Which settings should you request be modified in the APP1Deploy GPO?
###BeginCaseStudy###
Case Study: 8
Fourth Coffee
Scenario:
You are an enterprise desktop support technician for Fourth Coffee. The network contains a
single domain named fourthcoffee.com.
Physical Environment
The company has three offices. The offices are configured as shown in the following table.
The relevant servers are configured as shown in the following table.
The Web1 server is accessible only through the URL http://web1.fourthcoffee.local
Application Configurations.
Fourth Coffee deploys an application named App1 to users in the main office by using a
Group Policy object (GPO) named APP1Deploy. App1 requires that a drive named M be
mapped to
\\AppServer1\AppData$. App1 saves information on a local computer if drive M is
unavailable. All client computers have drive M.
Security Policy
The corporate security policy states that domain controllers can only be deployed in secure
data centers. Branch office 2 does not have a secure data center.
Client Configuration
All users connect remotely through VPN1. VPN1 is configured to accept only SSTP-based
VPN connections. All client computers receive IP configurations from DHCP. You recently
purchased 100 desktop computers from a new hardware vendor.
###EndCaseStudy###
The application support team reports that the App1 data of some users is not saved to AppServer1.
The team reports that the users deleted the mapped drive. You need to prevent the users from
deleting the mapped drive. Which settings should you request be modified in the APP1Deploy GPO?
You need to ensure that the users can access the shared folders if the WAN link fails
###BeginCaseStudy###
Case Study: 8
Fourth Coffee
Scenario:
You are an enterprise desktop support technician for Fourth Coffee. The network contains a
single domain named fourthcoffee.com.
Physical Environment
The company has three offices. The offices are configured as shown in the following table.
The relevant servers are configured as shown in the following table.
The Web1 server is accessible only through the URL http://web1.fourthcoffee.local
Application Configurations.
Fourth Coffee deploys an application named App1 to users in the main office by using a
Group Policy object (GPO) named APP1Deploy. App1 requires that a drive named M be
mapped to
\\AppServer1\AppData$. App1 saves information on a local computer if drive M is
unavailable. All client computers have drive M.
Security Policy
The corporate security policy states that domain controllers can only be deployed in secure
data centers. Branch office 2 does not have a secure data center.
Client Configuration
All users connect remotely through VPN1. VPN1 is configured to accept only SSTP-based
VPN connections. All client computers receive IP configurations from DHCP. You recently
purchased 100 desktop computers from a new hardware vendor.
###EndCaseStudy###
Users in branch office 2 map drives to shared folders on SRV1. The users report that they cannot
access files in the shared folders when the WAN link between branch office 2 and the main office is
unavailable. When they attempt to access the files, they are prompted to enter their credentials but
are denied access. You need to ensure that the users can access the shared folders if the WAN link
fails. What should you do?
What should you configure?
###BeginCaseStudy###
Case Study: 8
Fourth Coffee
Scenario:
You are an enterprise desktop support technician for Fourth Coffee. The network contains a
single domain named fourthcoffee.com.
Physical Environment
The company has three offices. The offices are configured as shown in the following table.
The relevant servers are configured as shown in the following table.
The Web1 server is accessible only through the URL http://web1.fourthcoffee.local
Application Configurations.
Fourth Coffee deploys an application named App1 to users in the main office by using a
Group Policy object (GPO) named APP1Deploy. App1 requires that a drive named M be
mapped to
\\AppServer1\AppData$. App1 saves information on a local computer if drive M is
unavailable. All client computers have drive M.
Security Policy
The corporate security policy states that domain controllers can only be deployed in secure
data centers. Branch office 2 does not have a secure data center.
Client Configuration
All users connect remotely through VPN1. VPN1 is configured to accept only SSTP-based
VPN connections. All client computers receive IP configurations from DHCP. You recently
purchased 100 desktop computers from a new hardware vendor.
###EndCaseStudy###
The help desk reports that the new computers experience intermittent failures that generate stop
errors. You need to collect all the critical errors from the new computers. What should you
configure?
What should you request?
###BeginCaseStudy###
Case Study: 8
Fourth Coffee
Scenario:
You are an enterprise desktop support technician for Fourth Coffee. The network contains a
single domain named fourthcoffee.com.
Physical Environment
The company has three offices. The offices are configured as shown in the following table.
The relevant servers are configured as shown in the following table.
The Web1 server is accessible only through the URL http://web1.fourthcoffee.local
Application Configurations.
Fourth Coffee deploys an application named App1 to users in the main office by using a
Group Policy object (GPO) named APP1Deploy. App1 requires that a drive named M be
mapped to
\\AppServer1\AppData$. App1 saves information on a local computer if drive M is
unavailable. All client computers have drive M.
