You need to develop a plan that will meet the requirements of Adventure Works employees and the security requi
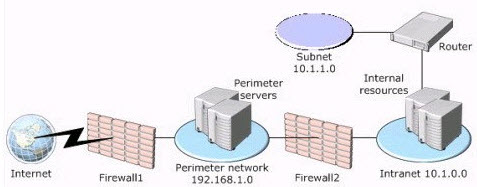
You are a network administrator for Alpine Ski House. The network consists of a single Active Directory domain. The network contains 50 Windows Server 2003 computers and 200 Windows XP Professional computers. Alpine Ski House does not use wireless networking. The network at Alpine Ski House is shown in the exhibit.
Alpine Ski House enters into a strategic partnership with Adventure Works. Under the strategic partnership, Adventure Works will regularly send employees to Alpine Ski House. Your design team interviews Adventure Works administrators and discovers the following:
Adventure Works employees require access to the Internet to retrieve e-mail messages and to browse the Internet. Adventure Works employees do not need access to the internal network at Alpine Ski House.
Adventure Works employees all have portable computers that run Windows XP Professional, and they use a wireless network in their home office. The wireless network client computers of Adventure Works employees must be protected from Internet-based attacks.
Adventure Works sends you a wireless access point that its employees will use to access the Internet through your network. You are not allowed to change the configuration of the wireless access point because any change will require changes to all of the wireless client computers.
You need to develop a plan that will meet the requirements of Adventure Works employees and the security requirements of Alpine Ski House. Your solution must be secure and must minimize administrative effort.
What should you do?
Exhibit:
What should you do?
You are a network administrator for your company. The network contains four Windows Server 2003 computers configured as a four-node server cluster.
Each cluster node is the preferred owner of a clustered instance of Microsoft SQL Server 2000, and each cluster node is configured as a possible owner of all other instances of SQL Server.
All nodes have identically configured hardware. All four nodes operate at a sustained 70 percent CPU average. You add a server that has identically configured hardware to the cluster as a fifth node. You want each SQL Server instance to continue operating at the same level of performance in the event of a single node failure.
What should you do?
You need to improve the response time of the application
You are the network administrator for your company. All servers run Windows Server 2003. The network contains two Web servers named Server1 and Server2 and three application servers named Server3, Server4, and Server5. All five servers have similar hardware. The servers are configured as Network Load Balancing clusters, as shown in the exhibit.
A Web services application hosted on Server1 and Server2 communicates to application components hosted on Server3, Server4, and Server5 by using the IP address 10.1.20.11. The application is designed to be stateless. The Network Load Balancing settings for each server are listed in the following table.
Host Filtering mode Host priority Affinity Load Server1 Multiple Single Equal Server2 Multiple Single Equal Server3 Multiple Single Equal
You need to improve the response time of the application.
What should you do?
Exhibit:
You need to create a plan to identify the problem computer
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains an application server running Windows Server 2003.
Users report intermittent slow performance when they access the application server throughout the day. You find out that the network interface on the application server is being heavily used during the periods of slow performance. You suspect that a single computer is causing the problem. You need to create a plan to identify the problem computer.
What should you do?
Which two actions should you take? (Each correct answer presents part of the solution
You are the network administrator for your company. The network consists of a single Active Directory domain. All computers on the network are members of the domain. You are planning a public key infrastructure (PKI) for the company. You want to ensure that users who log on to the domain receive a certificate that can be used to authenticate to Web sites.
You create a new certificate template named User Authentication. You configure a Group Policy object (GPO) that applies to all users. The GPO specifies that user certificates must be enrolled when the policy is applied. You install an enterprise certification authority (CA) on a computer that runs Windows Server 2003.
Users report that when they log on, they do not have certificates to authenticate to Web sites that require certificate authentication. You want to ensure that users receive certificates that can be used to authenticate to Web sites.
Which two actions should you take? (Each correct answer presents part of the solution. Choose two.)
You need to comply with the written security policy
You are a network administrator for your company. The company has a main office and one branch office. The network consists of a single Active Directory domain. All servers run Windows Server 2003. The company needs to connect the main office network and the branch office network by using Routing and Remote Access servers at each office. The networks will be connected by a VPN connection over the Internet.
