What deployment is said to be implemented If the gateway and the Security Management server are deployed on se
What deployment is said to be implemented If the gateway and the Security Management server are deployed on separate machines?
Which of the following is the solution to this problem?
One of the problem of the asymmetric encryption is proving that a public key is authentic and has not been tampered with. Which of the following is the solution to this problem?
Select all the correct answers.
Which of the following is true regarding Transparent Mode?
Which of the following is true regarding Transparent Mode?
The CheckPoint Open Performance Architecture security software running on Intel multicore processors was desig
The CheckPoint Open Performance Architecture security software running on Intel multicore processors was designed to solve which of the following problems?
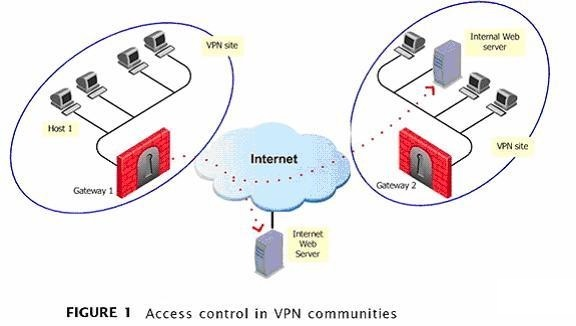
Which of the following may be true when dealing with Access Control and two gateways in the same VPN Community
Which of the following is the rule base file?
Which of the following is the rule base file?
you need to implement Disk Mirroring (RAID 1)?
How many disks do you need to implement Disk Mirroring (RAID 1)?
Anti-Virus Scanning methods are Scan by IP and:
Anti-Virus Scanning methods are Scan by IP and:
If system’s performance is of utmost importance, what deployment type would you implement for Eventia Re
If system’s performance is of utmost importance, what deployment type would you implement for Eventia Reporter?
What application, a support tool, gathers into one text file a wide range of data concerning the Check Point p
What application, a support tool, gathers into one text file a wide range of data concerning the Check Point packages in your system?