Refer to the exhibit.
If the given configuration is applied to the object-group vpnservers, during which time period
are external users able to connect?

A.
From Friday at 6:00 p.m. until Monday at 8:00 a.m.
B.
From Monday at 8:00 a.m. until Friday at 6:00 p.m.
C.
From Friday at 6:01 p.m. until Monday at 8:01 a.m.
D.
From Monday at 8:01 a.m. until Friday at 5:59 p.m.


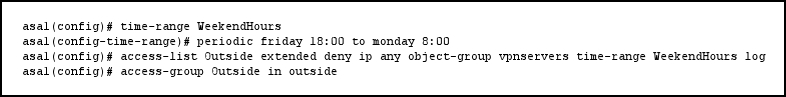
Answer should be B as this is when users are ‘able’ to connect or the question should ask when are users UNABLE to connect.
0
0
No it’s not… It’s C mate… Gimme what you are smoking my friend I want some also.
Remember a cisco product is a computer. Thus it states 6pm to 8am exactly …Seconds aren’t added here so only once the minute timer changes from 0 to 1 is when the ACL is removed.
0
0
Just pulling your Leg…You are correct…Not many discussions on here about the questions or exam and this was posted beginning of December.
0
0
Also there has been some extra Questions added on other sites for the 30 new questions for the exam …the questions were given from other students who wrote and added what is new.
0
0
Kazy – can u provide URL(s) for the additional 30 new questions?
Thank You
0
0
But actually my friend the real answer is D.
0
0
The ACL is deny ip from Friday 6pm to Monday 8am, this is when vpnservers getting denied.
So yeah, users will be able to connect outside this range.
That’s why the answer is D, which is after Monday 8am and before friday 6pm.
0
0
Any thoughts about the value of an an ACL with no permit entry…? Who comes up with this stuff?
0
0
seriously, no ‘permit’?
0
0
D is the correct answer
0
0
2018 Jan New 300-208 Exam Dumps with PDF and VCE Free Updated Today:
QUESTION 192
Which three host modes support MACsec? (Choose three.)
A. multidomain authentication host mode
B. multihost mode
C. multi-MAC host mode
D. single-host mode
E. dual-host mode
F. multi-auth host mode
Answer: ABD
QUESTION 193
You are troubleshooting wired 802.1X authentications and see the following error: “Authentication failed: 22040 Wrong password or invalid shared secret.” What should you inspect to determine the problem?
A. RADIUS shared secret
B. Active Directory shared secret
C. Identity source sequence
D. TACACS+ shared secret
E. Certificate authentication profile
Answer: A
QUESTION 194
Refer to the exhibit. You are troubleshooting RADIUS issues on the network and the debug radius command returns the given output. What is the most likely reason for the failure?
A. An invalid username or password was entered.
B. The RADIUS port is incorrect.
C. The NAD is untrusted by the RADIUS server.
D. The RADIUS server is unreachable.
E. RADIUS shared secret does not match
Answer: A
QUESTION 195
Which devices support download of environmental data and IP from Cisco ISE to SGT bindings in their SGFW implementation?
A. Cisco ASA devices
B. Cisco ISR G2 and later devices with ZBFW
C. Cisco ISR G3 devices with ZBFW
D. Cisco ASR devices with ZBFW
Answer: A
QUESTION 196
In Cisco ISE 1.3, where is BYOD enabled with dual-SSID onboarding?
A. client provisioning policy
B. client provisioning resources
C. BYOD portal
D. guest portal
Answer: D
QUESTION 197
Which description of the purpose of the Continue option in an authentication policy rule is true?
A. It allows Cisco ISE to check the list of rules in an authentication policy until there is a match.
B. It sends an authentication to the next subrule within the same authentication rule.
C. It allows Cisco ISE to proceed to the authorization policy regardless of authentication pass/fail.
D. It sends an authentication to the selected identity store.
E. It causes Cisco ISE to ignore the NAD because NAD will treat the Cisco ISE server as dead.
Answer: C
QUESTION 198
How many days does Cisco ISE wait before it purges a session from the active session list if no RADIUS Accounting STOP message is received?
A. 1
B. 5
C. 10
D. 15
Answer: B
QUESTION 199
A user configured a Cisco Identity Service Engine and switch to work with downloadable access list for wired dot1x users, though it is failing to work. Which command must be added to address the issue?
A. ip dhcp snooping
B. ip device tracking
C. dot1x pae authenticator
D. aaa authentication dot1x default group radius
Answer: B
QUESTION 201
Refer to the exhibit. In a distributed deployment of Cisco ISE, which column in Figure 1 is used to fill in the Host Name field in Figure 2 to collect captures on Cisco ISE while authenticating the specific endpoint?
A. Server
B. Network Device
C. Endpoint ID
D. Identity
Answer: A
QUESTION 202
Which ISE feature is used to facilitate a BYOD deployment?
A. self-service personal device registration and onboarding
B. Guest Service Sponsor Portal
C. Local Web Auth
D. Guest Identity Source Sequence
Answer: A
1
0
And you can download more free 300-208 Real Exam Questions at: https://www.braindump2go.com/300-208.html
0
0