You need to minimize the amount of Trusted Platform Module (TPM) authorization information that is stored in t
A company has an Active Directory Domain Services (AD DS) domain. All client computers run
Windows 8. You need to minimize the amount of Trusted Platform Module (TPM) authorization
information that is stored in the registry. What should you do?
Which command should you run on the client computer?
A company has client computers that run Windows 8. The company uses Windows BitLocker Drive
Encryption with the data-only option on all client computers. You delete a file containing highly
confidential information from your computer. You need to clear the free space on the hard drive to
minimize the chance of the confidential information being recovered. Which command should you
run on the client computer?
You need to configure Group Policy settings to meet the requirements
A company has an Active Directory Domain Services (AD DS) domain. All client computers run
Windows 8 and are joined to the domain. You have the following requirements:
• Ensure that files in shared network folders are available offline.
• Minimize all data access times.
• Reduce network bandwidth usage.
You need to configure Group Policy settings to meet the requirements.
What should you do first?
Which policy setting should you configure?
A company has an Active Directory Domain Services (AD DS) domain. All client computers run
Windows 8. Client computers use Windows BitLocker Drive Encryption with a Trusted Platform
Module (TPM) chip. You need to create a Group Policy object (GPO) that will secure the TPM owner
information. Which policy setting should you configure?
Which two actions should you perform?
You support laptops that run Windows 8 Enterprise. Microsoft BitLocker Administration and
Monitoring (MBAM) are deployed on your network on a server named SERVER1. Company policy
requires that laptops with MBAM client installed prompt users to enable BitLocker within 2 hours of
being started. You need to make changes to the Configure MBAM Services Group Policy settings.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
You need to connect Office 365 to Lync and Outlook
You are a Windows 8 user. Your organization has purchased an Office 365 subscription. You install
Microsoft Lync and Microsoft Outlook on your computer. You need to connect Office 365 to Lync
and Outlook. What should you do?
You need to ensure that users that meet the membership criteria are added to the Windows Intune group
You administer computers that run Windows 8 Enterprise in an Active Directory domain in a single
Active Directory Site. All user account objects in Active Directory have the Manager attribute
populated. The company has purchased a subscription to Windows Intune. The domain security
groups are synchronized with the Microsoft Online directory. You create a Windows Intune group
that specifies a manager as a membership criterion. You notice that the group has no members. You
need to ensure that users that meet the membership criteria are added to the Windows Intune
group. What should you do?
Which three actions should you perform on the laptop in sequence?
DRAG DROP
You use a desktop computer and a laptop, both of which run Windows 8. You use a Microsoft
account to log on to the desktop computer and a local user account to log on to the laptop. The
desktop computer is joined to the HomeGroup and the laptop is a member of a workgroup. When
you access a frequently visited website from your laptop, Internet Explorer saves your password.
When you visit the website from your desktop computer, you are prompted to enter your password.
You need to sync your saved password from your laptop to your desktop computer. Which three
actions should you perform on the laptop in sequence? (To answer, move the appropriate actions
from the list of actions to the answer area and arrange them in the correct order.)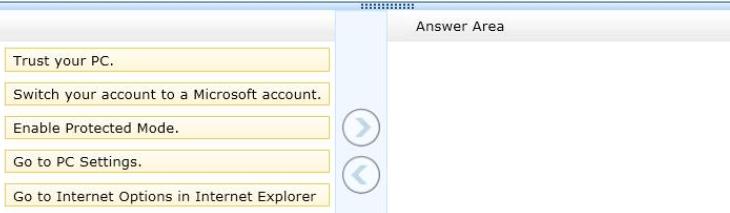
You need to minimize the time that is required for the user to start App-V applications on the computer
You administer computers that run Windows 8 Pro. The desktops have the Application Virtualization
(App-V) client installed. Multiple App-V applications are published on the network. A user reports
that it is taking a long time to launch App-V applications on his computer. You discover that the user
has a roaming profile on the computer. You need to minimize the time that is required for the user
to start App-V applications on the computer. What should you do?
You need to create a Windows Intune policy that meets the security policy requirements
You administer computers that run Windows 8 Enterprise in an Active Directory domain. Your
company has purchased a subscription to Windows Intune. Users access a Microsoft Exchange
environment by using the Mail tile. The Microsoft Exchange environment is connected to Windows
Intune. Company security policy defines the minimum length of passwords and required encryption
settings. You need to create a Windows Intune policy that meets the security policy requirements.
What should you do?

