how would you verify that the IP addresses and port numbers are correctly referencing the CA and LDAP Servers?
CRL lookups from VPN-1/Firewall-1 modules, or the SecuRemote Server, to the LDAP Server.
When problems occur with CRL verification, how would you verify that the IP addresses and port
numbers are correctly referencing the CA and LDAP Servers?
What are the disadvantages of Shared Secret Key encryption?
What are the disadvantages of Shared Secret Key encryption?
which if the following?
An external UFP server, can perform which if the following?
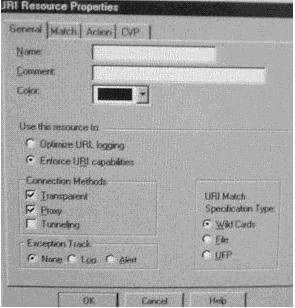
Which of the following statements best describe the purpose of the Transparent Connection method shown below i
When SecuRemote Client and Server key exchange occurs, the user will NOT be re-authenticated even if the Passw
When SecuRemote Client and Server key exchange occurs, the user will NOT be re-authenticated
even if the Password Expires After timer on the SecuRemote Server has not expired.
In the event that an unauthorized user attempts to compromise a valid Secure Client connection, the Secure Cli
In the event that an unauthorized user attempts to compromise a valid Secure Client connection,
the Secure Client machine can remain protected by?
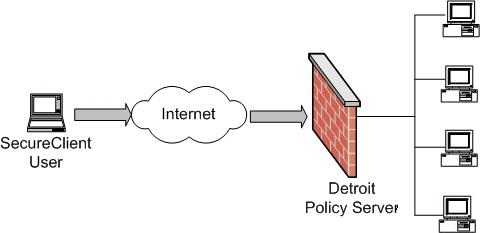
The Secure Client user tries to connect to a host in Detroit’s domain. Because Detroit is a Policy Serve
what version of firewall kernel a customer is using?
How do determine what version of firewall kernel a customer is using?
When you select the Pre-Shared Secret check box in the IKE Properties window:
When you select the Pre-Shared Secret check box in the IKE Properties window:
What is the Check Point recommended sequence for performing the following operations?
What is the Check Point recommended sequence for performing the following operations?
1. Install operating system.
2. Finish hardening the operating system.
3. Patch operating system.
4. Install firewall.
5. Patch firewall.