What is used to validate a digital certificate?
What is used to validate a digital certificate?
Which statement defines Public Key Infrastructure?
Which statement defines Public Key Infrastructure? Security is provided:
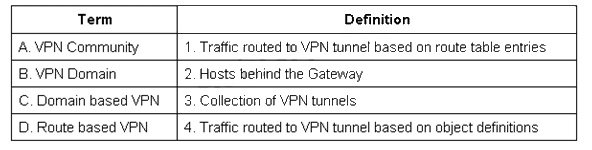
Match the VPN-related terms with their definitions:
Which of the following activities should you do first?
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an
external partner. Which of the following activities should you do first?
Which of the following activities should you do first?
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an
external partner. Which of the following activities should you do first?
How should you configure the VPN match rule?
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit the
Security Gateway bound for all site-to-site VPN Communities, including Remote Access
Communities. How should you configure the VPN match rule?
Which of the following statements is FALSE regarding OSPF configuration on SecurePlatform Pro?
Which of the following statements is FALSE regarding OSPF configuration on SecurePlatform
Pro?
what option would be the BEST choice?
If you need strong protection for the encryption of user data, what option would be the BEST
choice?
Select the response below that includes the available actions:
Review the following list of actions that Security Gateway R76 can take when it controls packets.
The Policy Package has been configured for Simplified Mode VPN. Select the response below that
includes the available actions:
Which technology should you explain to the executives?
Your organization maintains several IKE VPN’s. Executives in your organization want to know
which mechanism Security Gateway R76 uses to guarantee the authenticity and integrity of
messages. Which technology should you explain to the executives?