You need to enable the appropriate remote access for the members of the Managers and Operations groups while r
You are the network administrator for your company. The network consists of a single Active Directory domain. The functional level of the domain is Windows Server 2003. The domain contains a Windows Server 2003 computer named Server1 that is running Routing and Remote Access. The domain contains a universal group named Managers and a global group named Operations. User accounts in the Managers group require remote access between the hours of 8:00 A.M. and 8:00 P.M. User accounts in the Operations group require remote access 24 hours per day. You configure a remote access policy on Server1 named RA_Managers with the appropriate settings for the Managers group, and you configure a second remote access policy named RA_Operations on Server1 with the appropriate settings for the Operations group. The default remote access policies on Server1 remain unmodified. Members of the Managers group report that they can establish a remote access connection to Server1, but members of the Operations group report that they cannot establish a remote access connection to Server1. You open the Routing and Remote Access administrative tool and note that the remote access policies are in the order presented in the following table.
You need to enable the appropriate remote access for the members of the Managers and Operations groups while restricting remote access to all other users.
What should you do?
You need to accomplish this task by using the minimum amount of administrative effort and while minimizing the
You are the network administrator for your company. The network consists of a single Active Directory domain. The functional level of the domain is Windows Server 2003. The domain contains an organizational unit (OU) named Servers that contains all of the company’s Windows Server 2003 resource servers.
The domain also contains an OU named Workstations that contains all of the company’s Windows XP Professional client computers. You configure a baseline security template for resource servers named Server.inf and a baseline security template for client computers named Workstation.inf.
The Server.inf template contains hundreds of settings, including file and registry permission settings that have inheritance propagation enabled. The Workstation.inf template contains 20 security settings, none of which contain file or registry permissions settings.
The resource servers operate at near capacity during business hours. You need to apply the baseline security templates so that the settings will be periodically enforced. You need to accomplish this task by using the minimum amount of administrative effort and while minimizing the performance impact on the resource servers.
What should you do?
You need to ensure that members of the Cert Approvers group can approve pending enrollment requests for a Key
You are the network administrator for your company. The network consists of a single Active Directory domain. All computers on the network are members of the domain. The domain contains a Windows Server 2003 computer named Server1. You are planning a public key infrastructure (PKI) for the company.
You want to deploy an enterprise certification authority (CA) on Server1. You create a new global security group named Cert Approvers. You install an enterprise CA and configure the CA to issue Key Recovery Agent certificates. The company’s written security policy states that issuance of a Key Recovery Agent certificate requires approval from a member of the Cert Approvers group.
All other certificates must be issued automatically. You need to ensure that members of the Cert Approvers group can approve pending enrollment requests for a Key Recovery Agent certificate.
What should you do?
You need to configure DNSSRV1 so that it complies with company requirements and restrictions
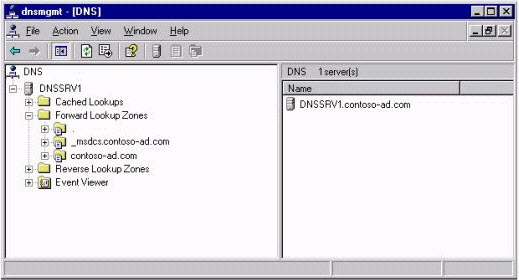
You are the systems engineer for Contoso, Ltd. The network consists of a single Active Directory domain named contoso-ad.com. All servers run Windows Server 2003. A Windows Server 2003 computer named DNSSRV1 functions as the internal DNS server and has zones configured as shown in the exhibit.
The network is not currently connected to the Internet. The company maintains a separate network that contains publicly accessible Web and mail servers. These Web and mail servers are members of a DNS domain named contoso.com.
The contoso.com zone is hosted by a UNIX-based DNS server named UNIXDNS, which is running the latest version of BIND. The company plans to allow users of the internal network to access Internet-based resources. The company’s written security policy states that resources located on the internal network must never be exposed to the Internet.
The written security policy also states that the internal network’s DNS namespace must never be exposed to the Internet. To meet these requirements, the design specifies that all name resolution requests for Internet-based resources from computers on the internal network must be sent from DNSSRV1.
The current design also specifies that UNIXDNS must attempt to resolve any name resolution requests before sending them to name servers on the Internet. You need to plan a name resolution strategy for Internet access. You need to configure DNSSRV1 so that it complies with company requirements and restrictions.
