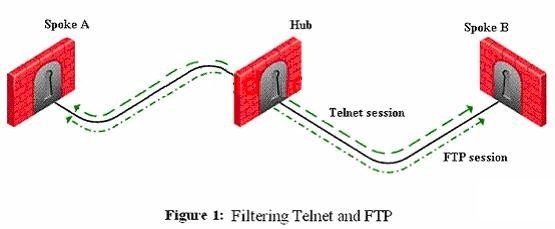
VPN routing between Gateways (star or mesh) can be configured by editing which of the following configuration
How many phases are involved in the IKE encryption scheme?
How many phases are involved in the IKE encryption scheme?
In IPSO file structure, which of the following file enables execution of programs on startup?
In IPSO file structure, which of the following file enables execution of programs on startup?
What file must you edit to fine-tune your Eventia Reporter for improve performance? Assume you are dealing wit
What file must you edit to fine-tune your Eventia Reporter for improve performance? Assume you are dealing with Unix system.
What key in your keyboard provides methods of automatic command-line completion?
What key in your keyboard provides methods of automatic command-line completion?
Which of the following are true of mesh and star community? Select all the correct answers.
Which of the following is true regarding the configuration that may not map to the new appliance?
When deploying a new IP Appliance to replace an old one, the existing configuration may not necessarily map directly to the new appliance. Which of the following is true regarding the configuration that may not map to the new appliance?
What is likely to happen if a user from the internal network tries to access the Internet using HTTP?
Which of the following rule will hide the InternalNetwork behind the external IP address of the SmartLSM Secur
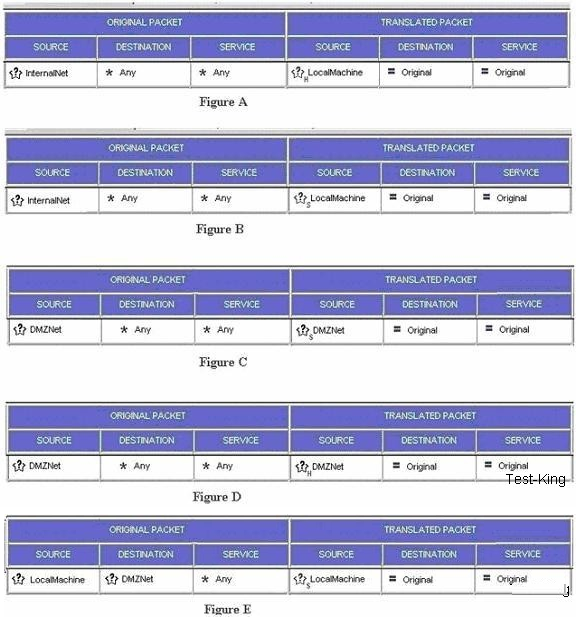
Study the diagram and proceed to answer the question. Which of the following rule will hide the InternalNetwork behind the external IP address of the SmartLSM Security Gateway. Note: a) Use the LocalMachine dynamic object to represent the SmartLSM Gateway , b) Use the InternalNet, DMZnet and AuxiliaryNet dynamic objects to represent the respective networks behind the SmartLSM Gateway.
Why should User Authentication not be suitable with HTTP sessions?
Why should User Authentication not be suitable with HTTP sessions?