which would be the best configuration to protect from a traffic hijack attempt?
You need to verify the effectiveness of your IPS configuration for your Web server farm. You have
a colleague run penetration tests to confirm that the Web servers are secure against traffic hijacks.
Of the following, which would be the best configuration to protect from a traffic hijack attempt?
Which command would stop the root level MDS but leave all of the CMA’s still running?
Which command would stop the root level MDS but leave all of the CMA’s still running?
Which SmartConsole application should you use to check these objects and rules?
A marketing firm’s networking team is trying to troubleshoot user complaints regarding access to
audio-streaming material from the Internet. The networking team asks you to check the object and
rule configuration settings for the perimeter Security Gateway. Which SmartConsole application
should you use to check these objects and rules?
URL Filtering Policy can make exceptions for specific sites by being enforced…
URL Filtering Policy can make exceptions for specific sites by being enforced…
how many management modules can be configured for a particular customer?
In Multi-Domain Management with Provider-1 R70, how many management modules can be
configured for a particular customer?
How would you check this using SmartConsole?
A third shift Security Administrator configured and installed a new Security Policy early this
morning. When you arrive, he tells you that he has been receiving complaints that Internet access
is very slow. You suspect the Security Gateway virtual memory might be the problem. How would
you check this using SmartConsole?
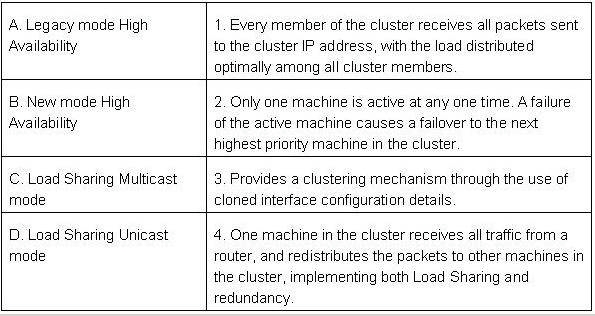
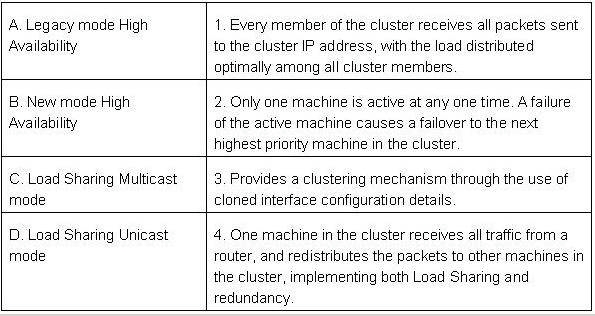
Match the ClusterXL Modes with their configurations
Match the ClusterXL Modes with their configurations
What CLI command is used to set a Leading VIP Interface?
What CLI command is used to set a Leading VIP Interface?