Which Check Point QoS feature marks the ToS byte in the IP header?
Which Check Point QoS feature marks the ToS byte in the IP header?
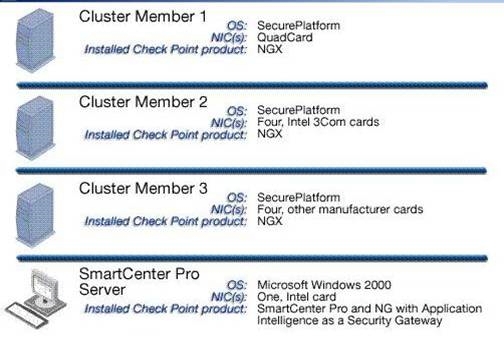
For your cluster, you plan to use three machines with the following configurations…
You are preparing computers for a new ClusterXL deployment. For your cluster, you plan to use
three machines with the following configurations: Cluster Member 1: OS: SecurePlatform, NICs:
QuadCard, memory: 512 MB, Security Gateway, version: VPN-1 NGX R65 and primary
SmartCenter Server installed, version: VPN-1 NGX R65 Cluster Member 2: OS: SecurePlatform,
NICs: 4 Intel 3Com, memory: 512 MB, Security Gateway only, and version: VPN-1 NGX R65
Cluster Member 3: OS: SecurePlatform, NICs: 4 other manufacturers, memory: 256 MB, Security
Gateway only, and version: VPN-1 NGX R65
Are these machines correctly configured for a ClusterXL deployment?
For your cluster, you plan to use three machines with the following configurations…
You are preparing computers for a new ClusterXL deployment. For your cluster, you plan to use
three machines with the following configurations: Cluster Member 1: OS: SecurePlatform, NICs:
QuadCard, memory: 512 MB, Security Gateway, version: VPN-1 NGX R65 and primary
SmartCenter Server installed, version: VPN-1 NGX R65 Cluster Member 2: OS: SecurePlatform,
NICs: 4 Intel 3Com, memory: 512 MB, Security Gateway only, and version: VPN-1 NGX R65
Cluster Member 3: OS: SecurePlatform, NICs: 4 other manufacturers, memory: 256 MB, Security
Gateway only, and version: VPN-1 NGX R65
When configuring a Web Application for SSL VPN remote access, you have given the following definition for the
When configuring a Web Application for SSL VPN remote access, you have given the following
definition for the application along with its protection level.
which of the following statements is NOT true?
When synchronizing clusters, which of the following statements is NOT true?
which of the following statements is NOT true?
When synchronizing clusters, which of the following statements is NOT true?
which would be the best configuration to protect from a traffic hijack attempt?
You need to verify the effectiveness of your IPS configuration for your Web server farm. You have
a colleague run penetration tests to confirm that the Web servers are secure against traffic hijacks.
Of the following, which would be the best configuration to protect from a traffic hijack attempt?
Where is it necessary to configure historical records in SmartView Monitor to generate Express reports in Even
Where is it necessary to configure historical records in SmartView Monitor to generate Express
reports in Eventia Reporter?
Where is it necessary to configure historical records in SmartView Monitor to generate Express reports in Even
Where is it necessary to configure historical records in SmartView Monitor to generate Express
reports in Eventia Reporter?