Security Policy
The corporate security policy states that domain controllers can only be deployed in secure
data centers. Branch office 2 does not have a secure data center.
Client Configuration
All users connect remotely through VPN1. VPN1 is configured to accept only SSTP-based
VPN connections. All client computers receive IP configurations from DHCP. You recently
purchased 100 desktop computers from a new hardware vendor.
###EndCaseStudy###
VPN users report that they cannot access shared resources in the branch offices. They can access
shared resources in the main office. Users in the main office report that they can access shared
resources in the branch offices. You need to ensure that the VPN users can access shared resources
in the branch offices. What should you request?
You need to ensure that App1 runs on Windows 7 computers
###BeginCaseStudy###
Case Study: 9
Wingtip Toys Scenario:
You are an enterprise desktop support technician for Wingtip Toys. Wingtip Toys has two offices.
Active Directory Configuration
The network contains a single Active Directory domain. An Active Directory site exists for
each office. The network contains the organizational units (OUs) that are shown in the
following table.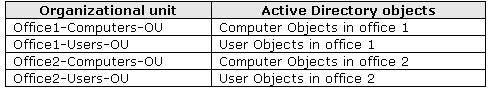
The network contains an enterprise root certification authority (CA). Certificate
autoenrollement is enabled for all users.
Network Configuration
Each office has a wireless network. You control access to the wireless network in office 1 by
using Network Access Protection (NAP). A Group Policy object (GPO) named GPO1
configures the NAP settings for the computers in office 1.
Resource Access
The Documents folders of all users are encrypted by using Encrypting File System (EFS).
The Documents folders of all users are backed up daily.
A Web server named Web1 hosts an internal Web site named WebSite1. Users connect to
WebSite1 from the Internet by using the URL http://website1.wingtiptoys.com. The domain
name website1.wingtiptoys.com is resolved by using the Hosts file that is located on each
client computer. Users frequently work from home. Home users connect to the internal
network by using SSTP-based VPN connections.
Line of Business Applications
Your company has a line-of-business application named App1. App1 is installed only on
computers that run Windows XP. You test App1 by using the Microsoft Application
Compatibility Toolkit (ACT). ACT reports that App1 can be made compatible to run on Windows 7.
###EndCaseStudy###
You deploy App1 on a test Windows 7 computer and notice that it fails to run. You need to ensure
that App1 runs on Windows 7 computers. What should you do?
You need to ensure that users can connect to website1.wingtiptoys.com from the Internet
###BeginCaseStudy###
Case Study: 9
Wingtip Toys Scenario:
You are an enterprise desktop support technician for Wingtip Toys. Wingtip Toys has two offices.
Active Directory Configuration
The network contains a single Active Directory domain. An Active Directory site exists for
each office. The network contains the organizational units (OUs) that are shown in the
following table.
The network contains an enterprise root certification authority (CA). Certificate
autoenrollement is enabled for all users.
Network Configuration
Each office has a wireless network. You control access to the wireless network in office 1 by
using Network Access Protection (NAP). A Group Policy object (GPO) named GPO1
configures the NAP settings for the computers in office 1.
Resource Access
The Documents folders of all users are encrypted by using Encrypting File System (EFS).
The Documents folders of all users are backed up daily.
A Web server named Web1 hosts an internal Web site named WebSite1. Users connect to
WebSite1 from the Internet by using the URL http://website1.wingtiptoys.com. The domain
name website1.wingtiptoys.com is resolved by using the Hosts file that is located on each
client computer. Users frequently work from home. Home users connect to the internal
network by using SSTP-based VPN connections.
Line of Business Applications
Your company has a line-of-business application named App1. App1 is installed only on
computers that run Windows XP. You test App1 by using the Microsoft Application
Compatibility Toolkit (ACT). ACT reports that App1 can be made compatible to run on Windows 7.
###EndCaseStudy###
An administrator modifies the external IP address of Web1 and creates a Hosts (A) record for
website1.wingtiptoys.com on the external DNS servers. Your users report that they can no longer
connect to website1.wingtiptoys.com from the Internet. You need to ensure that users can connect
to website1.wingtiptoys.com from the Internet. What should you do?
What should you request?
###BeginCaseStudy###
Case Study: 9
Wingtip Toys Scenario:
You are an enterprise desktop support technician for Wingtip Toys. Wingtip Toys has two offices.
Active Directory Configuration
The network contains a single Active Directory domain. An Active Directory site exists for
each office. The network contains the organizational units (OUs) that are shown in the
following table.
The network contains an enterprise root certification authority (CA). Certificate
autoenrollement is enabled for all users.
Network Configuration
Each office has a wireless network. You control access to the wireless network in office 1 by
using Network Access Protection (NAP). A Group Policy object (GPO) named GPO1
configures the NAP settings for the computers in office 1.
