While you are working in Network Voyager, which keys or operations are not recommended in your browser?
While you are working in Network Voyager, which keys or operations are not recommended in your browser?
Why would an Administrator want to verify a security policy? Choose all the correct answers.
Why would an Administrator want to verify a security policy? Choose all the correct answers.
The command line to use when monitoring system status is:
The command line to use when monitoring system status is:
Which folder or directory contains the list of IP addresses of machines designated as Masters?
Which folder or directory contains the list of IP addresses of machines designated as Masters?
What secure protocol provides secure connection to a SecurePlatform system?
What secure protocol provides secure connection to a SecurePlatform system?
What do you think might be wrong with the address George specified in the browser?
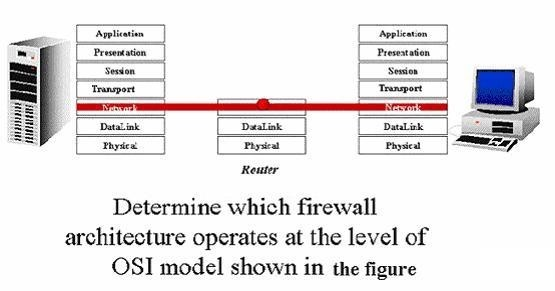
What type of firewall is shown in the diagram?
Which of the following feature provides high availability by avoiding a single point of failure?
Which of the following feature provides high availability by avoiding a single point of failure?
Which of the following is true of Software Blade? Select all the correct answers.
Which of the following is true of Software Blade? Select all the correct answers.
To manually perform a pre-upgrade verification, which of the following file would you run?
To manually perform a pre-upgrade verification, which of the following file would you run?