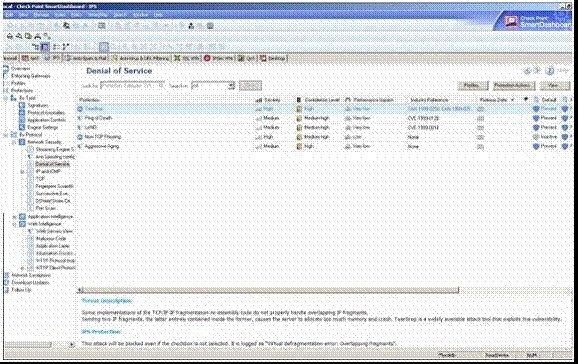
You are configuring IPS, Denial of Service – Teardrop section.
Which of the following is true of Teardrop?

A.
A denial of service vulnerability has been reported in the Linux Kernel. The vulnerability is due to an error in the Linux Kernel IPv6 over IPv4 tunneling driverthat fails to properly handle crafted network packets. Teardrop is a widely available attack tool that exploits this vulnerability
B.
Some implementations of TCP/IP contain fragmentation re-assembly code that does not properly handle overlapping IP fragments. Sending two IP fragments, the latter entirely contained inside the former, causes the server to allocate too much memory and crash. Teardrop is a widely available attack tool that exploits this vulnerability
C.
JPEG is a very popular image file format. Teardrop is a widely available attack tool that exploits this vulnerability Specially crafted JPEG files may be used to create a DoS condition and in some cases, arbitrary code execution
D.
Some implementations of TCP/IP are vulnerable to packets that are crafted in a particular way (a SYN packet in which the source address and port are the same as the destination, i.e., spoofed). Teardrop is a widely available attack tool that exploits this vulnerability
E.
The attacker sends a fragmented PING request that exceeds the maximum IP packet size (64KB). Some operating systems are unable to handle such requests and crash. Teardrop is a widely available attack tool that exploits this vulnerability