Which policy should you configure?
You administer windows 8 computers in you company network. all computers include
Windows 8 compatible trusted platform modele (TPM).
You configure a computer that will run a credit processing application.
You need to ensure that the computer requires a user to enter a PIN code when starting the computer.
Which policy should you configure? (To answer, select the appropriate policy in the answer area.)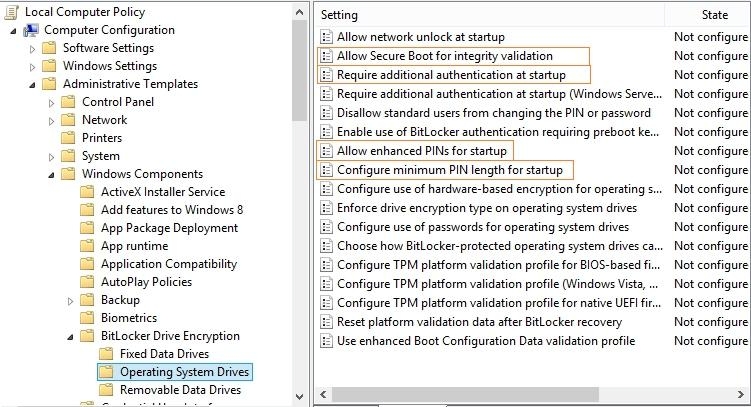
You need to ensure that the guest user is able to share network resources over Wi-Fi without lowering the over
You administer Windows 8 client computers in your company network.
A guest at your company is connected to the Internet as shown in the following exhibit. (Click the Exhibit button.)
You need to ensure that the guest user is able to share network resources over Wi-Fi
without lowering the overall security of the computer. What should you do?
You need to ensure that the default printer for the computer is the office printer …
A company has client computers that run Windows 8.
When a user tries to print from his portable client computer while connected to the corporate
network, he discovers that the default printer is set to his home printer instead of to the office
printer.
You need to ensure that the default printer for the computer is the office printer when the
computer is connected to the corporate network and the user’s home printer when the
computer is connected to his home network.
What should you do on the portable computer?
Which two actions should you perform?
A company has an Active Directory Domain Services (AD DS) domain. All client computers
run Windows 8.
You need to configure 20 portable computers so that they sleep after 20 minutes when
running on battery power. You must accomplish this goal by using the least amount of
administrative effort.
Which two actions should you perform? (Each correct answer presents part of the complete
solution. Choose two.)
You need to restore the client computer to full functionality
You install Windows 8 on a client computer.
Several days later, you establish that the computer has been infected by malware. You are
unable to establish when the computer was infected.
You need to restore the client computer to full functionality.
What should you do?
Which two Group Policy settings should you configure?
A company has an Active Directory Domain Services (AD DS) domain. All client computers
run Windows 8.
You need to ensure that only administrators can access removable storage devices on client
computers.
Which two Group Policy settings should you configure? (Each correct answer presents part
of the solution. Choose two.)
Which two command-line tools should you use?
A company has client computers that run Windows 8. Each employee has one client
computer at the office. Some employees also have personal computers at home.
The company has applications that run only on Windows 8.
You need to deploy Windows To Go so that employees can run the applications on their
home computers.
Which two command-line tools should you use? (Each correct answer presents part of the
solution. Choose two.)
You need to quickly ensure that the application can run
A company has an Active Directory Domain Services (AD DS) domain. All client computers
run Windows 8 and are joined to the domain. All Sales department employees are members
of the Sales organizational unit (CU). AppLocker rules control the installation of applicatior
on client computers.
You create a new Group Policy object (GPO) to configure an AppLocker file hash rule. The
file hash rule allows an application to run and links the application to the Sales OU. Several
minutes later, you establish that the AppLocker rule is not present on some computers within
SalesOU and the application cannot run.
You need to quickly ensure that the application can run.
What should you do?
Which command should you use to create the custom recovery image?
You administer Windows 8 laptops in your company network.
You install several custom desktop applications on the laptops.
You need to create a custom recovery image for Windows to use when selecting the
Refresh your PC option. The custom recovery image must include the custom desktop
applications.
Which command should you use to create the custom recovery image?
Which two actions should you perform?
You administer Windows 8 client computers in your company network. A computer that is
used by non-administrator users has a directory named C:\Folder1.
A shared collection of Microsoft Excel files is stored in the C:\Folder directory, with
nonadministrator users being granted modify permissions to the directory.
You discover that some files have been incorrectly modified by a user.
You need to determine which user made changes to the directory’s folder’s files.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)

