Which two components should you identify?
You are a network administrator for a company named Contoso, Ltd.
You install the Active Directory Rights Management Services server role on a server. The Active Directory
Rights Management Services (AD RMS) server uses an internal certification authority (CA) for all certificates.
You plan to provide users with the ability to use AD RMS to protect all of the email messages sent to a partner
company named A. Datum Corporation.
ADatum does not have AD RMS deployed.
You need to identify which components from the Contoso network must be accessible to A. Datum to ensure
that the users at A. Datum can open protected messages.
Which two components should you identify? (Each correct answer presents part of the solution. Choose two.)
Which two actions should you perform?
Your company has offices in Montreal, New York, and Toronto.
Each office is configured as an Active Directory site. The Montreal office has a site link to the New York office.
The New York office has a site link to the Toronto office.
You have an Exchange Server 2013 organization that contains five Mailbox servers. The organization is
configured as shown in the exhibit. (Click the Exhibit button.)
The servers in the Montreal and Toronto offices are members of a database availability group (DAG) named
DAG01. DAG01 contains two databases name TOMBX and MTLMBX.
MTLMBX is active on EX1 and contains all of the mailboxes of the users in the Montreal office.
TOMBX is active on EX3 and contains all of the mailboxes of the users in the Toronto office.
You need to ensure that all email messages transmitted between the Montreal users and the Toronto users are
routed through EX5.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
Which tasks should you identify?
DRAG DROP
You work for a financial services company that has an Exchange Server 2013 organization.
Mailbox audit logging is enabled for all mailboxes.
The company identifies the following requirements for the sales department:
The manager of the sales department must be able to search for email messages that contain specific key
words in the mailboxes of the users in the sales department.
The manager of the human resources department must receive a report that contains a list of all the sales
users’ mailboxes that were searched by the sales manager.
You need to identify which tasks must be performed to meet the requirements.
Which tasks should you identify?
To answer, drag the appropriate task to the correct requirement in the answer area. Each task may be used
once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to
view content.
Select and Place:
Which command should you run?
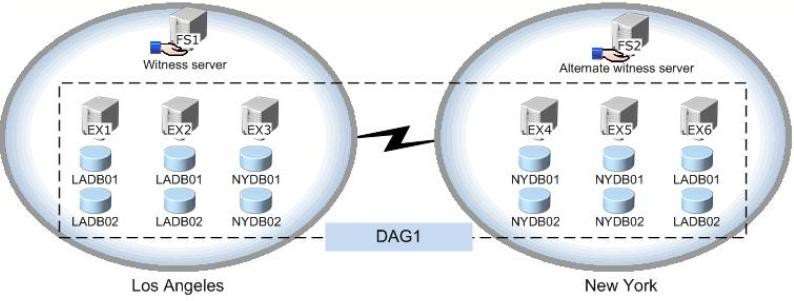
You have an Exchange Server 2013 organization that contains one office in Los Angeles and one office in New
York.
All servers have the Mailbox server role and the Client Access server role installed and are members of a data
availability group (DAG) named DAG1. The servers and databases are shown in the exhibit. (Click the Exhibit
button.)
You need to ensure that if the active copy of LADB01 fails, a server in the same site will attempt to activate a
copy of the database before a server in another site does. The solution must not influence the activation of
other database copies.
Which command should you run?
You need to ensure that all of the email messages are s…
Your company has a hybrid deployment of Exchange Server 2013 and Microsoft Office 365.
All recipients have an SMTP suffix of contoso.com.
You discover that all of the email messages sent to the Internet from users who have Office 365 mailboxes are
routed through the on-premises Exchange servers.You need to ensure that all of the email messages are sent directly to the Internet.
What should you do?
You need to replace the certificate
You have an Exchange Server 2013 organization that contains 10 servers.
You have a federation trust to the Microsoft Federation Gateway. The certificate in the trust relationship expires
soon.
You need to replace the certificate. The solution must minimize downtime.
You purchase a new certificate.
What should you do next?
You need to ensure that users in fabrikam.com can find …
A company named Contoso, Ltd., has an Exchange Server 2013 organization. The primary SMTP suffix for all
users is contoso.com.
A company named Fabrikam, Inc., has an Exchange Server 2010 organization. The primary SMTP suffix for all
users is fabrikam.com.
The users in both organizations access their email by using Microsoft Outlook 2010 and Outlook Anywhere. All
of the users work from domain-joined client computers that connect to the internal network.
Contoso acquires Fabrikam.
You establish a cross-forest trust between the Contoso forest and the Fabrikam forest.
In fabrikam.com, you create a user named User1. In contoso.com, you create a linked mailbox for User1 and
you set the primary SMTP address to User1@fabrikam.com.
User1 reports that Outlook 2010 fails to configure his mail profile automatically. User1 can manually configure
his profile and connect to his mailbox.
You need to ensure that users in fabrikam.com can find their mailboxes automatically.
What should you do in contoso.com?
Which two cmdlets should you run?
Your company has an Exchange Server 2013 organization named Contoso.
A partner company has an Exchange Server 2013 organization named Fabrikam. Neither company has any
trusts between their forests.
Users from both organizations access their mailbox from the Internet by using Outlook Anywhere.
You need to ensure that the users from both organizations can share free/busy information.
Which two cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)
You need to prevent a user named User1 from permanently…
You have an Exchange Server 2013 organization.
You need to prevent a user named User1 from permanently deleting an email message in his mailbox.
What should you do on the mailbox of User1?
Which technology should you recommend for each requirement?
DRAG DROP
Contoso, Ltd., is a bank that has offices in North America and Europe.
The company must comply with different regulations for North America and Europe.
The company uses Information Right Management (IRM) to protect sensitive documents, such as internal
financial reports.
You need to recommend a compliance solution to meet the following requirements:
Prevent users from disclosing customers’ personal information in email messages.
Prevent users from disclosing internal financial data to people outside of the company.
Prevent the permanent deletion of email messages of users who are under investigation.
Allow compliance officers to search the mailbox of users who are under investigation without being able to
alter the data in the mailbox.
Which technology should you recommend for each requirement?
To answer, drag the appropriate technology to the correct requirement in the answer area. Each technology
may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between
panes or scroll to view content.
Select and Place: