What is the security significance of a missing audit log file?
What is the security significance of a missing audit log file?
which items?
HP Integrity Virtual Machines can run in which items? (Select two.)
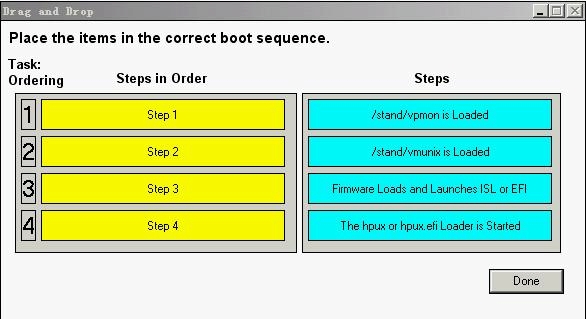
Using drag and drop, arrange the steps in the correct boot sequence for booting the first Virtual Partition (v
what should happen next?
The authenticity of a patch to a business-critical software package has been verified. From a
security point of view, what should happen next?
How can a single user be prevented from viewing or changing a system in the VSE Management Suite and the HP Sy
How can a single user be prevented from viewing or changing a system in the VSE Management
Suite and the HP Systems Insight Manager management domain?
Which command displays whether a server is currently consuming Temporary Instant Capacity?
Which command displays whether a server is currently consuming Temporary Instant Capacity?
what actions prevent the account from being used while still permitting subsequent backup and restoration of d
When an account is no longer in use, what actions prevent the account from being used while still
permitting subsequent backup and restoration of data with original security attributes such as
ownership?
What is the maximum CPU resource that can be utilized by the Virtual Machine?
A customer has an Integrity server with four cores with Integrity Virtual Machines installed. A
virtual machine configured with two virtual processors and an entitlement of 25% is running on the
server. What is the maximum CPU resource that can be utilized by the Virtual Machine?
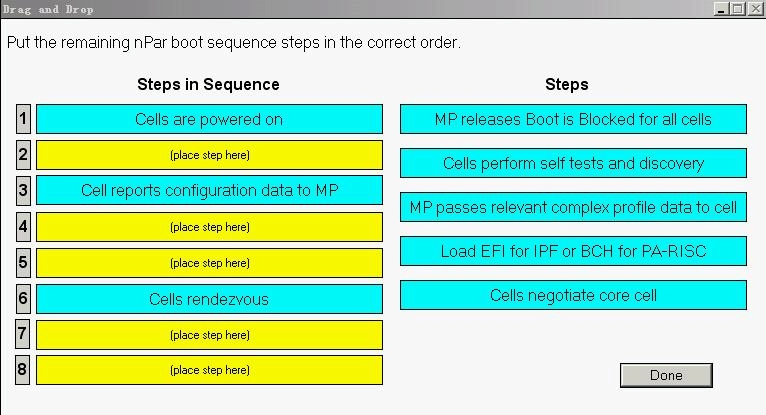
Using drag and drop, arrange the steps in the correct boot sequence for an nPartition.
What are three valid options for an ACL identifier ACE?
What are three valid options for an ACL identifier ACE? Select three.