What should you include in the recommendation?
Testlet: Trey Research
You need to recommend changes to the environment that meet the company’s user requirements.
What should you include in the recommendation?\r\n
COMPANY OVERVIEW
Trey Research is a pharmaceutical company that has a main office and two branch offices.
The main office is located in Denver. The branch offices are located in New York and Seattle. The main
office has 10,000 users. Each branch office has approximately 200 users.
PLANNED CHANGES
You plan to deploy a new application named App1. App1 is developed in-house. The binary executables
and support files for App1 contain sensitive intellectual property.
Users must access App1 through document invocation.The users must be prevented from directly copying
or accessing the App1 program files.
EXISTING ENVIRONMENT
The network contains a single Active Directory domain named treyresearch.com.
All servers run Windows Server 2008 R2. All client computers run Windows 7 Enterprise.
The network contains a Web server named Web1 that hosts an intranet site. All users use Web1.
Users report that access to the content on Web1 is slow. You discover that the CPU utilization of Web1is
approximately 90 percent during peak hours.
Microsoft System Center Configuration Manager is used to deploy updates to all of the client computers.
Existing Network Infrastructure
Each office has several file servers. The file servers have a limited amount of storage space. Users access
the data on all of the file servers.
Each branch office has a WAN link to the main office. Users in the branch office frequently access thefile
server in the main office.
Current Administration Model
All servers are currently administered remotely by using Remote Desktop. Help desk users perform the
following administrative tasks in the domain:
Manage printers.
Create shared folders.
Manage Active Directory users.
Modify file permissions and share permissions.
All of the help desk users are members of a global group named HelpDesk.
Business Goals
Trey Research has the following business goals:
Minimize the cost of making changes to the environment.
Minimize the cost of managing the network infrastructure and the servers.
REQUIREMENTS
Technical Requirements
Trey Research plans to virtualize all of the servers during the next three years.
Trey Research must meet the following technical requirements for virtualization:
Simplify the management of all hardware.
Allocate CPU resources between virtual machines (VMs).
Ensure that the VMs can connect to multiple virtuallocal area networks (VLANs).
Minimize the amount of administrative effort required to convert physical servers to VMs.
Trey Research must ensure that users can access content in the shared folders if a single server fails. The
solution must also reduce the amount of bandwidth used to access the shared folders from the branch
offices.
Trey Research must meet the following technical requirements for the intranet site:
Improve response time for users.
Provide redundancy if a single server fails.
Security Requirements
A new corporate security policy states that only Enterprise Administrators are allowed to interactively log on
to servers.
User Requirements
Users report that it is difficult to locate files in the shared folders across the network. The users want a
single point of access for all of the shared folders in the company.
What should you include in the recommendation?
Testlet: Trey Research
You need to recommend changes to the environment that meet the company’s user requirements.
What should you include in the recommendation?\r\n
COMPANY OVERVIEW
Trey Research is a pharmaceutical company that has a main office and two branch offices.
The main office is located in Denver. The branch offices are located in New York and Seattle. The main
office has 10,000 users. Each branch office has approximately 200 users.
PLANNED CHANGES
You plan to deploy a new application named App1. App1 is developed in-house. The binary executables
and support files for App1 contain sensitive intellectual property.
Users must access App1 through document invocation.The users must be prevented from directly copying
or accessing the App1 program files.
EXISTING ENVIRONMENT
The network contains a single Active Directory domain named treyresearch.com.
All servers run Windows Server 2008 R2. All client computers run Windows 7 Enterprise.
The network contains a Web server named Web1 that hosts an intranet site. All users use Web1.
Users report that access to the content on Web1 is slow. You discover that the CPU utilization of Web1is
approximately 90 percent during peak hours.
Microsoft System Center Configuration Manager is used to deploy updates to all of the client computers.
Existing Network Infrastructure
Each office has several file servers. The file servers have a limited amount of storage space. Users access
the data on all of the file servers.
Each branch office has a WAN link to the main office. Users in the branch office frequently access thefile
server in the main office.
Current Administration Model
All servers are currently administered remotely by using Remote Desktop. Help desk users perform the
following administrative tasks in the domain:
Manage printers.
Create shared folders.
Manage Active Directory users.
Modify file permissions and share permissions.
All of the help desk users are members of a global group named HelpDesk.
Business Goals
Trey Research has the following business goals:
Minimize the cost of making changes to the environment.
Minimize the cost of managing the network infrastructure and the servers.
REQUIREMENTS
Technical Requirements
Trey Research plans to virtualize all of the servers during the next three years.
Trey Research must meet the following technical requirements for virtualization:
Simplify the management of all hardware.
Allocate CPU resources between virtual machines (VMs).
Ensure that the VMs can connect to multiple virtuallocal area networks (VLANs).
Minimize the amount of administrative effort required to convert physical servers to VMs.
Trey Research must ensure that users can access content in the shared folders if a single server fails. The
solution must also reduce the amount of bandwidth used to access the shared folders from the branch
offices.
Trey Research must meet the following technical requirements for the intranet site:
Improve response time for users.
Provide redundancy if a single server fails.
Security Requirements
A new corporate security policy states that only Enterprise Administrators are allowed to interactively log on
to servers.
User Requirements
Users report that it is difficult to locate files in the shared folders across the network. The users want a
single point of access for all of the shared folders in the company.
Which role services should you configure?
Testlet: Graphic Design Institute, Case B
You need to configure the role services on all fileservers that are necessary to meet the technical
requirements.
Which role services should you configure? (Choose all that apply.)\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 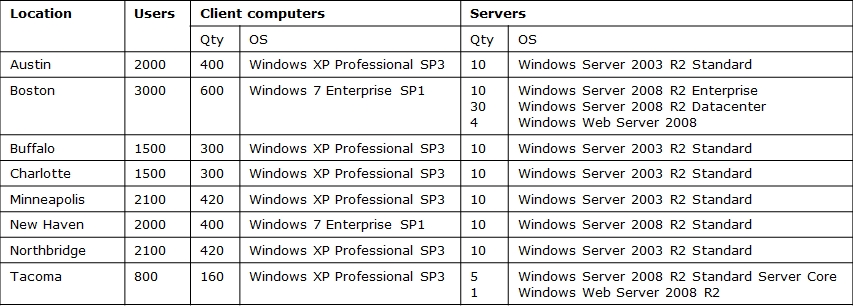
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 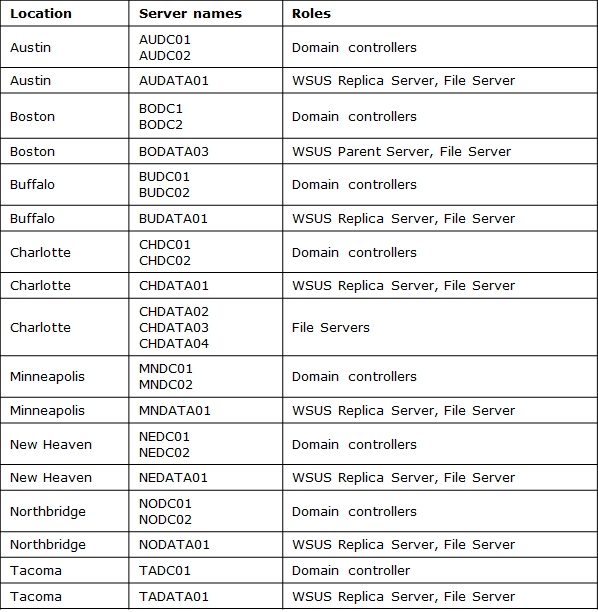
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
Which deployment strategy should you recommend?
Testlet: Graphic Design Institute, Case B
You are designing a Windows Server 2008 R2 deployment strategy for the Minneapolis campus servers.
Which deployment strategy should you recommend?\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
What should you recommend?
Testlet: Graphic Design Institute, Case B
You need to plan for the installation of critical updates to only shared client computers.
What should you recommend?\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
Which two actions should you perform?
Testlet: Graphic Design Institute, Case B
You are planning the deployment of Windows Server 2008 R2 to CHDATA03 and CHDATA04.
You have the following requirements:
Do not impact settings for CHDATA01 and CHDATA02.
Apply Windows Server 2008 R2-specific settings to CHDATA03 and CHDATA04 after migration.
Ensure that the ServerSettings GPO does not apply to CHDATA03 and CHDATA04 after migration.
You need to plan a strategy that meets the requirements.
Which two actions should you perform? (Each correctanswer presents part of the solution. Choose two.)\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
What should you recommend?
Testlet: Graphic Design Institute, Case B
You need to apply a critical security update to allcomputers on the New Haven campus while ensuring that
New Haven computers continue to receive scheduled updates from BODATA03. You must not apply the
security update to any other computers.
What should you recommend?\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
What should the recovery strategy include?
Testlet: Graphic Design Institute, Case B
You are planning a recovery strategy in the event that a file server is unable to boot into Windows. You need to
ensure that file servers can be restored from backups.
What should the recovery strategy include?\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
Which tools could you use?
Testlet: Graphic Design Institute, Case B
You need to plan a scheduled daily backup of all files on TADC01.
Which tools could you use? (Choose all that apply.)\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.
Which command should you execute?
Testlet: Graphic Design Institute, Case B
You are testing a file replication strategy for theIT Budget folders on BODATA01, NEDATA01, and
TADATA01.
The IT Budget folder on TADATA01 is the primary member.
You need to force replication of files to the Boston campus as soon as possible.
Which command should you execute?\r\n
General Background
You are the systems administrator for the Graphic Design Institute (GDI). GDI is a private liberal arts and
technical college with campuses in multiple cities.
Technical Background
The campus locations, users, client computers, and servers are described in the following table. 
The campuses are connected by a fully meshed WAN.
The corporate network includes Active Directory Domain Services (AD DS). Domain controllers are located
on each campus.
GDI uses Microsoft Windows Deployment Server (WDS) to distribute images by using Preboot Execution
Environment (PXE). GDI builds images by using the Windows Automated Installation Kit (WAIK).
GDI uses Microsoft Windows Server Update Services (WSUS) to distribute and manage Windows security
updates and software updates.
All private client computers and portable computersused by faculty and staff are members of the WSUS
computer group named Staff. All shared client computers are members of the WSUS computer group
named LabComputers. All faculty and staff users aremembers of the global security group named
GDI_Staff. All students are members of the global security group named GDI_Students.
Specific servers are configured as shown in the following table. 
The main data center is located on the Boston campus. ADMX and ADML files are centrally stored on
BODC01.
All Charlotte servers reside in the CH_Servers organizational unit (OU). CHDATA01, CHDATA02,
CHDATA03, and CHDATA04 reside in the CH_FileServersOU. CH_FileServers is a child OU of
CH_Servers.
A Group Policy object (GPO) named ServerSettings applies Windows Internet Explorer settings to all
servers.
Business Requirements
After successful migrations to Windows Server 2008 R2 in Boston, New Haven, and Tacoma, GDI plans to
migrate its other campuses to Windows Server 2008 R2 in advance of a full Windows 7 client computer
deployment.
Server deployment on the Austin campus must be performed on weekends by using scheduled
deployments.
The post-migration environment must meet the following business requirements:
Maximize security.
Maximize data protection.
Maximize existing resources.
Minimize downtime.
Technical Requirements
The post-migration environment must meet the following security requirements:
All updates must be distributed by using WSUS.
All critical updates must be installed as soon as possible.
All drives on the Minneapolis campus servers must have Windows BitLocker Drive Encryption enabled.
The post-migration environment must meet the following data protection requirements:
All servers must have automated backup routines.
All backups must be replicated to the Boston data center at the end of each business week.
The post-migration environment must meet the following resource requirements:
Installations and recovery must be performed remotely.
All department volumes on file servers must have NTFS quotas.
Minimize download time for users who open MicrosoftOffice documents over the WAN.
Ensure that users’ files are always opened from theclosest file server when available.
Users’ files must be accessible by the same path from all campuses.

