What is one reason for this?
OpenVMS systems are highly resistant to buffer overflow attacks. What is one reason for this?
Which approach ensures each department receives their fair share of the server, yet also allows other departme
A university implements an Integrity server solution with VSE. Three departments have combined
their money to purchase this server and have configured three vPars; one for each department.
There are Instant Capacity processors in the system. Which approach ensures each department
receives their fair share of the server, yet also allows other departments use of unused CPU
cycles?
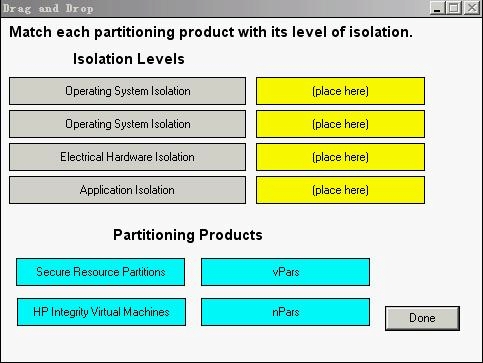
Using drag and drop, match each partitioning product with its isolation level.
Which VSE approach meets these requirements and minimizes OS maintenance?
A customer has several small mission critical Oracle databases where each requires one to two
processors. In development, it is noted that the database instances stack together without
interactions.
They want to implement an rx4640 Integrity server solution that provides the ability to dynamically
shift processor and memory resources between the database instances.
Which VSE approach meets these requirements and minimizes OS maintenance?
What is the most likely cause and fix?
You have installed, configured, and booted up in a Virtual Partition environment and thus have
several vPars up and running. However, you have found that the bootup times for the vPars
compared to an nPar bootup is significantly longer. What is the most likely cause and fix?
Why does an OpenVMS system with both internal and external users need to be protected by a hardware firewall?
Why does an OpenVMS system with both internal and external users need to be protected by a
hardware firewall?
How can this problem be resolved?
An administrator attempts to run an HP Systems Insight Manager command line tool on the
system jacquot.fc.hp.com. The following error message is returned:
Ssh Operation failed for node: jacquot.fc.hp.com. SshAuthenication Failed.
How can this problem be resolved?
Which file will cause auditing messages to be sent to the security operator consoles?
User PHILBY, UIC [SIS,PHILBY], holds rights identifiers LONDON and CAMBRIDGE and
executes the command TYPE *.* in a directory containing the following files. Which file will cause
auditing messages to be sent to the security operator consoles?
What could cause this?
A user named johnny has been managing three systems for several months with Virtualization
Manager. However, one of the three systems disappeared from Virtualization Manager, yet the
system is still shown in HP Systems Insight Manager. What could cause this?
which image another process is executing?
How can a system manager identify which image another process is executing?