What feature is used by control connections to ensure strong authentication between Check Point Nodes?
Check Point Nodes communicate with other Check Point Nodes by means of control connections. What feature is used by control connections to ensure strong authentication between Check Point Nodes?
In ClusterXL, _______ is defined by default as a critical device.
In ClusterXL, _______ is defined by default as a critical device.
Which encryption scheme provides in-place encryption?
Which encryption scheme provides in-place encryption?
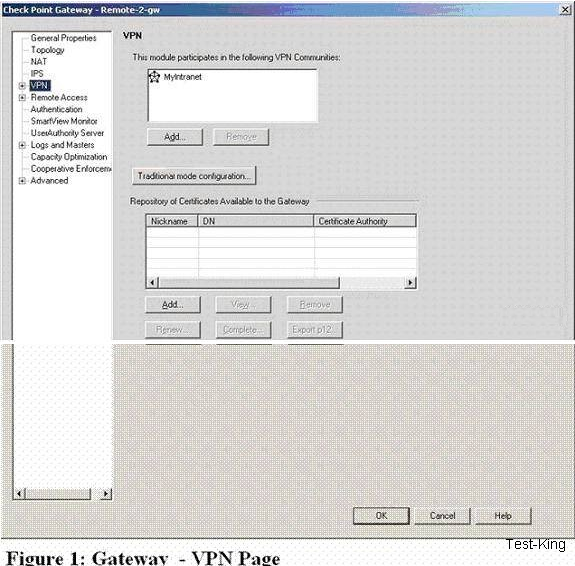
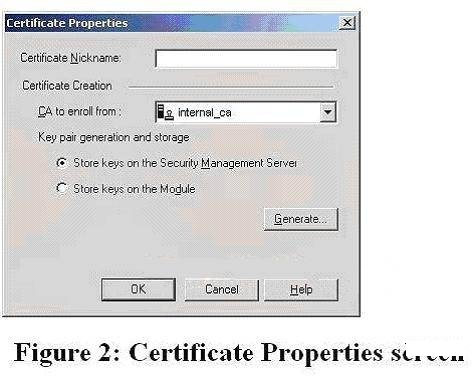
The ICA cannot be used in which of the following situations?
What’s happening?
How should Check Point packages be uninstalled?
How should Check Point packages be uninstalled?
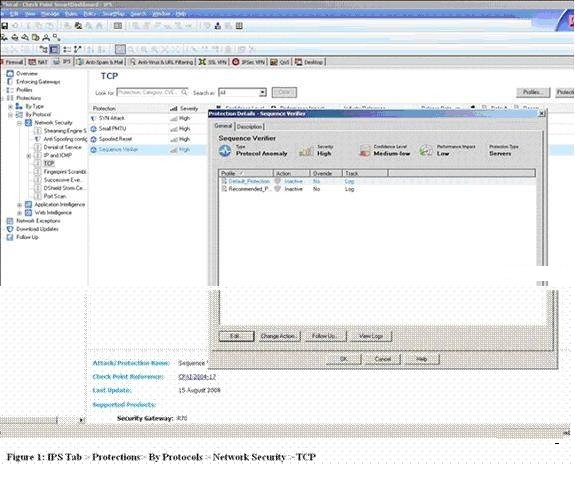
What will be the consequence of disabling TCP state check in the IPS tab?
Which of the following commands shows full synchronization status?
Which of the following commands shows full synchronization status?
Central License management allows a Security Administrator to perform which of the following? Select all that
Central License management allows a Security Administrator to perform which of the following? Select all that apply.
The default cluster administrator user name is:
The default cluster administrator user name is: