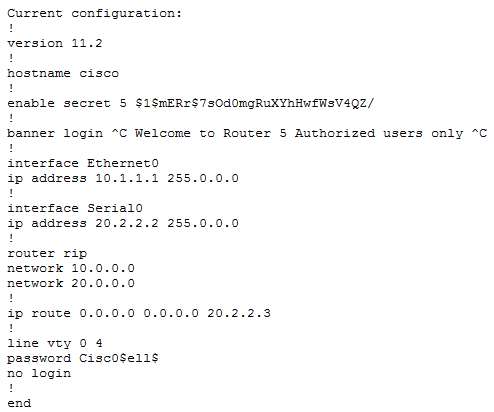
What problems exist?
Which Cisco IOS interface configuration command is used…
Which Cisco IOS interface configuration command is used to configure the private VLAN edge ports on a Cisco
Catalyst 2950 switch?
Which statement is TRUE regarding the switchport protec…
Which statement is TRUE regarding the switchport protected interface configuration command and its effects?
What switch security configuration requires AAA to be c…
What switch security configuration requires AAA to be configured on the switch?
Which command would you use to convey a message regardi…
You are configuring a Cisco router.
Which command would you use to convey a message regarding the remote access security policy of your
organization to a user logging into the router?
Which two statements represent physical security guidel…
Which two statements represent physical security guidelines that should be followed during Cisco security
deployment? (Choose two.)
Which of the following is NOT true of APIC-EM?
Which of the following is NOT true of APIC-EM?
Which service is denoted by TCP/UDP port number 53?
Which service is denoted by TCP/UDP port number 53?
What did you do wrong?
A new security policy has been adopted by your company. One of its requirements is that only one host is
permitted to attach dynamically to each switch port. The security settings on all of the ports have been altered
from the default settings.
You execute the following command on all switch ports of Switch A:
SwitchA(config-if)# switchport port-security maximum 1
After executing the command, you discover that users in the Sales department are still successfully plugging a
hub into a port and then plugging two or three laptops into the hub.
What did you do wrong?