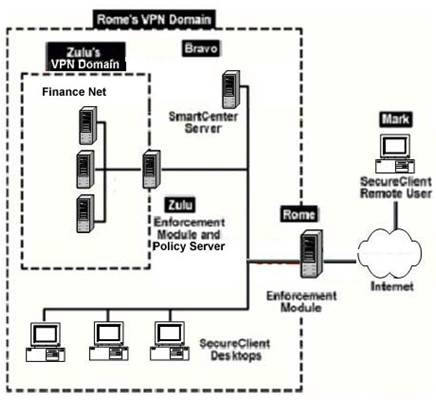
When this connection is made, Zulu will attempt to load its Desktop Policy on the SecureClient remote user, an
Which VPN-1/FireWall-1 Security Servers provide Content Security?
Which VPN-1/FireWall-1 Security Servers provide Content Security? (Choose three)
which of the following from HTML?
In VPN-1/FireWall-1, Security Administrators can define URI Resource Properties to strip which of
the following from HTML? (Choose three)
Which VPN-1/FireWall-1 Security Server does NOT perform authentication?
Which VPN-1/FireWall-1 Security Server does NOT perform authentication?
Encryption is the transformation of readable data into an unreadable form called:
Encryption is the transformation of readable data into an unreadable form called:
The Check Point SecureClient Packaging Tool allows System Administrators to:
Choose three. The Check Point SecureClient Packaging Tool allows System Administrators to:
Which of the following is TRUE of the relationship between the RemoteAccess VPN Community and the Security Pol
Which of the following is TRUE of the relationship between the RemoteAccess VPN Community
and the Security Policy Rule Base?
Which of the following statements, about Hybrid Ike, are FALSE?
Which of the following statements, about Hybrid Ike, are FALSE? Choose two.
Passwords are shared in memory instead if being written to disk, and are erased upon reboot.
Users must enter a username and a password on the first attempt while using Secure Client
Authentication window to connect to a site. Passwords are shared in memory instead if being
written to disk, and are erased upon reboot.
The IKE encryption scheme encrypts the original TCP and IP headers along with the packet data.
The IKE encryption scheme encrypts the original TCP and IP headers along with the packet data.