which member is the standby machine?
In New Mode HA, the internal cluster IP VIP address is 10.4.8.3. The internal interfaces on two
members are 10.4.8.1 and 10.4.8.2. Internal host 10.4.8.108 Pings 10.4.8.3, and receives replies.
The following is the ARP table from the internal Windows host 10.4.8.108: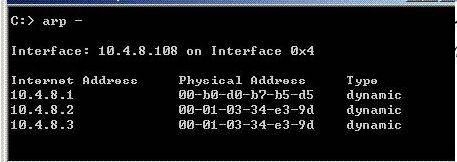
According to the output, which member is the standby machine?
Which Check Point product is used to create and save changes to a Log Consolidation Policy?
Which Check Point product is used to create and save changes to a Log Consolidation Policy?
Which Check Point product is used to create and save changes to a Log Consolidation Policy?
Which Check Point product is used to create and save changes to a Log Consolidation Policy?
What is the best tool to produce a report which represents historical system information?
What is the best tool to produce a report which represents historical system information?
Which of the following would NOT be a reason for beginning with a fresh installation of VPN-1 NGX R65, instead
Which of the following would NOT be a reason for beginning with a fresh installation of VPN-1
NGX R65, instead of upgrading a previous version to VPN-1 NGX R65?
Which of the following would NOT be a reason for beginning with a fresh installation of VPN-1 NGX R65, instead
Which of the following would NOT be a reason for beginning with a fresh installation of VPN-1
NGX R65, instead of upgrading a previous version to VPN-1 NGX R65?
which folder(s)?
To clean the system of all events, you should delete the files in which folder(s)?
How do you block some seldom-used FTP commands, such as CWD, and FIND from passing through the Gateway?
How do you block some seldom-used FTP commands, such as CWD, and FIND from passing
through the Gateway?
A . Use FTP Security Server settings in SmartDefense.
How can they solve this problem and stabilize the tunnel?
John is the Mega Corp Security Administrator, and is using Check Point R70. Malcolm is the
Security Administrator of a partner company and is using a different vendor’s product and both
have to build a VPN tunnel between their companies. Both are using clusters with Load Sharing
for their firewalls and John is using ClusterXL as a Check Point clustering solution. While trying to
establish the VPN, they are constantly noticing problems and the tunnel is not stable and then
Malcolm notices that there seems to be 2 SPIs with the same IP from the Check Point site. How
can they solve this problem and stabilize the tunnel?


