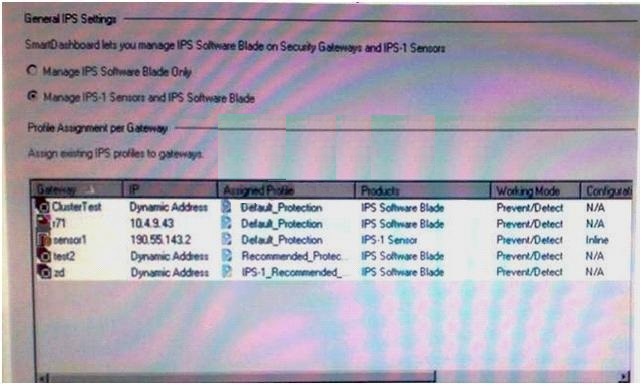
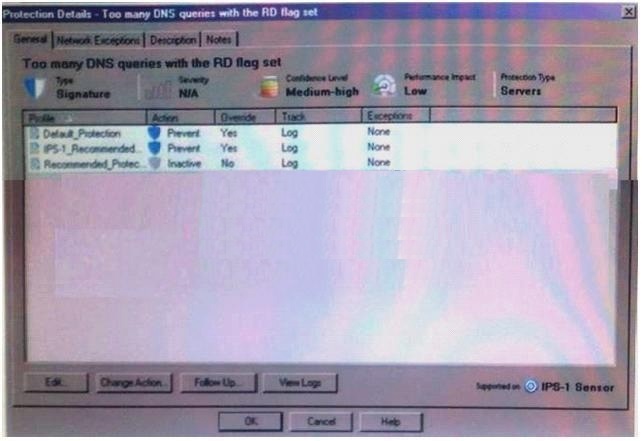
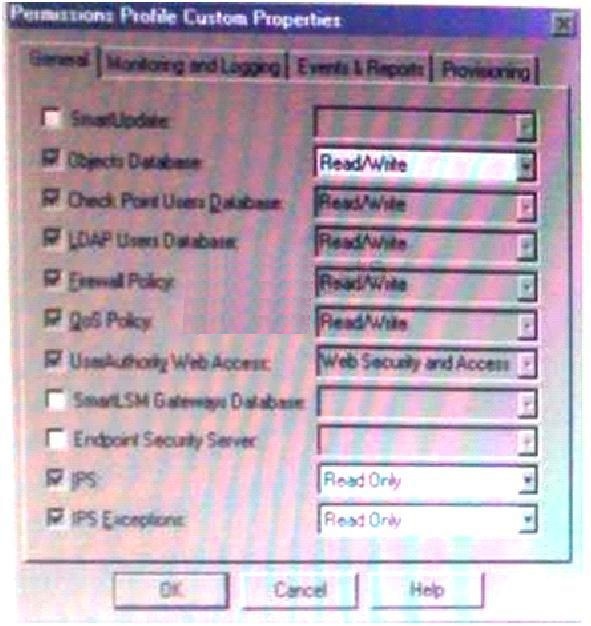
Given the following protection detailed and the enforcing gateways list, is the Tool many DNS queries with the
Which technology is responsible for assembling packet streams and passing ordered data to the protocol parsers
Which technology is responsible for assembling packet streams and passing ordered data to the
protocol parsers in IPS?
which of the following statements is TRUE?
You configure a Check Point QoS Rule Base with two rules: an H.323 rule with a weight of 10, and
the Default Rule with a weight of 10. The H.323 rule includes a per-connection guarantee of 384
Kbps. and a per-connection limit of 512 Kbps. The per-connection guarantee is for four
connections, and no additional connections are allowed in the Action properties. If traffic is passing
through the QoS Module matches both rules, which of the following statements is TRUE?
Which of the following is the default port for Management Portal?
Which of the following is the default port for Management Portal?
How is SmartWorkflow enabled?
How is SmartWorkflow enabled?
What could the following regular expression be used for in a DLP rule?
What could the following regular expression be used for in a DLP rule?
\$([0-9]*,[0-9] [0-9] [0-9]. [0-9] [0-9]
Select the best answer
Exhibit: UserA is able to create a SmartLSM Security Cluster Profile , you must select the correct justifica
Which Check Point QoS feature is used to dynamically allocate relative portions of available bandwidth?
Which Check Point QoS feature is used to dynamically allocate relative portions of available
bandwidth?
How can they solve this problem and stabilize the tunnel?
John is the MegaCorp Security Administrator, and is using Check Point R71. Malcolm is the
Security Administrator of a partner company and is using a different vendor’s product and both
have to build a VPN tunnel between their companies. Both are using clusters with Load Sharing
for their firewalls and John is using ClusterXL as a Check Point clustering solution. While trying to
establish the VPN, they are constantly noticing problems and the tunnel is not stable and then
Malcolm notices that there seems to be 2 SPIs with the same IP from the Check Point site. How
can they solve this problem and stabilize the tunnel?
how would Laura change the Default_Protection on Performance Impact Protections classified as low from inactiv
Laura notices the Microsoft Visual Basic Bits Protection is set to inactive. She wants to set the
Microsoft Visual Basic Kill Bits Protection and all other Low Performance Impact Protections to
Prevent. She asks her manager for approval and stated she can turn theses on. But he wants
Laura to make sure no high Performance Impacted Protections are turned on while changing this setting.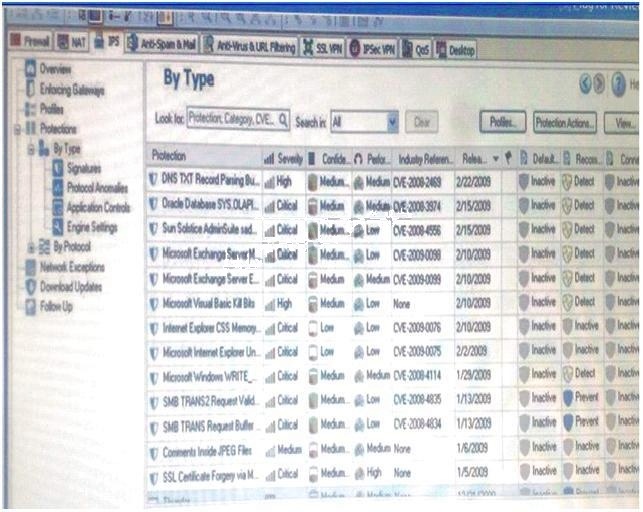
Using the out below, how would Laura change the Default_Protection on Performance Impact
Protections classified as low from inactive to prevent until meeting her other criteria?