which of the following operating systems?
R80 Security Management Server can be installed on which of the following operating systems?
The most important part of a site-to-site VPN deploymen…
The most important part of a site-to-site VPN deployment is the ________ .
what is the reason Jorge cannot see any logs?
If there is an Accept Implied Policy set to “First”, what is the reason Jorge cannot see any logs?
Which authentication scheme requires a user to possess …
Which authentication scheme requires a user to possess a token?
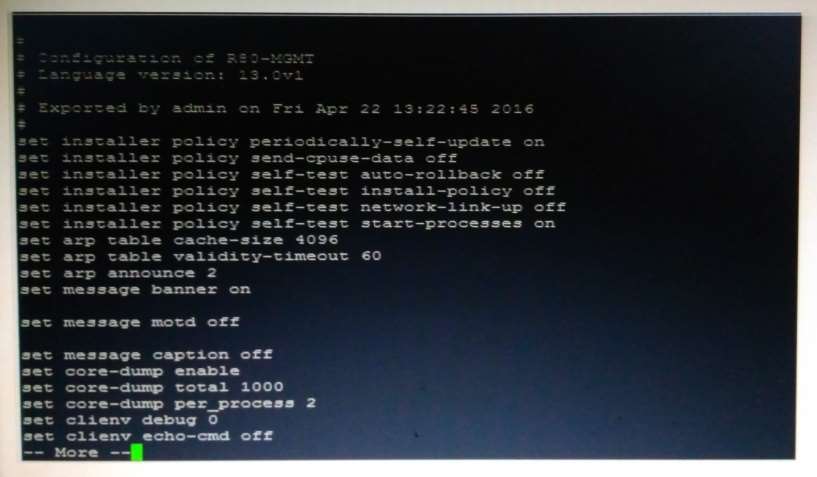
What CLISH command provides this output?
Look at the following screenshot and select the BEST answer.
Fill in the blanks: A security Policy is created in ___…
Fill in the blanks: A security Policy is created in _________ , stored in the _________ , and Distributed to the
various __________ .
Which of the completed statements is NOT true?
Which of the completed statements is NOT true? The WebUI can be used to manage user accounts and:
Which Check Point software blade provides protection fr…
Which Check Point software blade provides protection from zero-day and undiscovered threats?
Fill in the blank: When LDAP is integrated with Check P…
Fill in the blank: When LDAP is integrated with Check Point Security Management, it is then referred to as
_______