The company’s written security policy includes the following requirements for VPN connections over the Internet. All data must be encrypted with end-to-end encryption. VPN connection authentication must be at the computer level. Credential information must not be transmitted over the Internet as part of the authentication process.
You need to configure security for VPN connection between the main office and the branch office. You need to comply with the written security policy.
What should you do?
You need to choose a secure authentication method
You are the network administrator for your company. The network consists of a single Active Directory domain. The company has remote users in the sales department who work from home. The remote users’ client computers run Windows XP Professional, and they are not members of the domain.
The remote users’ client computers have local Internet access through an ISP. The company is deploying a Windows Server 2003 computer named Server1 that has Routing and Remote Access installed. Server1 will function as a VPN server, and the remote users will use it to connect to the company network.
Confidential research data will be transmitted from the remote users’ client computers. Security is critical to the company and Server1 must protect the remote users’ data transmissions to the main office. The remote client computers will use L2TP/IPSec to connect to the VPN server. You need to choose a secure authentication method.
What should you do?
You need to configure the Application group to remain on Server2 while you research the problem on Server1
You are a network administrator for your company. You install Windows Server 2003 on two servers named Server1 and Server2. You configure Server1 and Server2 as a two-node cluster. You configure a custom application on the cluster by using the Generic Application resource, and you put all resources in the Application group.
You test the cluster and verify that it fails over properly and that you can move the Applications group from one node to the other and back again. The application and the cluster run successfully for several weeks.
Users then report that they cannot access the application. You investigate and discover that Server1 and Server2 are running but the Application group is in a failed state. You restart the Cluster service and attempt to bring the Application group online on Server1.
The Application group fails. You discover that Server1 fails, restarts automatically, and fails again soon after restarting. Server1 continues to fail and restart until the Application group reports that it is in a failed state and stops attempting to bring itself back online.
You need to configure the Application group to remain on Server2 while you research the problem on Server1.
What should you do?
You need to allow the user on Server2 to use the script to transfer files to Server5
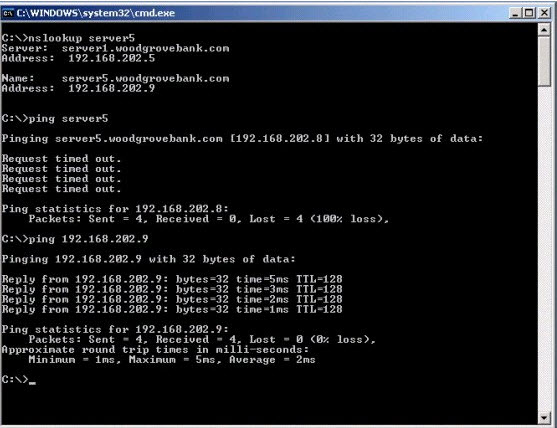
You are a network administrator for Woodgrove Bank. All servers run Windows Server 2003. The company uses WINS and DNS for name resolution.
The LMHosts and Hosts files are not used. A user on a server named Server2 reports that when she runs a script to transfer files to a server named Server5, she receives the following error messag* “Unknown host Server5.”
You use Server2 to troubleshoot the problem. The results of your troubleshooting are shown in the exhibit.
You need to allow the user on Server2 to use the script to transfer files to Server5.
What should you do?
Exhibit:
What should you do?
You are the network administrator for your company. The network consists of a single Active Directory domain. All computers on the network are members of the domain. You administer a three-node Network Load Balancing cluster. Each cluster node runs Windows Server 2003 and has a single network adapter.
The cluster has converged successfully. You notice that the nodes in the cluster run at almost full capacity most of the time. You want to add a fourth node to the cluster. You enable and configure Network Load Balancing on the fourth node. However, the cluster does not converge to a four-node cluster. In the System log on the existing three nodes, you find the exact same TCP/IP error event.
The event has the following description: “The system detected an address conflict for IP address 10.50.8.70 with the system having network hardware address 02:BF:0*32:08:46.” In the System log on the new fourth node, you find a similar TCP/error event with the following description: “The system detected an address conflict for IP address 10.50.8.70 with the system having network hardware address 03:BF:0*32:08:46.” Only the hardware address is different in the two descriptions. You verify that IP address 10.50.8.70 is configured as the cluster IP address on all four nodes.
You want to configure a four-node Network Load Balancing cluster.
What should you do?