To execute the commands in file from the IPSO shell (not the CLI) you would enter which of the following comma
You create a file config.txt that contains a series of CLI commands. To execute the commands in file from the IPSO shell (not the CLI) you would enter which of the following command?
Which of the following is true?
Your remote Security Gateway is configured to support remote users access from their homes. These users use DSL dialup connection. Some of these users keep complaining of lost of connections. In order to resolve the problem, you go to the SmartView Tracker and notice that there is no indication that their (users) configurations have been tamper with. The remote Security Gateway is setup with static NAT.
Which of the following is true?
Select all the correct answers.
Which of the following points must you consider when defining these plans? Select all the correct answers.
The policy should allow the desktop users to work as freely as possible, but at the same time makes it hard to attack the remote users’ desktop. Which of the following points must you consider when defining these plans? Select all the correct answers.
Establishing Remote Access VPN requires configuration on both the gateway side and the:
Establishing Remote Access VPN requires configuration on both the gateway side and the:
What will a or Home key will allow you to achieve?
You are using Command Line Editing keys in the SecurePlatform. What will a or Home key will allow you to achieve?
which of the following options below lists the correct steps you will take to achieve this?
You want to download a contracts file from Checkpoint User Center website (when upgrading your Security Gateway from R65 to R70), which of the following options below lists the correct steps you will take to achieve this?
Which of the following will you configure?
If aggressive mode is selected for your IPSec tunnel, the gateway performs the IKE negotiation using how many
If aggressive mode is selected for your IPSec tunnel, the gateway performs the IKE negotiation using how many packets during phase 1 exchange?
Which mode would you run your IPSO appliance if you want it to function as a layer 2 bridge?
Which mode would you run your IPSO appliance if you want it to function as a layer 2 bridge?
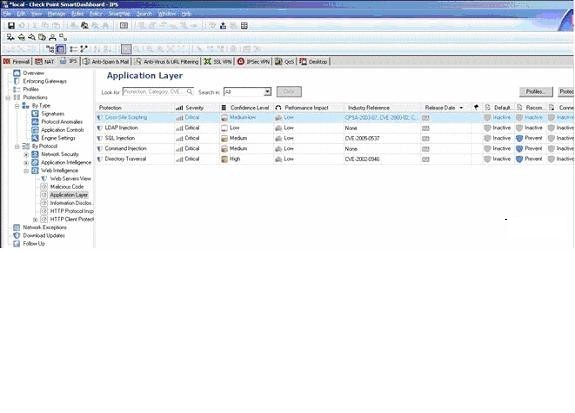
Application Intelligence feature of the IPS prevent and defend attacks of which of the OSI layer?
Application Intelligence feature of the IPS prevent and defend attacks of which of the OSI layer?