which techniques are used to control access?
When setting up the disk and file structures for user data, which techniques are used to control
access? Select TWO.
Which data sources can be used by Capacity Advisor for this analysis?
What are the benefits for configuring all six vPars in a single nPar versus splitting the vPars across two nPa
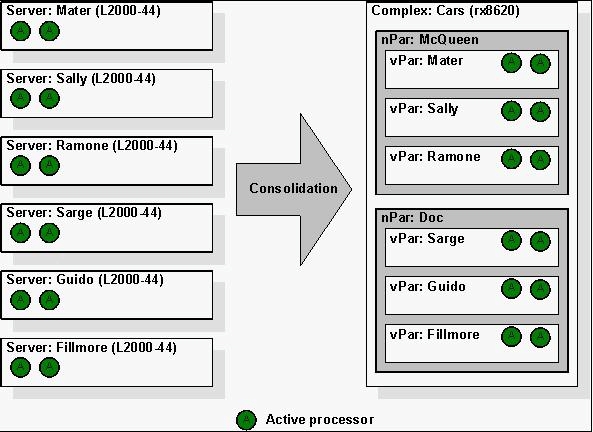
A customer is consolidating six L2000 servers to Virtual Partitions as shown in the diagram. Global
Workload Manager is used to allocate resources to each vPar based on demand.
An alternate approach for this consolidation would have been creating a single nPartition for all six
of the Virtual Partitions. What are the benefits for configuring all six vPars in a single nPar versus
splitting the vPars across two nPars?
What two areas need to be considered prior to implementing such a solution?
Encrypted file transfers between systems provide better data integrity and confidentiality than “in
the clear” transfers. What two areas need to be considered prior to implementing such a solution?
Select two.
how many processors are using Temporary Instant Capacity?
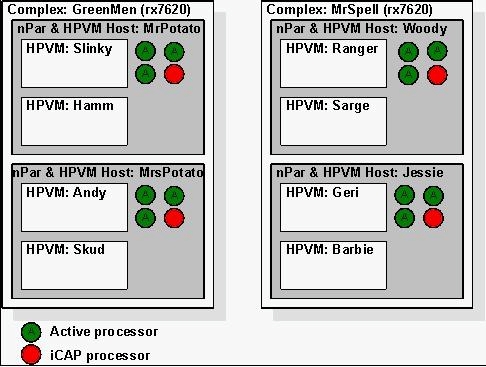
A customer has migrated four L2000 servers to Integrity Virtual Machines on an rx7620 that has
eight processors. Five of the processors are active, and three are inactive Instant Capacity
processors. The Integrity Virtual Machines are managed by Global Workload manager and
Temporary Instant Capacity is used to activate the inactive processors when needed.
Where should the icod_stat command be executed to determine how many processors are using
Temporary Instant Capacity?
What are two of the vulnerabilities that are introduced?
A backup system disk copy is missing. What are two of the vulnerabilities that are introduced?
Select two.
how will HP Integrity Essentials Global Workload Manager change the resource allocation when the workload move
If the Sid vPar fails, HP Serviceguard moves the workload to the Bullseye vPar. Bullseye and
Hannah each have a gWLM Own Borrow policy with a minimum of one CPU, owns three CPUs,
and a maximum of seven CPUs. TiCAP processors are configured to be utilized by gWLM.
If Bullseye’s and Hannah’s workload demands are being met with three CPUs, how will HP
Integrity Essentials Global Workload Manager change the resource allocation when the workload
moves?
Which shared resource domain or domains need to be created in this environment?
Using drag and drop, order the required steps to activate an Instant Capacity CPU in the Hannah vPar
Which feature of OpenVMS allows verification of the integrity and authenticity of product installation kits?
Which feature of OpenVMS allows verification of the integrity and authenticity of product
installation kits?