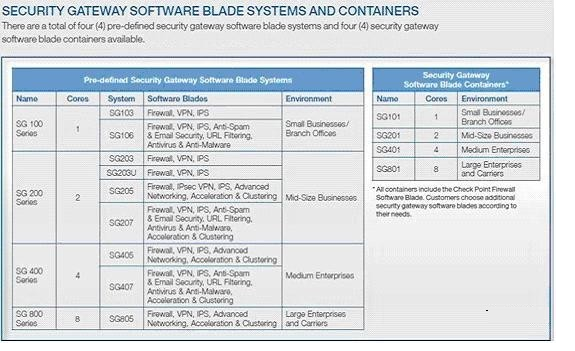
Which of the containers you have to choose from based on number of gateways?
The most recommended and manageable method for authentication among gateways and remote clients is:
The most recommended and manageable method for authentication among gateways and remote clients is:
What other way can you use to administer Security Policy apart from CheckPoint SmartDashboard?
What other way can you use to administer Security Policy apart from CheckPoint SmartDashboard?
A __________________ ___________________ is a trusted third party that can provide a public key even over an u
A __________________ ___________________ is a trusted third party that can provide a public key even over an untrusted network such as the Internet.
The default track column of the newly created Default rule is set to:
Which of the following question(s) will you raise when planning a VPN topology?
Which of the following question(s) will you raise when planning a VPN topology?
1. Who needs secure/private access?
2. From a VPN point of view, what will be the structure of the organization?
3. Internally managed gateways will authenticate each other using certificates
4. How will externally managed gateways authenticate
5. What VPN topology will be suitable?
Which of the following are the disadvantages of symmetric encryption?
Which of the following are the disadvantages of symmetric encryption?
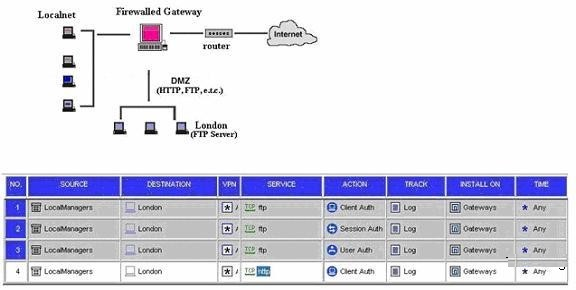
What rule would allow Local Managers to access London (the FTP server) after successful User Authentication?
VPN deployments can be two types and these are:
VPN deployments can be two types and these are:
ISAKMP/Oakley provides a mean to:
ISAKMP/Oakley provides a mean to: