What are two reasons for this problem?
The dashboard widget indicates that FortiGuard Web Filtering is not reachable. However, AntiVirus, IPS, and
Application Control have no problems as shown in the exhibit.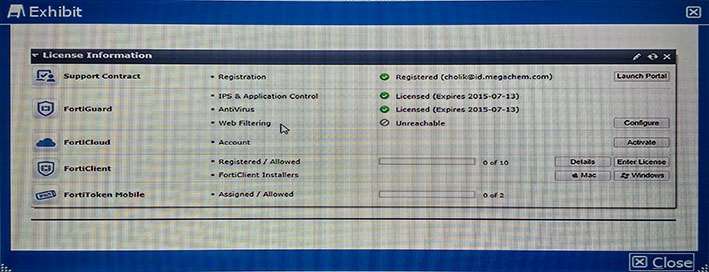
You contacted Fortinet’s customer service and discovered that your FortiGuard Web Filtering contract is still valid for several months.
What are two reasons for this problem? (Choose two.) not. http://cookbook.fortinet.com/troubleshooting-web-filtering/
what is causing the problem? http://kb.fortinet.com/…
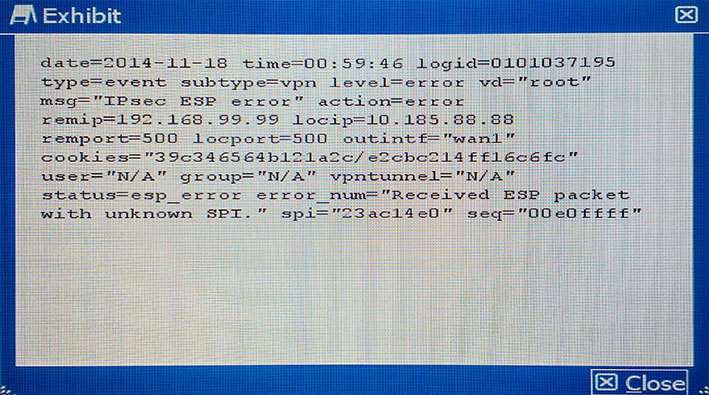
A customer is authenticating users using a FortiGate and an external LDAP server. The LDAP user, John
Smith, cannot authenticate. The administrator runs the debug command diagnose debug application fnbamd 255 while John Smith attempts the authentication:
Based on the output shown in the exhibit, what is causing the problem?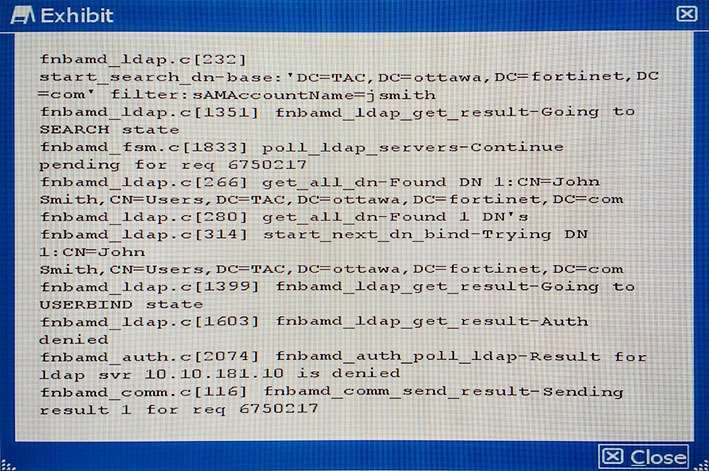
http://kb.fortinet.com/kb/documentLink.do?externalID=FD31886
Which two sniffer commands will capture this HTTP traffic?
The exhibit shows an explicit Web proxy configuration in a FortiGate device. 
The FortiGate is installed between a client with the IP address 172.16.10.4 and a Web server using port 80 with the IP address 10.10.3.4. The client Web browser is properly sending HTTP traffic to the FortiGate Web proxy IP address 172.16.10.254. Which two sniffer commands will capture this HTTP traffic? (Choose two.) http://www.maxnetwork.org/fortigate-packet-capture
Which step would you perform to load balance traffic wi…
Your colleague has enabled virtual clustering to load balance traffic between the cluster units. You notice that all traffic is currently directed to a single FortiGate unit. Your colleague has applied the configuration shown in the exhibit.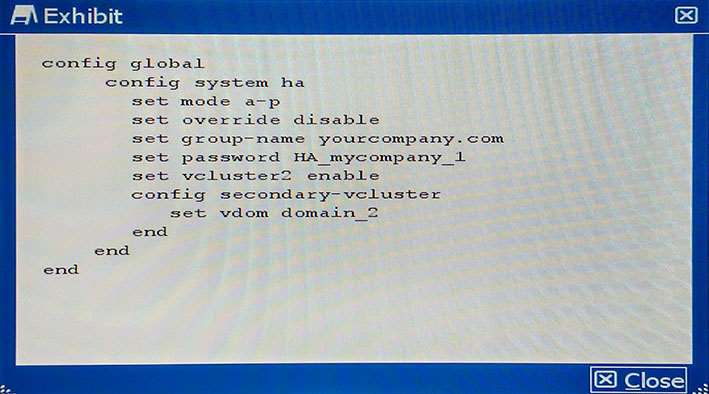
Which step would you perform to load balance traffic within the virtual cluster? http://docs.fortinet.com/uploaded/files/1088/fortigate-ha-50.pdf
Which solution meets these requirements?
