Which role or service should you move to the Jakarta site?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
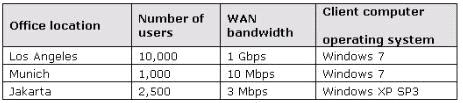
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
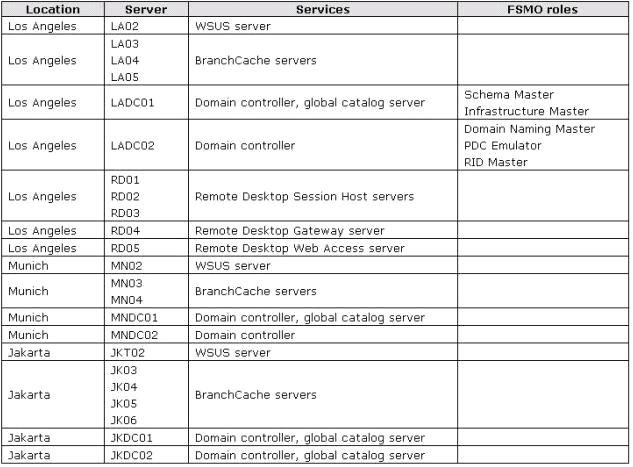
The company’s servers include those shown in the following table.
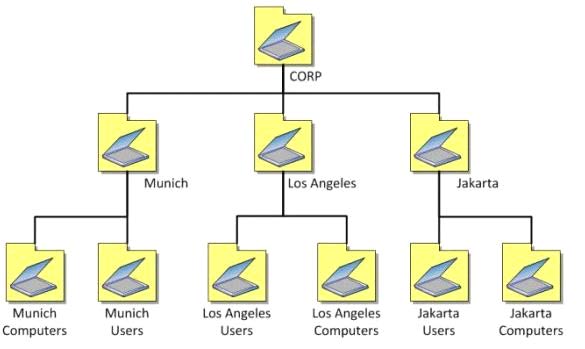
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to minimize WAN bandwidth for the Jakarta office during the acquisition.
Which role or service should you move to the Jakarta site?
Which address allocation should you use for the new Munich addresses?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You are planning to deploy the new network in Munich.
Which address allocation should you use for the new Munich addresses?
Which actions should you perform?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to prepare the new perimeter network and move the appropriate resources with the
minimum amount of downtime.
Which actions should you perform? (Choose all that apply.)
You need to design the deployment for the retail locations
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to design the deployment for the retail locations.
What should you do? (Choose all that apply.)
You need to apply the updates and comply with all requirements
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You run a Microsoft Baseline Security Analyzer scan and find that several important security updates
have not been applied to Jakarta client computers.
You need to apply the updates and comply with all requirements.
What should you do?
What should you recommend?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to specify the location and configuration for domain controllers in the new AD DS domain.
What should you recommend?
Which NAP enforcement method should you recommend?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to recommend a NAP enforcement method for wingtiptoys.com that meets the company’s
security requirements.
Which NAP enforcement method should you recommend?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 17
Graphics Design Institute
COMPANY OVERVIEW
Graphics Design Institute is a training company that has four offices.
Graphics Design Institute recently purchased another company named Proseware, Inc.
PLANNED CHANGES
Graphics Design Institute plans to transition the internal IPv4 network to IPv6. IPv4 will be used to
connect to the Internet. Only private IPv6 addresses will be used on the internal network.
Graphics Design Institute plans to deploy a remote access solution for all client computers.
Graphics Design Institute plans to deploy 10 public computers that run Windows Vista Service Pack 2
(SP2). All Windows Vista public computers will run an application named Appl.
Graphics Design Institute plans to deploy 10 public computers that run Windows 7 Professional. All
windows 7 public computers will run an application named App2.
You plan to deploy a virtualization solution that will host 120 virtual machines (VMs). You run
performance tests and verify that you can host 20 VMs per server and still maintain adequate
performance.
EXISTING ENVIRONMENT
All client computers run Windows 7 Enterprise and are joined to the Active Directory domain. All of
the client computers use wireless WAN (WWAN) network adapters to maintain permanent
connections to the Internet.
An application named BusinessApp is installed on a server in graphicdesigninstitute.com.
BusinessApp only supports Kerberos authentication. Only users in graphicdesigninstitute.com
currently use BusinessApp.
Existing Network Infrastructure
The network contains four IPv4 subnets.
REQUIREMENTS
Technical Requirements
All of the client computers that use IPv4 must be able to communicate with the client computers
that use IPv6.
Administrators must be able to remotely manage the client computers when users work either from
the office or remotely. Administrators must be able to remotely manage the client computers if the
users are not logged on to their computers.
Administrators must ensure that only Appl and App2 run on the public computers.
Graphics Design Institute must meet the following visualization requirements:
Support Hyper-V live migration.
Minimize hardware and software costs.
Ensure that all of the VMs are available if a single server fails.
Prevent any impact on the performance of the VMs if a single server fails.
Minimize the amount of administrative effort required to manage a storage solution for the Hyper-V
servers.
Security Requirements
The corporate security policy states that when an administrator modifies the permissions assigned
to the members of a group named Group1, the permissions must be restored to their default
settings.
###EndCaseStudy###
You need to recommend a remote access solution that meets the company’s technical
requirements. What should you include in the recommendation?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 17
Graphics Design Institute
COMPANY OVERVIEW
Graphics Design Institute is a training company that has four offices.
Graphics Design Institute recently purchased another company named Proseware, Inc.
PLANNED CHANGES
Graphics Design Institute plans to transition the internal IPv4 network to IPv6. IPv4 will be used to
connect to the Internet. Only private IPv6 addresses will be used on the internal network.
Graphics Design Institute plans to deploy a remote access solution for all client computers.
Graphics Design Institute plans to deploy 10 public computers that run Windows Vista Service Pack 2
(SP2). All Windows Vista public computers will run an application named Appl.
Graphics Design Institute plans to deploy 10 public computers that run Windows 7 Professional. All
windows 7 public computers will run an application named App2.
You plan to deploy a virtualization solution that will host 120 virtual machines (VMs). You run
performance tests and verify that you can host 20 VMs per server and still maintain adequate
performance.
EXISTING ENVIRONMENT
All client computers run Windows 7 Enterprise and are joined to the Active Directory domain. All of
the client computers use wireless WAN (WWAN) network adapters to maintain permanent
connections to the Internet.
An application named BusinessApp is installed on a server in graphicdesigninstitute.com.
BusinessApp only supports Kerberos authentication. Only users in graphicdesigninstitute.com
currently use BusinessApp.
Existing Network Infrastructure
The network contains four IPv4 subnets.
REQUIREMENTS
Technical Requirements
All of the client computers that use IPv4 must be able to communicate with the client computers
that use IPv6.
Administrators must be able to remotely manage the client computers when users work either from
the office or remotely. Administrators must be able to remotely manage the client computers if the
users are not logged on to their computers.
Administrators must ensure that only Appl and App2 run on the public computers.
Graphics Design Institute must meet the following visualization requirements:
Support Hyper-V live migration.
Minimize hardware and software costs.
Ensure that all of the VMs are available if a single server fails.
Prevent any impact on the performance of the VMs if a single server fails.
Minimize the amount of administrative effort required to manage a storage solution for the Hyper-V
servers.
Security Requirements
The corporate security policy states that when an administrator modifies the permissions assigned
to the members of a group named Group1, the permissions must be restored to their default
settings.
###EndCaseStudy###
You need to recommend a remote access solution that meets the company’s technical
requirements.
What should you include in the recommendation?
What should you recommend?
###BeginCaseStudy###
Case Study: 17
Graphics Design Institute
COMPANY OVERVIEW
Graphics Design Institute is a training company that has four offices.
Graphics Design Institute recently purchased another company named Proseware, Inc.
PLANNED CHANGES
Graphics Design Institute plans to transition the internal IPv4 network to IPv6. IPv4 will be used to
connect to the Internet. Only private IPv6 addresses will be used on the internal network.
Graphics Design Institute plans to deploy a remote access solution for all client computers.
Graphics Design Institute plans to deploy 10 public computers that run Windows Vista Service Pack 2
(SP2). All Windows Vista public computers will run an application named Appl.
Graphics Design Institute plans to deploy 10 public computers that run Windows 7 Professional. All
windows 7 public computers will run an application named App2.
You plan to deploy a virtualization solution that will host 120 virtual machines (VMs). You run
performance tests and verify that you can host 20 VMs per server and still maintain adequate
performance.
EXISTING ENVIRONMENT
All client computers run Windows 7 Enterprise and are joined to the Active Directory domain. All of
the client computers use wireless WAN (WWAN) network adapters to maintain permanent
connections to the Internet.
An application named BusinessApp is installed on a server in graphicdesigninstitute.com.
BusinessApp only supports Kerberos authentication. Only users in graphicdesigninstitute.com
currently use BusinessApp.
Existing Network Infrastructure
The network contains four IPv4 subnets.
REQUIREMENTS
Technical Requirements
All of the client computers that use IPv4 must be able to communicate with the client computers
that use IPv6.
Administrators must be able to remotely manage the client computers when users work either from
the office or remotely. Administrators must be able to remotely manage the client computers if the
users are not logged on to their computers.
Administrators must ensure that only Appl and App2 run on the public computers.
Graphics Design Institute must meet the following visualization requirements:
Support Hyper-V live migration.
Minimize hardware and software costs.
Ensure that all of the VMs are available if a single server fails.
Prevent any impact on the performance of the VMs if a single server fails.
Minimize the amount of administrative effort required to manage a storage solution for the Hyper-V
servers.
Security Requirements
The corporate security policy states that when an administrator modifies the permissions assigned
to the members of a group named Group1, the permissions must be restored to their default
settings.
###EndCaseStudy###
You need to recommend a visualization solution that meets the company’ s technical requirements.
What should you recommend?