What causes the Connection Rejection?
You are reviewing SmartView Tracker entries, and see a Connection Rejection on a Check Point
QoS rule. What causes the Connection Rejection?
What could cause this behavior?
Wayne configures an HTTP Security Server to work with the content vectoring protocol to screen
forbidden sites. He has created a URI resource object using CVP with the following settings:
Use CVP
Allow CVP server to modify content
Return data after content is approved
He adds two rules to his Rule Base: one to inspect HTTP traffic going to known forbidden sites,
the other to allow all other HTTP traffic.
Wayne sees HTTP traffic going to those problematic sites is not prohibited.
What could cause this behavior?
What is the problem, and how do you fix it?
You want to block corporate internal-net and localnet from accessing Web sites containing
inappropriate content. You are using WebTrends for URL filtering. You have disabled VPN-1
Control connections in the Global properties. Review the diagram and the Security Policies for
GW_A and GW_B in the exhibit provided.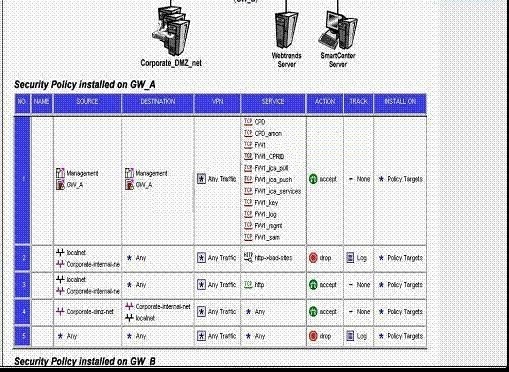
Corporate users and localnet users receive message “Web cannot be displayed”. In SmartView
Tracker, you see the connections are dropped with message “content security is not reachable”.
What is the problem, and how do you fix it?
Which of the following services is NOT provided by a CIFS resource?
VPN-1 NGX includes a resource mechanism for working with the Common Internet File System
(CIFS). However, this service only provides a limited level of actions for CIFS security. Which of
the following services is NOT provided by a CIFS resource?
Which of the following services is NOT provided by a CIFS resource?
VPN-1 NGX includes a resource mechanism for working with the Common Internet File System
(CIFS). However, this service only provides a limited level of actions for CIFS security. Which of
the following services is NOT provided by a CIFS resource?
How do you configure VPN routing in this star VPN Community?
Your organization has many VPN-1 Edge gateways at various branch offices, to allow VPN-1
Secure Client users to access company resources. For security reasons, your organization’s
Security Policy requires all Internet traffic initiated behind the VPN-1 Edge gateways first be
inspected by your headquarters’ VPN-1 Pro Security Gateway. How do you configure VPN routing
in this star VPN Community?
Which of the following is a possible cause?
Robert has configured a Common Internet File System (CIFS) resource to allow access to the
public partition of his company’s file server, on \\erisco\goldenapple\files\public. Robert receives
reports that users are unable to access the shared partition, unless they use the file server’s IP
address.
Which of the following is a possible cause?
Which type of address translation should you use, to ensure the two networks access each other through the VPN
You want to create an IKE VPN between two VPN-1 NGX Security Gateways, to protect two
networks. The network behind one Gateway is 10.15.0.0/16, and network 192.168.9.0/24 is behind
the peer’s Gateway. Which type of address translation should you use, to ensure the two networks
access each other through the VPN tunnel?
Which type of address translation should you use, to ensure the two networks access each other through the VPN
You want to create an IKE VPN between two VPN-1 NGX Security Gateways, to protect two
networks. The network behind one Gateway is 10.15.0.0/16, and network 192.168.9.0/24 is behind
the peer’s Gateway. Which type of address translation should you use, to ensure the two networks
access each other through the VPN tunnel?
Which is the BEST configuration option to protect internal users from malicious Java code, without stripping J
Which is the BEST configuration option to protect internal users from malicious Java code, without
stripping Java scripts?

