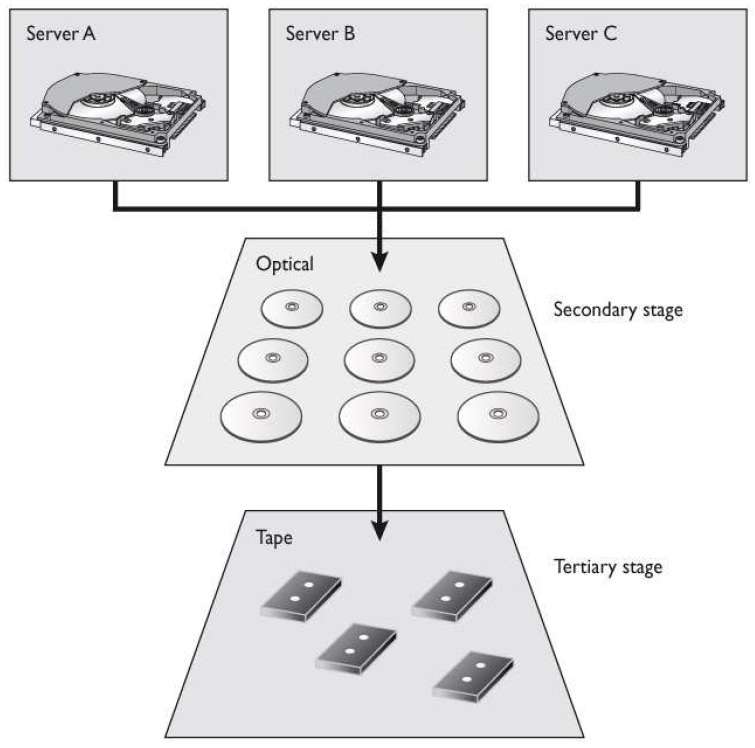
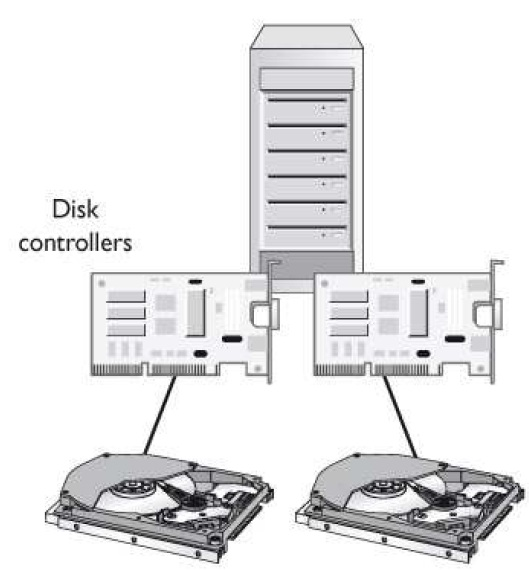
Which architecture does the graphic that follows represent?
What similar type of technology is shown in the graphic that follows?
What is parity information used for?
Which of the following is not one of those guidelines?
Guidelines should be followed to allow secure remote administration. Which of the following is not one of those guidelines?
What course of action should Brian take?
Brian, a security administrator, is responding to a virus infection. The antivirus application reports that a file has been infected with a dangerous virus and disinfecting it could damage the file. What course of action should Brian take?
What steps should he take if a report has no information?
John is responsible for providing a weekly report to his manager outlining the week’s security incidents and mitigation steps. What steps should he take if a report has no information?
Which of the following incorrectly describes mail relays?
The relay agent on a mail server plays a role in spam prevention. Which of the following incorrectly describes mail relays?
Which of the following is most likely the attack Sam used?
Brandy could not figure out how Sam gained unauthorized access to her system, since he has little computer experience. Which of the following is most likely the attack Sam used?
Which of the following is the best way to reduce brute-force attacks that allow intruders to uncover usersR
Which of the following is the best way to reduce brute-force attacks that allow intruders to uncover users’ passwords?
Which of the following best fits this need?
Fred is a new security officer who wants to implement a control for detecting and preventing users who attempt to exceed their authority by misusing the access rights that have been assigned to them. Which of the following best fits this need?