Which machine meets ALL of the following requirements?
You are preparing to deploy a VPN-1 Pro Gateway for VPN-1 NGX. You have five systems to
choose from for the new Gateway, and you must conform to the following requirements:
Operating-system vendor’s license agreement
Check Point’s license agreement
Minimum operating-system hardware specification
Minimum Gateway hardware specification
Gateway installed on a supported operating system (OS)
Which machine meets ALL of the following requirements?
What can Stephanie do to achieve her goal?
Which of the following configurations is MOST appropriate for Jerry?
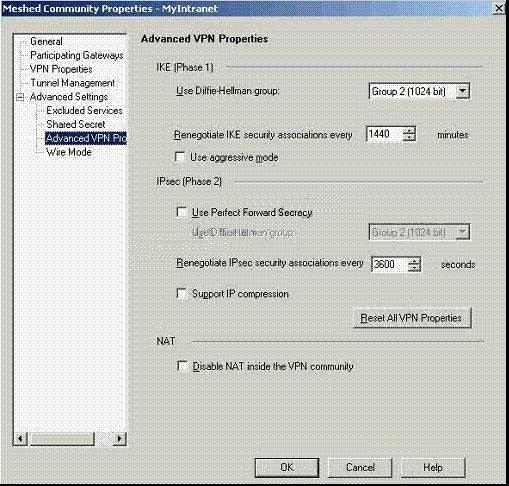
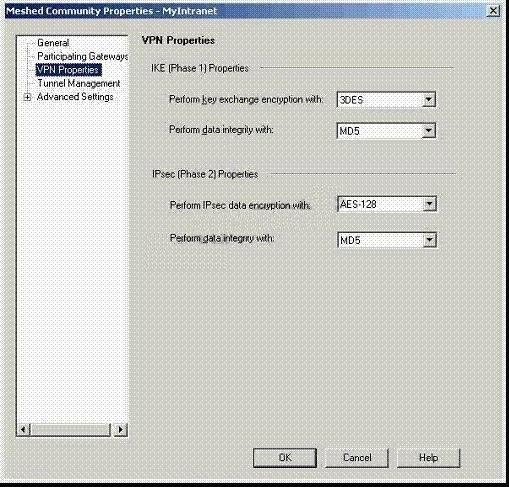
Jerry is concerned that a denial-oF. service (DoS) attack may affect his VPN Communities. He
decides to implement IKE DoS protection. Jerry needs to minimize the performance impact of
implementing this new protection. Which of the following configurations is MOST appropriate for
Jerry?
Which of the following configurations is MOST appropriate for Jerry?
Jerry is concerned that a denial-oF. service (DoS) attack may affect his VPN Communities. He
decides to implement IKE DoS protection. Jerry needs to minimize the performance impact of
implementing this new protection. Which of the following configurations is MOST appropriate for
Jerry?
Where can a Security Administrator adjust the unit of measurement (bps, Kbps or Bps), for Check Point QoS band
Where can a Security Administrator adjust the unit of measurement (bps, Kbps or Bps), for Check
Point QoS bandwidth?
What is the best Load Sharing method for preventing this type of problem?
Problems sometimes occur when distributing IPSec packets to a few machines in a Load Sharing
Multicast mode cluster, even though the machines have the same source and destination IP
addresses. What is the best Load Sharing method for preventing this type of problem?
What is the best Load Sharing method for preventing this type of problem?
Problems sometimes occur when distributing IPSec packets to a few machines in a Load Sharing
Multicast mode cluster, even though the machines have the same source and destination IP
addresses. What is the best Load Sharing method for preventing this type of problem?
Which of the following statements is TRUE?
which FTP commands pass through the Security Gateway protecting the FTP servers?
Rachel is the Security Administrator for a university. The university’s FTP servers have old
hardware and software. Certain FTP commands cause the FTP servers to malfunction. Upgrading
the FTP servers is not an option at this time. Which of the following options will allow Rachel to
control which FTP commands pass through the Security Gateway protecting the FTP servers?
which FTP commands pass through the Security Gateway protecting the FTP servers?
Rachel is the Security Administrator for a university. The university’s FTP servers have old
hardware and software. Certain FTP commands cause the FTP servers to malfunction. Upgrading
the FTP servers is not an option at this time. Which of the following options will allow Rachel to
control which FTP commands pass through the Security Gateway protecting the FTP servers?