To reduce the effectiveness of traffic sniffing inside the LAN, internal users should have the _______ install
To reduce the effectiveness of traffic sniffing inside the LAN, internal users should have the
_______ installed in their desktop.
Which of the following selections lists the three security components essential to guaranteeing the security o
Which of the following selections lists the three security components essential to guaranteeing the
security of network connections?
If you wish to move any Secure Client files to another directory.
If you wish to move any Secure Client files to another directory.
Which option should you choose?
You are installing Check Point VPN-1/Firewall-1 on a Windows NT platform. The machine will only
be used to install policies on Enforcement Modules. No other machine in the network will perform
the function. While installing the following installation screen of “VPN-1/Firewall-1 Enterprise
Product” appears.
The screen shows “Please select the VPN-1/Firewall-1 Product Type you are about to install”.
Which option should you choose?
Choose the one phrase below that best describes Patrick’s proposal.
Patrick has been hired to devise a security solution for a company that provides in-home care.
Visiting Nurses use Internet connections to transmit confidential patient data to a database server
located at the corporate office.
The visiting Nurses at the remote locations must have a secure connection to the database server
to protect patient confidentiality. The database server itself must also be protected from external
threats. The human resources department would like to have access to information about their
Nurses access the database server. Accounting would like to offer Nurses the option of submitting
their time sheets from remote locations, provided this can be accomplished in a secure manner.
Patrick proposes installing Check Point VPN/Firewall-1 at the perimeter of the corporate LAN. He
recommends installing Check Point Secure Client in the laptops used by the visiting Nurses.
Patrick suggests rules allowing only client-authenticated traffic to the accounting server. To reduce
resource consumption, Patrick advises his customer not to log any traffic passing through the
Enforcement Module. Choose the one phrase below that best describes Patrick’s proposal.
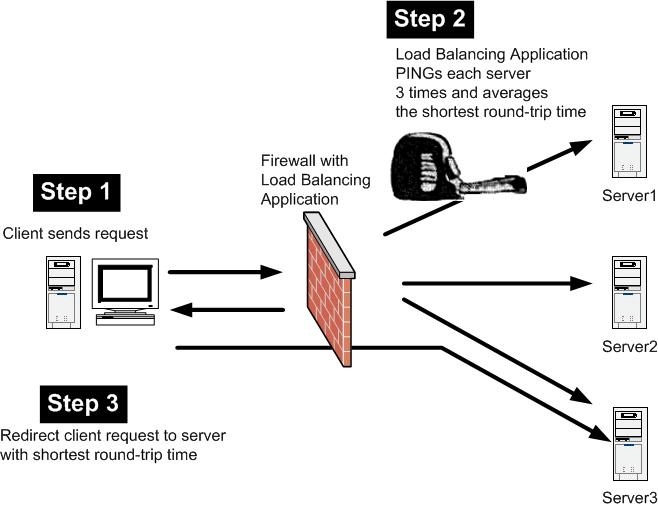
The ________ load balancing algorithm uses ICMP to determine the shortest time to and from the firewall…
Re-install the Security Policy.
When using the Load Measuring Agent, you can add a new server without stopping and starting
anything. Review the steps listed below and select the response demonstrating the correct order
for adding a new server for Load Measuring.
1. Install the agent on the server.
2. Add the object for the new server to the existing rule in the Rule Base.
3. Re-install the Security Policy.
What is the purpose of cplic check?
What is the purpose of cplic check?
If you have modified your network configuration by removing the firewall adapters, you can reinstall these ada
If you have modified your network configuration by removing the firewall adapters, you can
reinstall these adapters by reinstalling Secure Client.
What are the MINIMUM elements Hector must configure to complete Enforcement Module installation?
Hector is a security administrator for a large, global enterprise that is preparing to implement VPN-1/Firewall-1. In the first phase of the rollout all Enforcement Modules will be installed at a central
warehouse before being shipped to the final sites and final set-up. Site-specific information is not
available to the warehouse installer. What are the MINIMUM elements Hector must configure to
complete Enforcement Module installation?