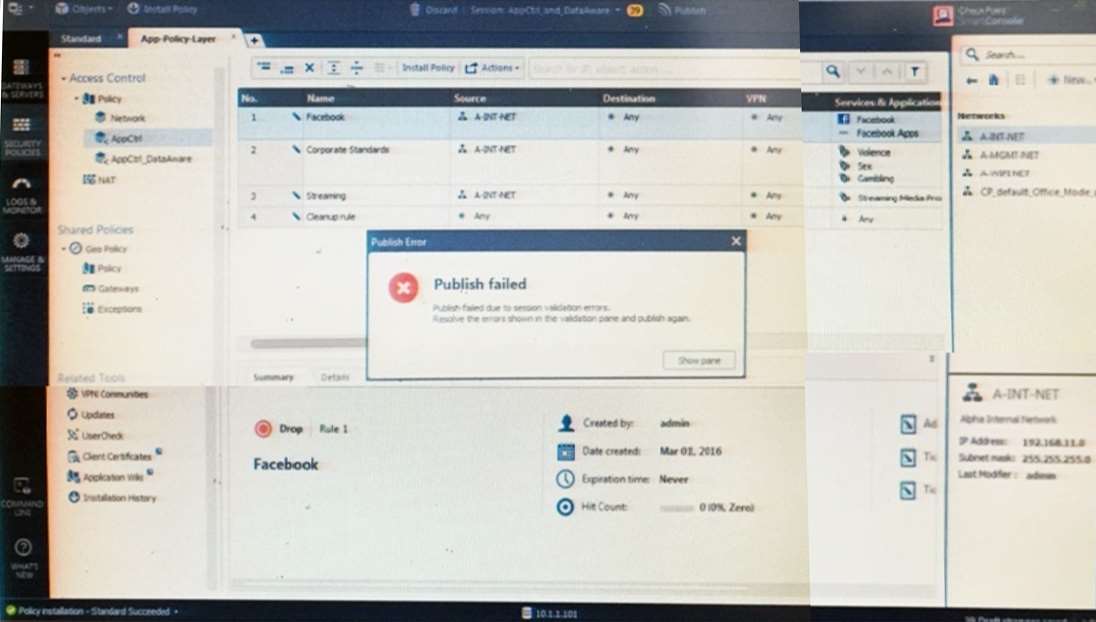
To optimize Rule Base efficiency the most hit rules should be where?
To optimize Rule Base efficiency the most hit rules should be where?
which blade will she enable to achieve her goal?
Harriet wants to protect sensitive information from intentional loss when users browse to a specific URL: https://
personal.mymail.com, which blade will she enable to achieve her goal?
which action would you choose?
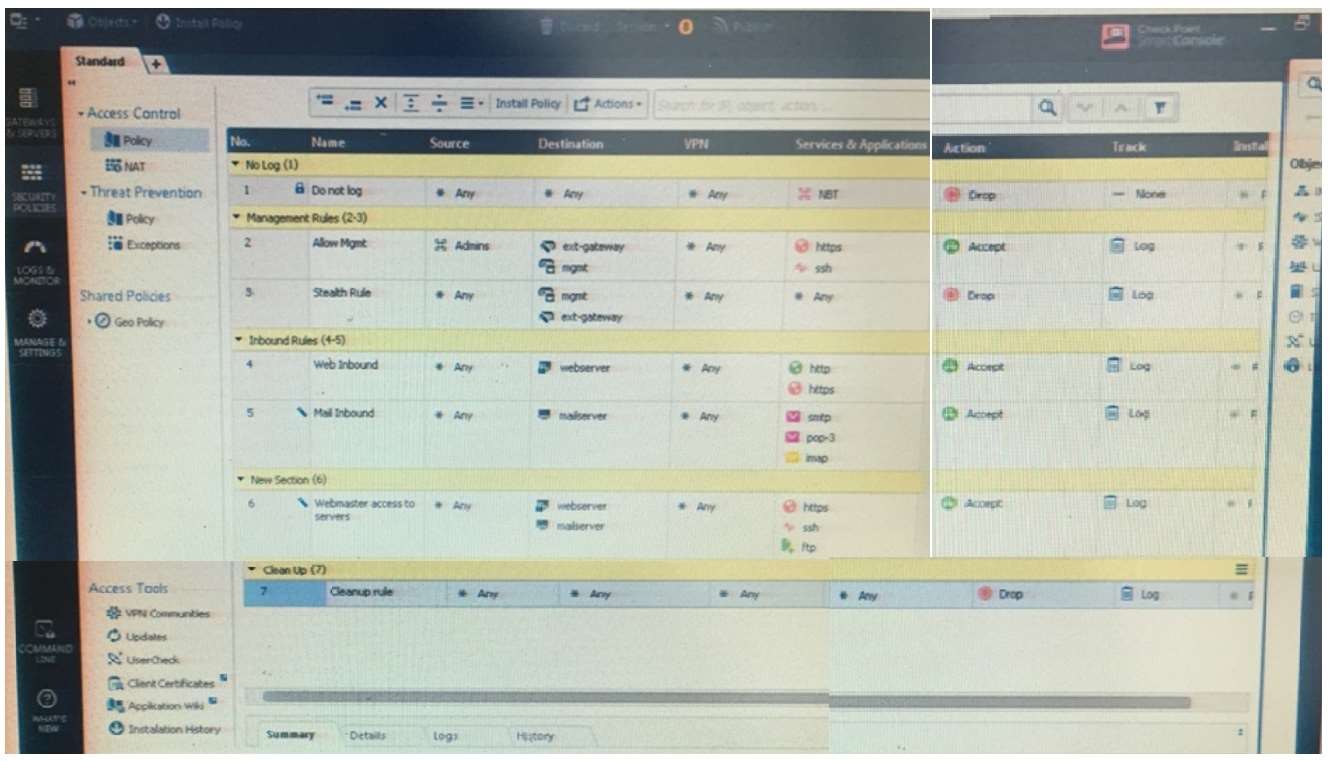
You are working with multiple Security Gateways enforcing an extensive number of rules. To simplify security
administration, which action would you choose?
Where can the administrator check for more information …
What is the likely cause for this?
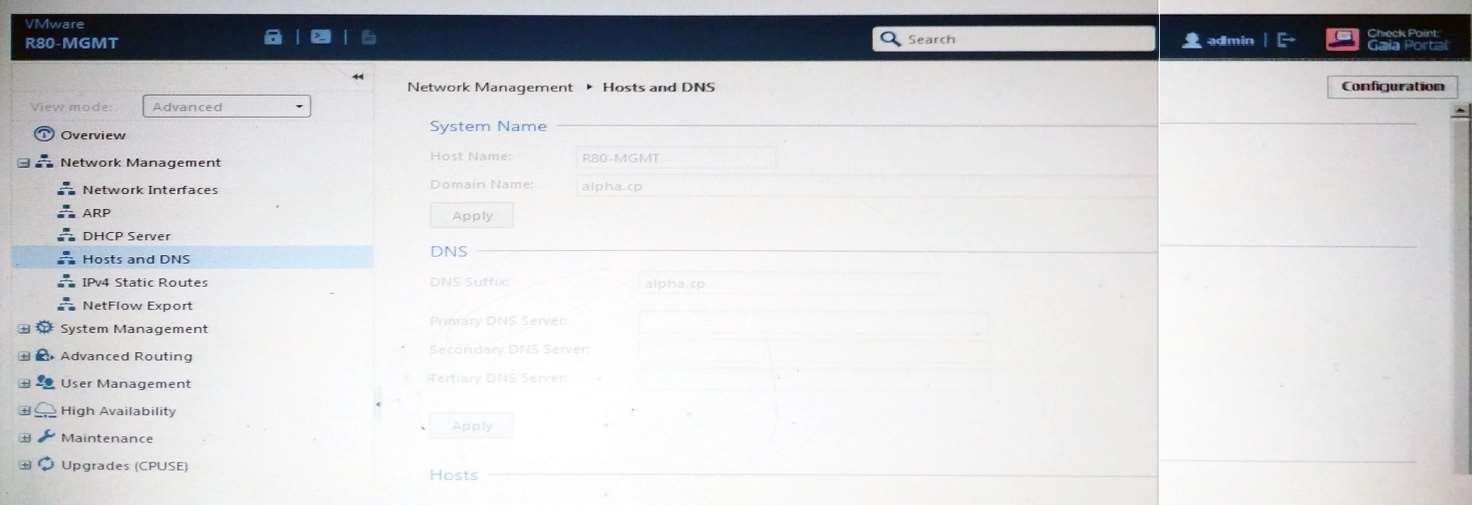
ALPHA Corp has a new administrator who logs into the Gaia Portal to make some changes. He realizes that
even though he has logged in as an administrator, he is unable to make any changes because all configuration
options are greyed out as shown in the screenshot image below. What is the likely cause for this?
What can we infer about the recent changes made to the …
Which command should be use in CLI?
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server. He can
do this via WebUI or a via CLI. Which command should be use in CLI? Choose the correct answer.
Which of the following is an identity acquisition metho…
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active
Directory users and computers?
What is the order of NAT priorities?
What is the order of NAT priorities?
What is the MOST likely reason?
You have enabled “Full Log” as a tracking option to a security rule. However, you are still not seeing any data
type information. What is the MOST likely reason?