Which Security Servers can perform Content Security tasks, but CANNOT perform authentication tasks?
Which Security Servers can perform Content Security tasks, but CANNOT perform authentication
tasks?
How is the Security Gateway VPN Domain created?
What is causing the State Synchronization problem?
A cluster contains two members, with external interfaces 172.28.108.1 and 172.28.108.2. The
internal interfaces are 10.4.8.1 and 10.4.8.2. The external cluster’s IP address is 172.28.108.3,
and the internal cluster’s IP address is 10.4.8.3. The synchronization interfaces are 192.168.1.1
and 192.168.1.2. The Security Administrator discovers State Synchronization is not working
properly, cphaprob if command output displays as follows: What is causing the State
Synchronization problem?
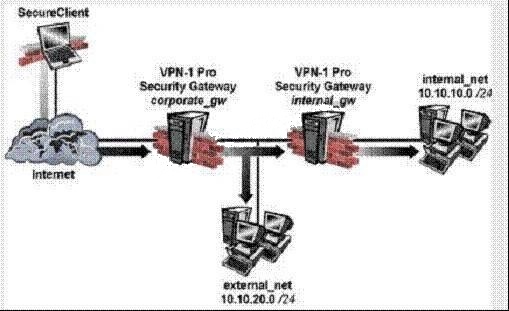
How can you completely tear down a specific VPN tunnel in an intranet IKE VPN deployment?
How can you completely tear down a specific VPN tunnel in an intranet IKE VPN deployment?
How can you completely tear down a specific VPN tunnel in an intranet IKE VPN deployment?
How can you completely tear down a specific VPN tunnel in an intranet IKE VPN deployment?
How can you prevent delay-sensitive applications, such as video and voice traffic, from being dropped due to l
How can you prevent delay-sensitive applications, such as video and voice traffic, from being
dropped due to long queue using Check Point QoS solution?
Which machine meets ALL of the following requirements?
You are preparing to deploy a VPN-1 Pro Gateway for VPN-1 NGX. You have five systems to
choose from for the new Gateway, and you must conform to the following requirements:
Operating-system vendor’s license agreement
Check Point’s license agreement
Minimum operating-system hardware specification
Minimum Gateway hardware specification
Gateway installed on a supported operating system (OS)
Which machine meets ALL of the following requirements?
Which machine meets ALL of the following requirements?
You are preparing to deploy a VPN-1 Pro Gateway for VPN-1 NGX. You have five systems to
choose from for the new Gateway, and you must conform to the following requirements:
Operating-system vendor’s license agreement
Check Point’s license agreement
Minimum operating-system hardware specification
Minimum Gateway hardware specification
Gateway installed on a supported operating system (OS)
Which machine meets ALL of the following requirements?
What can Stephanie do to achieve her goal?
Which of the following configurations is MOST appropriate for Jerry?
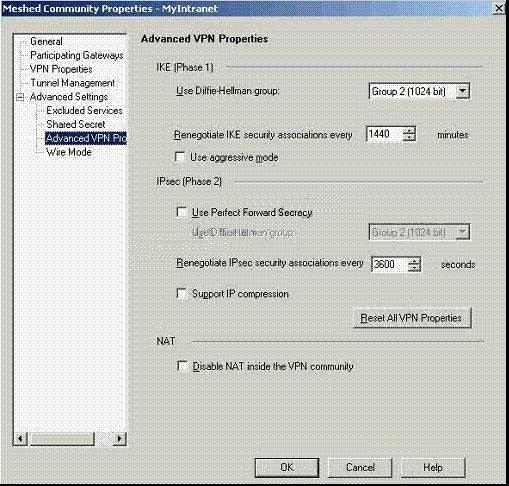
Jerry is concerned that a denial-oF. service (DoS) attack may affect his VPN Communities. He
decides to implement IKE DoS protection. Jerry needs to minimize the performance impact of
implementing this new protection. Which of the following configurations is MOST appropriate for
Jerry?