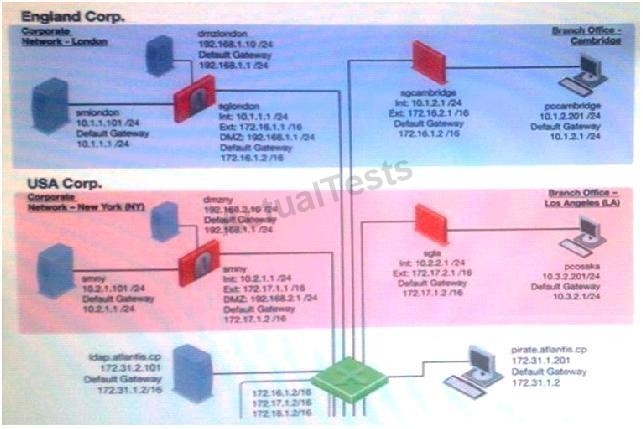
What application would you run in order to modify Eventia Reporter Database settings?
What application would you run in order to modify Eventia Reporter Database settings?
How is this possible?
In IPSO directory structure, what does config folder contain?
In IPSO directory structure, what does config folder contain?
The following graphic illustrates which command being issued on SecurePlatform?
The following graphic illustrates which command being issued on SecurePlatform?
When dealing with IPSO clustering modes, which of the following is true of the forwarding mode?
When dealing with IPSO clustering modes, which of the following is true of the forwarding mode?
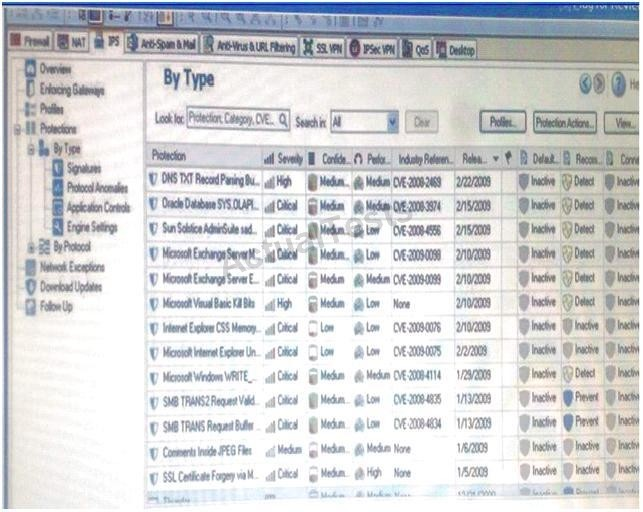
Using the out below, how would Laura change the Default_Protection on Performance Impact Protections classifie
Laura notices the Microsoft Visual Basic Bits Protection is set to inactive. She wants to set the Microsoft Visual Basic Kill Bits Protection and all other Low Performance Impact Protections to Prevent. She asks her manager for approval and stated she can turn theses on. But he wants Laura to make sure no high Performance Impacted Protections are turned on while changing this setting.
Using the out below, how would Laura change the Default_Protection on Performance Impact Protections classified as low from inactive to prevent until meeting her other criteria?
What is the Checkpoint recommended way to troubleshoot this?
Your new System Administrator is setting up User Authentication for the very first time. After the setting up she tests it but does not work. You then ask her to follow the CheckPoint recommendation for troubleshooting. What is the Checkpoint recommended way to troubleshoot this?
How can they solve this problem and stabilize the tunnel?
John is the MegaCorp Security Administrator, and is using Check Point R71. Malcolm is the Security Administrator of a partner company and is using a different vendor’s product and both have to build a VPN tunnel between their companies. Both are using clusters with Load Sharing for their firewalls and John is using ClusterXL as a Check Point clustering solution. While trying to establish the VPN, they are constantly noticing problems and the tunnel is not stable and then Malcolm notices that there seems to be 2 SPIs with the same IP from the Check Point site. How can they solve this problem and stabilize the tunnel?
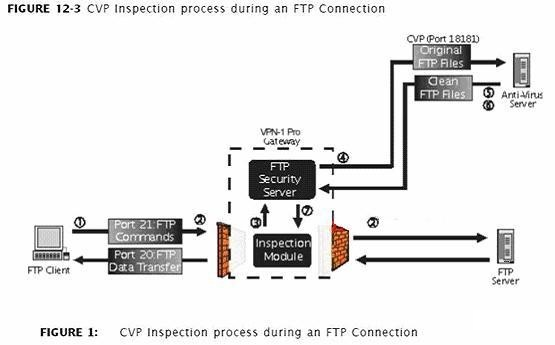
What is likely to happen if the client initiates a data transfer over port 20? Choose the best answer.
Which Check Point QoS feature is used to dynamically allocate relative portions of available bandwidth?
Which Check Point QoS feature is used to dynamically allocate relative portions of available bandwidth?