What is likely to be the problem? Diagram 2 shed more light on the answer.
What sort of attack is this and what would you deploy to defend against this?
Sharon wishes to communicate with George. During the exchange of public key between Sharon and George, Craig is able to intercept the key. And as soon as the communications begins, Craig is able to intercept the message to George, forges it and sends it to him. What sort of attack is this and what would you deploy to defend against this?
NAT Generated Rule question: The rule that specifies that for connections that originate in the external netwo
NAT Generated Rule question: The rule that specifies that for connections that originate in the external network, the destination address of the packet is translated and this is known as:
if the URL address you are accessing matches two or more categories, and one of them is blocked then what is l
How would you about the setup?
You need to setup a new corporate VPN between your head-office and all your branches. You need to choose the strongest and the most secure algorithms for the VPN between the head-office and legal branch office. And for the VPN between the head-office and marketing branch, you must use shorter keylength encryption algorithm e.g. DES. How would you about the setup?
For SecuRemote/SecureClient to resolve the names of internal hosts behind the Security Gateway with non-unique
For SecuRemote/SecureClient to resolve the names of internal hosts behind the Security Gateway with non-unique IP addresses using an internal DNS server, what must you implement?
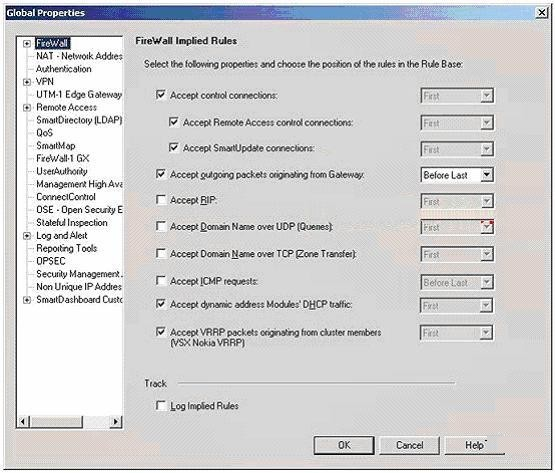
How would you access Global Properties? Choose the best answer.
What would happen to the disabled rules if you fail to re-install your security policy after reenabling these
What would happen to the disabled rules if you fail to re-install your security policy after reenabling these disabled rules?
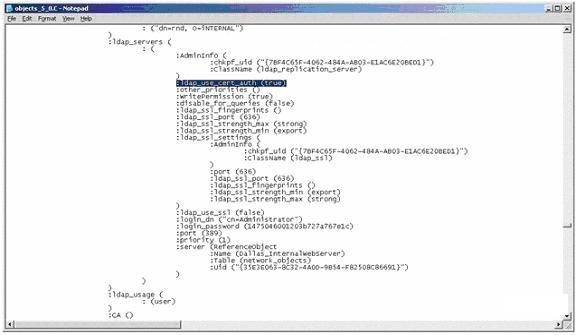
In addition to this, what parameter must be set in objects_5_0.C file?
The command " show ip multicast boundary" query will:
The command ” show ip multicast boundary” query will: