Review the following screenshot and select the BEST answer.
Which of the following is NOT a SecureXL traffic flow?
Which of the following is NOT a SecureXL traffic flow?
Which encryption is used in Secure Internal Communicati…
Vanessa is firewall administrator in her company; her company is using Check Point firewalls on central and
remote locations, which are managed centrally by R80 Security Management Server. One central location has
an installed R77.30 Gateway on Open server. Remote location is using Check Point UTM-1 570 series
appliance with R71. Which encryption is used in Secure Internal Communication (SIC) between central
management and firewall on each location?
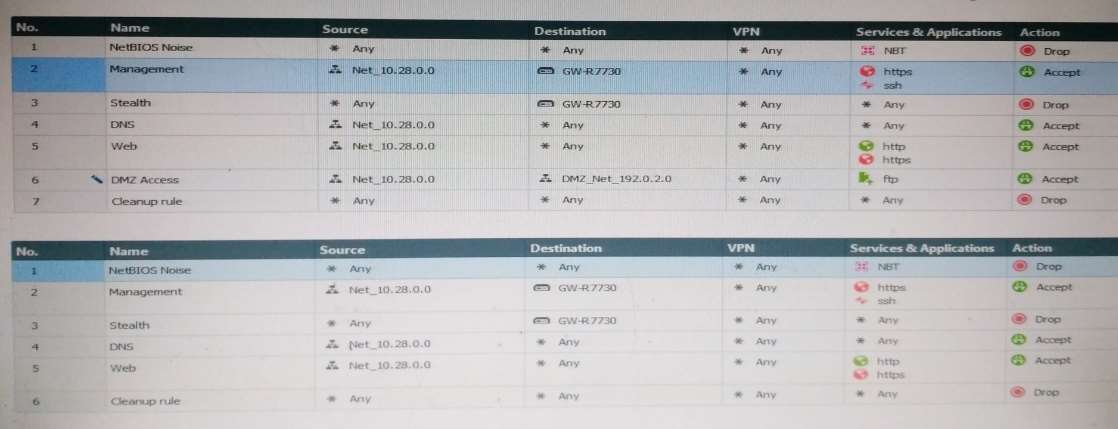
why does Dave not have the rule no.6 in his SmartConsol…
Two administrators Dave and Jon both manage R80 Management as administrators for Alpha Corp. Jon logged
into the R80 Management and then shortly after Dave logged in to the same server. They are both in the
Security Policies view. From the screenshots below, why does Dave not have the rule no.6 in his SmartConsole
view even though Jon has it his in his SmartConsole view?
Which of the following is NOT an integral part of VPN c…
Which of the following is NOT an integral part of VPN communication within a network?
How can you acheive this?
When your domain account password has to be changed you also want your pointsec password to be changed automatically. How can you acheive this?
how will you be able to access the Advanced options on the recovery media?
When trying to remove Pointsec by force on an unencrypted machine, using reco_img.exe, how will you be able to access the Advanced options on the recovery media?
what should be clearly stated in the organization’s e-mail policy?
If e-mail is subject to review by individuals other than the sender and recipient, what should be clearly stated in the organization’s e-mail policy?
What happens to Joey’s laptop?
Joey downloads the following Desktop Security Policy to his laptop and successfully logs in to the policy server. Joey then disconnects from the VPN-1 Policy server. exhibit What happens to Joey’s laptop?
Which of the following actions are denied to users, on net-detroit, when using FTP to an external host
You create a FTP resource and select the Get check box. exhibit Which of the following actions are denied to users, on net-detroit, when using FTP to an external host when the rule action is "accept" and no other permissive ftp rule exists lower in the rule base?