what is one of the files you would want to analyze?
You are attempting to establish a VPN tunnel between a Check Point gateway and a 3rd party
vendor. When attempting to send traffic to the peer gateway it is failing. You look in SmartView
Tracker and see that the failure is due to “Encryption failure: no response from peer”. After
running a VPN debug on the problematic gateway, what is one of the files you would want to
analyze?
What is the best command that can be used to achieve this goal?
You want to run VPN debug that will generate both ike.elg and vpn.elg files. What is the best
command that can be used to achieve this goal?
Which of the following is the most likely cause?
In IKEView while troubleshooting a VPN issue between your gateway and a partner site you see
an entry that states “Invalid ID”. Which of the following is the most likely cause?
Which of the following is the most likely cause?
While troubleshooting a VPN issue between your gateway and a partner site you see an entry in
Smartview Tracker that states “Info: encryption failure: Different community ID: possible NAT
problem”. Which of the following is the most likely cause?
Which of the following would be the best troubleshooting step?
You are troubleshooting a VPN issue between your gateway and a partner site and you get a
drop log on your gateway that states “Clear text packet should be encrypted”. Which of the
following would be the best troubleshooting step?
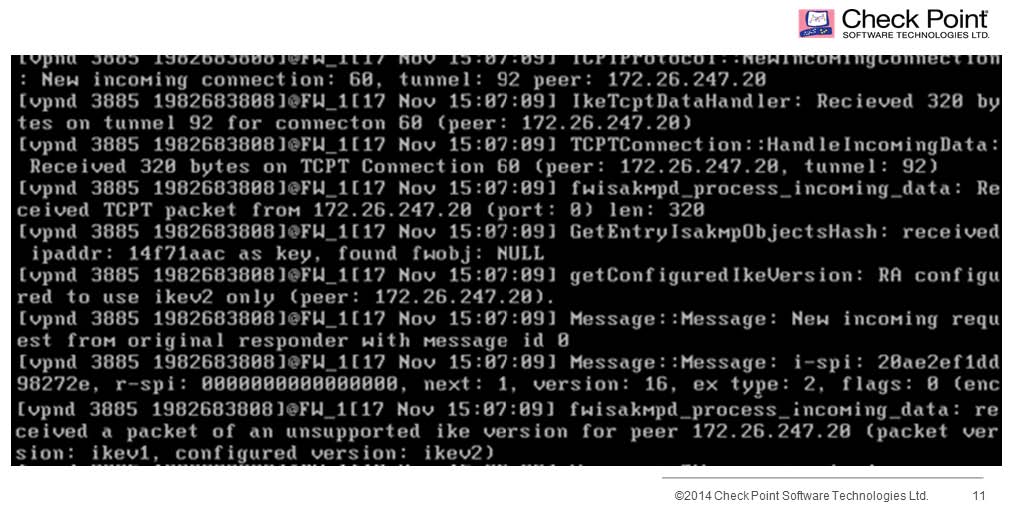
What is the most likely cause, based on the options below?
Your company has recently decided to allow remote access for clients. You find that no one is
able to connect, although you are confident that your rule set and remote access community has
been defined correctly. What is the most likely cause, based on the options below? You have the
following debug file:
What is the most likely cause of this issue?
You are experiencing an issue where Endpoint Connect client connects successfully however, it
disconnects every 20 seconds. What is the most likely cause of this issue?
In a VPN configuration, the following mode can be used to increase throughput by bypassing firewall enforcemen
In a VPN configuration, the following mode can be used to increase throughput by bypassing
firewall enforcement.
which of the following debug logs is essential to understanding the issue?
When VPN user-based authentication fails, which of the following debug logs is essential to
understanding the issue?
what is the most likely cause?
In Tracker you are troubleshooting a VPN issue between your gateway and a partner site and
you get a drop log that states “No proposal chosen” what is the most likely cause?