A data center for example.com hosts several separate Web applications. Users authenticate with all of them by providing their Active Directory (AD) login credentials. You do not have access to Example, Inc.’s AD server.
Your solution must do the following:
– provide single sign-on (SSO) for all protected Web applications
– prevent login brute forcing
– scan FTPS connections to the Web servers for exploits
– scan Webmail for OWASP Top 10 vulnerabilities such as session cookie hijacking, XSS, and SQL injection attacks
Which solution meets these requirements? then forward all traffic to web server. http://cookbook.fortinet.com/providing-single-sign-using-ldap-fsso-agent-advanced-mode-expert/
Which policy will implement the project requirements?
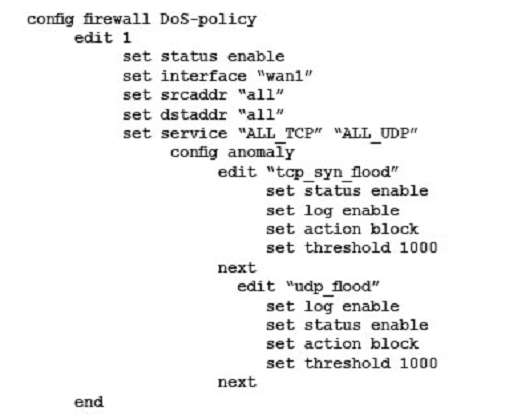
A company wants to protect against Denial of Service attacks and has launched a new project. They want to block the attacks that go above a certain threshold and for some others they are just trying to get a baseline of activity for those types of attacks so they are letting the traffic pass through without action. Given the following:
– The interface to the Internet is on WAN1.
– There is no requirement to specify which addresses are being protected or protected from.
– The protection is to extend to all services.
– The tcp_syn_flood attacks are to be recorded and blocked.
– The udp_flood attacks are to be recorded but not blocked.
– The tcp_syn_flood attack’s threshold is to be changed from the default to 1000.
The exhibit shows the current DoS-policy.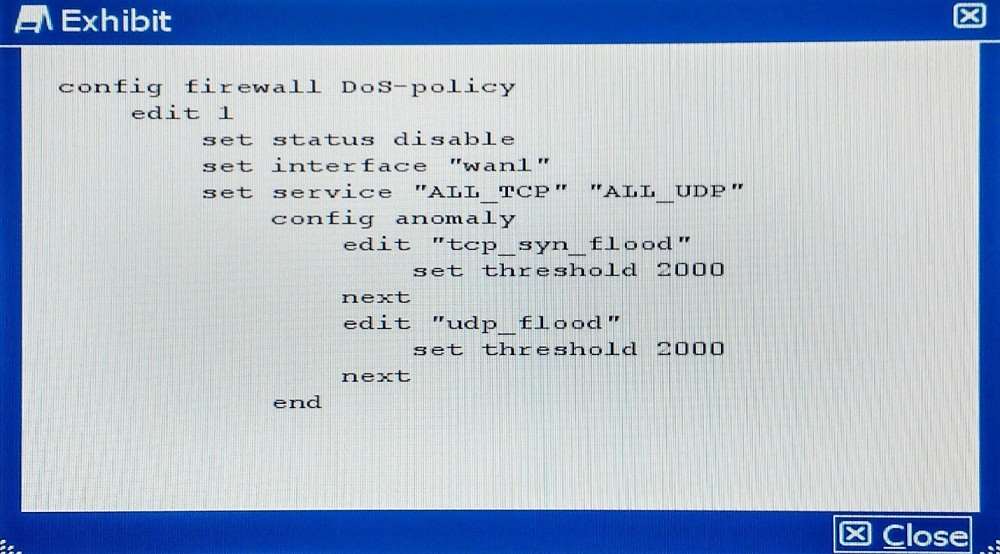
Which policy will implement the project requirements?
A)
D)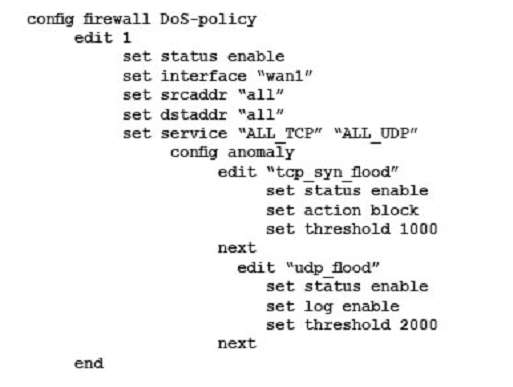
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-firewall-52/Examples/Example-%20DoS%
which two configurations are required to accomplish thi…
Your security department has requested that you implement the
OpenSSL.TLS.Heartbeat.Information.Disclosure signature using an IPS sensor to scan traffic destined to the
FortiGate. You must log all packets that attempt to exploit this vulnerability.
Referring to the exhibit, which two configurations are required to accomplish this task? (Choose two.)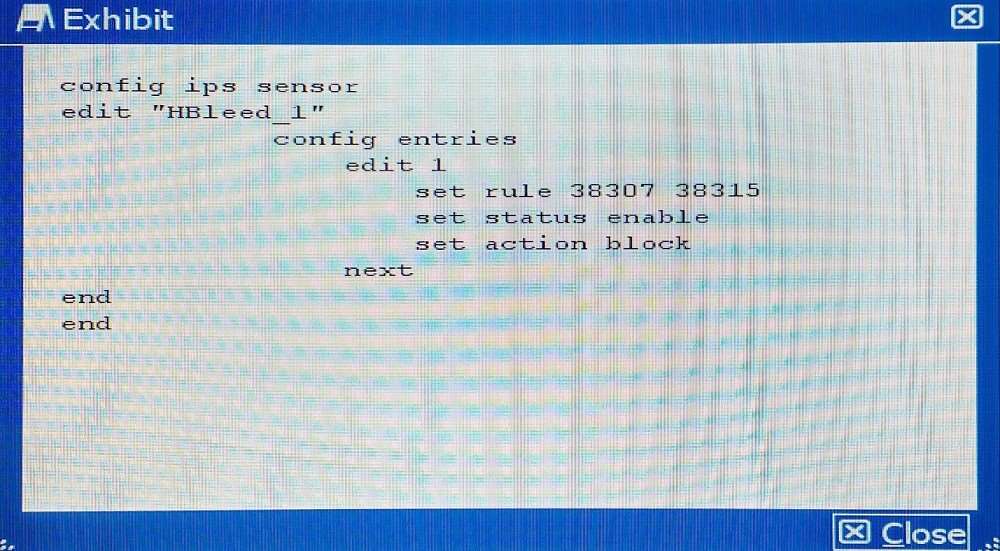
D)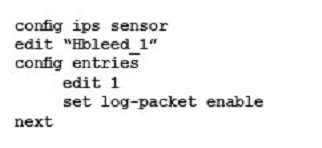
http://defadhil.blogspot.in/2014/04/how-to-protect-fortigate-from.html
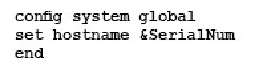
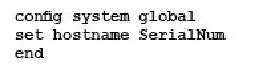
Which command syntax would you use to configure the ser…
which statement is true?
Which three configuration components meet these require…
You are asked to establish a VPN tunnel with a service provider using a third-party VPN device. The service provider has assigned subnet 30.30.30.0/24 for your outgoing traffic going towards the services hosted by the provider on network 20.20.20.0/24. You have multiple computers which will be accessing the remote services hosted by the service provider.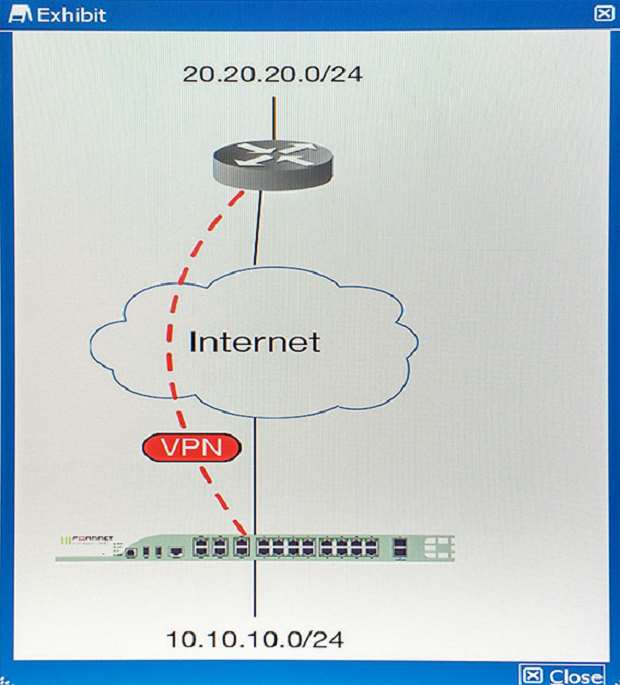
Which three configuration components meet these requirements? (Choose three.)