Which component functions as the Internal Certificate A…
Which component functions as the Internal Certificate Authority for R77?
What happens when a user from the internal network trie…
What should John request when he cannot access the web …
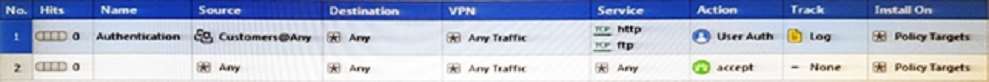
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to
designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway
policy permits access only from John’s desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT
department gave the laptop a static IP address, but that limits him to operating it only from his desk. The
current Rule Base contains a rule that lets John Adams access the HR Web Server from his desktop with a
static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web
Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the
policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server
from any machine and from any location.
3) Changes from static IP address to DHCP for the client PC.
What should John request when he cannot access the web server from his laptop?
How do you configure this change?
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to
00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you
configure this change?
How do you do this?
As a Security Administrator, you must refresh the Client Authentication authorized time-out every time a new
user connection is authorized. How do you do this? Enable the Refreshable Timeout setting:
which of the following should you remember?
The technical-support department has a requirement to access an intranet server. When configuring a User
Authentication rule to achieve this, which of the following should you remember?
How do you configure the Security Policy to provide use…
How do you configure the Security Policy to provide uses access to the Captive Portal through an external
(Internet) interface?
Which of the following uses the same key to decrypt as …
Which of the following uses the same key to decrypt as it does to encrypt?
Which SmartConsole application should you use to confir…
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of
your firm’s business partners. Which SmartConsole application should you use to confirm your suspicious?
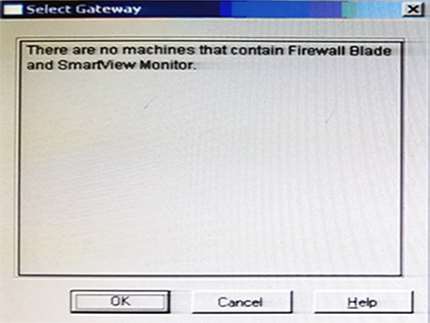
What should you do to analyze the packet size distribut…
You have just installed your Gateway and want to analyze the packet size distribution of your traffic with
SmartView Monitor.
Unfortunately, you get the message:
“There are no machines that contain Firewall Blade and SmartView Monitor”.
What should you do to analyze the packet size distribution of your traffic? Give the BEST answer.