What should you do?
Exhibit:
Which two actions should you take? (Each correct answer presents part of the solution
You are the security analyst for your company. The company’s written security policy does not allow direct dial-in connections to the network. During a routine security audit, you discover a Windows Server 2003 server named Server1 that has a modem installed and is connected to an outside analog phone line.
You investigate and discover that Server1 is also running Routing and Remote Access and is used by the sales department. The modem supports the caller ID service. This remote access connection is used by an application at a partner company to upload product and inventory information to Server1. Each day at midnight, the partner application connects to Server1 and uploads the information.
The connection never lasts longer than 30 minutes. The application is currently using the sales manager’s domain user account to make the connection. The partner application does not support incoming connections. The partner company has no plans to update this application to support your written security policy, and the sales department requires this updated product and inventory information to be available each morning.
Company management directs you to design a solution that provides the highest level of security for this connection until a more secure solution can be developed by the two companies. You need to design and implement a solution that will ensure that only the partner’s application can connect to your network over the dial-up connection.
Your solution must prevent the connection from being used by unauthorized users, and it must allow only the minimum amount of access to the network.
Which two actions should you take? (Each correct answer presents part of the solution. Choose two.)
You need to capture the authentication event details on the domain controller in the Bogota office…
You are the network administrator for your company. The network consists of a single Active Directory domain. The company has a main office in San Francisco and branch offices in Paris and Bogota. Each branch office contains a Windows Server 2003 domain controller.
All client computers run Windows XP Professional. Users in the Bogota office report intermittent problems authenticating to the domain.
You suspect that a specific client computer is causing the problem.
You need to capture the authentication event details on the domain controller in the Bogota office so that you can find out the IP address of the client computer that is the source of the problem.
What should you do?
You need to identify the cause of the failure and update your test plan
You are a network administrator for your company. You need to test a new application. The application requires two processors and 2 GB of RAM. The application also requires shared folders on the application server and requires the installation of software on the client computers. You create the test plan.
You assemble a server in the test lab. You install Windows Server 2003, Web Edition on the server. You install the application on the server. You install the client software components for the application on 20 client computers in the test lab. You test the application. You discover that only some of the client computers can run the application.
You turn off the client computers that ran the application successfully, and you test again. The client computers that failed in the first test now run the application successfully. You need to identify the cause of the failure and update your test plan.
What should you do?
You need to create one or more Group Policy objects (GPOs) to implement the security settings
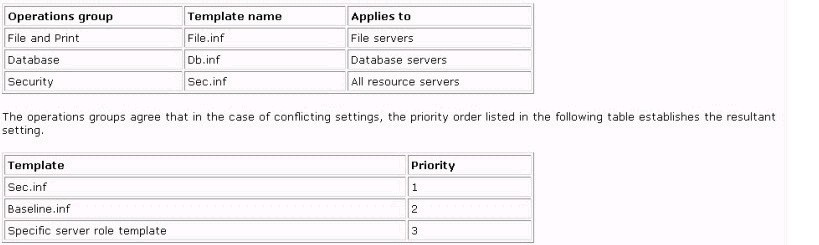
You are the network administrator for your company. All servers run Windows Server 2003. You configure a baseline security template named Baseline.inf. Several operations groups are responsible for creating templates containing settings that satisfy operational requirements. You receive the templates shown in the following table.
You need to create one or more Group Policy objects (GPOs) to implement the security settings. You want to minimize the amount of administrative effort required when changes are requested by the various operations groups. What should you do?
You need to ensure that unnecessary services are always disabled on the Web servers
You are a network administrator for your company. The network consists of a single Active Directory domain. The network contains 80 Web servers that run Windows 2000 Server. The IIS Lockdown Wizard is run on all Web servers as they are deployed.
Your company is planning to upgrade its Web servers to Windows Server 2003. You move all Web servers into an organizational unit (OU) named Web Servers. You are planning a baseline security configuration for the Web servers. The company’s written security policy states that all unnecessary services must be disabled on servers.
Testing shows that the server upgrade process leaves the following unnecessary services enable* SMTP Telnet
Your plan for the baseline security configuration for Web servers must comply with the written security policy. You need to ensure that unnecessary services are always disabled on the Web servers.
What should you do?