Which of the following services is NOT provided by a CIFS resource?
VPN-1 NGX includes a resource mechanism for working with the Common Internet File System (CIFS). However, this service only provides a limited level of actions for CIFS security. Which of the following services is NOT provided by a CIFS resource?
Which of the following is true of VPN Tunnel Interfaces (VTI)? Select of all the correct answers.
Which back up method does Check Point recommend anytime outside a maintenance window?
Check Point recommends that you back up systems running Check Point products. Run your back ups during maintenance windows to limit disruptions to services, improve CPU usage, and simplify time allotment. Which back up method does Check Point recommend anytime outside a maintenance window?
What is the problem, and how do you fix it?
You want to block corporate internal-net and localnet from accessing Web sites containing inappropriate content. You are using WebTrends for URL filtering. You have disabled VPN-1 Control connections in the Global properties. Review the diagram and the Security Policies for GW_A and GW_B in the exhibit provided.
Corporate users and localnet users receive message “Web cannot be displayed”. In SmartView Tracker, you see the connections are dropped with message “content security is not reachable”.
What is the problem, and how do you fix it?
When carrying out a backup operation on R70, you will have to backup which of the following files?
When carrying out a backup operation on R70, you will have to backup which of the following files?
Which back up method does Check Point recommend every couple of months, depending on how frequently you make c
Check Point recommends that you back up systems running Check Point products. Run your back ups during maintenance windows to limit disruptions to services, improve CPU usage, and simplify time allotment. Which back up method does Check Point recommend every couple of months, depending on how frequently you make changes to the network or policy?
What could cause this behavior?
Wayne configures an HTTP Security Server to work with the content vectoring protocol to screen forbidden sites. He has created a URI resource object using CVP with the following settings:
Use CVP
Allow CVP server to modify content
Return data after content is approved
He adds two rules to his Rule Base: one to inspect HTTP traffic going to known forbidden sites, the other to allow all other HTTP traffic.
Wayne sees HTTP traffic going to those problematic sites is not prohibited.
What could cause this behavior?
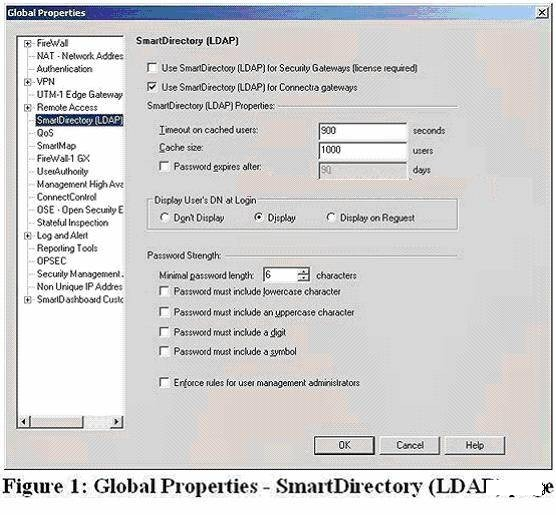
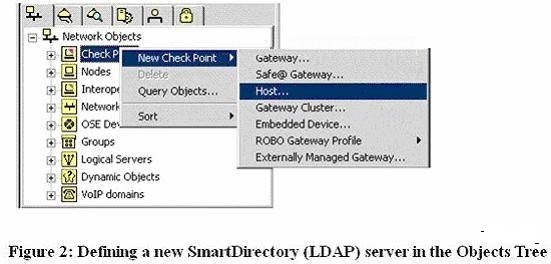
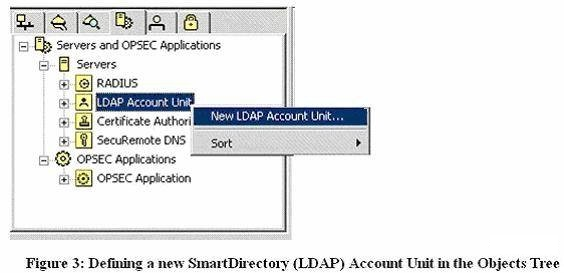
Where would you go enable SmartDirectory (LDAP) attributes?
Which back up method does Check Point recommend before major changes, such as upgrades?
Check Point recommends that you back up systems running Check Point products. Run your back ups during maintenance windows to limit disruptions to services, improve CPU usage, and simplify time allotment. Which back up method does Check Point recommend before major changes, such as upgrades?
After creating a snapshot of a Windows 2003 SP2 Security Management Server, you can restore it on a SecurePlat
True or false? After creating a snapshot of a Windows 2003 SP2 Security Management Server, you can restore it on a SecurePlatform R75 Security Management Server, except you must load interface information manually.