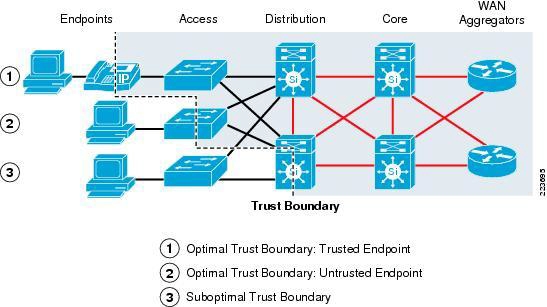
A network is deployed using recommended practices of the enterprise campus network
model, including users with desktop computers connected via IP phones. Given that all
components are QoS-capable, where are the two optimal locations for trust boundaries to be
configured by the network administrator? (Choose two.)

A.
host
B.
IP phone
C.
access layer switch
D.
distribution layer switch
E.
core layer switch
In the current campus QoS design, the access ports of each switch are configured to not
trust the QoS markings of any traffic arriving on that port—unless it is on the auxiliary or
voice VLAN and the switch has detected that there is a phone (trusted device) on that VLAN.
The decision to trust or not trust the endpoints traffic is binary; either the traffic is from the
phone and trusted or from any other device and not trusted. This model works well in an
environment with dedicated phones, but as the trends in Unified Communications continue
and voice/video applications start merging with other PC applications, the need to selectively
and intelligently trust certain application flows from the untrusted PC is becoming necessary.
The use of per VLAN and per port traffic policers is one mechanism that is used to
selectively trust traffic in certain port ranges and at certain data rates. Each edge port can be
configured to detect traffic within a specific port range and, for all traffic that is less than a
defined normal rate, mark that traffic with the correct DSCP values. All traffic in excess of
this rate is dropped, which provides a safety mechanism to protect against one application
masquerading as another more mission critical one (by using the more important
application’s port numbers for communication). While this policer-based approach has
proven to work well and is still valid for certain environments, the increasingly complex list of
applications that share port numbers and applications that might be hijacking other
applications trusted port ranges requires that we consider a more sophisticated approach.
Reference:http://www.cisco.com/en/US/docs/solutions/Enterprise/Campus/campover.html#wp709277