Resource Access
The Documents folders of all users are encrypted by using Encrypting File System (EFS).
The Documents folders of all users are backed up daily.
A Web server named Web1 hosts an internal Web site named WebSite1. Users connect to
WebSite1 from the Internet by using the URL http://website1.wingtiptoys.com. The domain
name website1.wingtiptoys.com is resolved by using the Hosts file that is located on each
client computer. Users frequently work from home. Home users connect to the internal
network by using SSTP-based VPN connections.
Line of Business Applications
Your company has a line-of-business application named App1. App1 is installed only on
computers that run Windows XP. You test App1 by using the Microsoft Application
Compatibility Toolkit (ACT). ACT reports that App1 can be made compatible to run on Windows 7.
###EndCaseStudy###
A group of users from office 2 travels to office 1 to work on a project. The users from office 2 report
that they are unable to connect to the wireless network in office 1 from their portable computers. A
help desk administrator manually provides the users with access to the wireless network. You need
to ensure that the next time users from office 2 travel to office 1 they can connect to the wireless
network in office 1. What should you request?
What should you recommend?
###BeginCaseStudy###
Case Study: 9
Wingtip Toys Scenario:
You are an enterprise desktop support technician for Wingtip Toys. Wingtip Toys has two offices.
Active Directory Configuration
The network contains a single Active Directory domain. An Active Directory site exists for
each office. The network contains the organizational units (OUs) that are shown in the
following table.
The network contains an enterprise root certification authority (CA). Certificate
autoenrollement is enabled for all users.
Network Configuration
Each office has a wireless network. You control access to the wireless network in office 1 by
using Network Access Protection (NAP). A Group Policy object (GPO) named GPO1
configures the NAP settings for the computers in office 1.
Resource Access
The Documents folders of all users are encrypted by using Encrypting File System (EFS).
The Documents folders of all users are backed up daily.
A Web server named Web1 hosts an internal Web site named WebSite1. Users connect to
WebSite1 from the Internet by using the URL http://website1.wingtiptoys.com. The domain
name website1.wingtiptoys.com is resolved by using the Hosts file that is located on each
client computer. Users frequently work from home. Home users connect to the internal
network by using SSTP-based VPN connections.
Line of Business Applications
Your company has a line-of-business application named App1. App1 is installed only on
computers that run Windows XP. You test App1 by using the Microsoft Application
Compatibility Toolkit (ACT). ACT reports that App1 can be made compatible to run on Windows 7.
###EndCaseStudy###
The help desk reports that they receive many calls from remote users who cannot access Internet
Web sites while they are connected to the VPN. The help desk instructs the users to manually
configure the VPN connection so that the users can access Internet Web sites while connected to the
VPN. You need to provide a recommendation to reduce the number of calls to the help desk
regarding this issue. What should you recommend?
What should you request?
###BeginCaseStudy###
Case Study: 9
Wingtip Toys Scenario:
You are an enterprise desktop support technician for Wingtip Toys. Wingtip Toys has two offices.
Active Directory Configuration
The network contains a single Active Directory domain. An Active Directory site exists for
each office. The network contains the organizational units (OUs) that are shown in the
following table.
The network contains an enterprise root certification authority (CA). Certificate
autoenrollement is enabled for all users.
Network Configuration
Each office has a wireless network. You control access to the wireless network in office 1 by
using Network Access Protection (NAP). A Group Policy object (GPO) named GPO1
configures the NAP settings for the computers in office 1.
Resource Access
The Documents folders of all users are encrypted by using Encrypting File System (EFS).
The Documents folders of all users are backed up daily.
A Web server named Web1 hosts an internal Web site named WebSite1. Users connect to
WebSite1 from the Internet by using the URL http://website1.wingtiptoys.com. The domain
name website1.wingtiptoys.com is resolved by using the Hosts file that is located on each
client computer. Users frequently work from home. Home users connect to the internal
network by using SSTP-based VPN connections.
Line of Business Applications
Your company has a line-of-business application named App1. App1 is installed only on
computers that run Windows XP. You test App1 by using the Microsoft Application
Compatibility Toolkit (ACT). ACT reports that App1 can be made compatible to run on Windows 7.
###EndCaseStudy###
A user’s computer fails. The help desk provides the user with a new computer. The user’s Documents
folder is restored from the backup. The user reports that he can no longer access his encrypted files.
The help desk recovers the files by using a data recovery agent (DRA). You need to ensure that when
users receive new computers, they can access their encrypted files without administrative
intervention. What should you request?
What should you instruct the users to do?
###BeginCaseStudy###
Case Study: 10
Humongous Insurance
Scenario:
You are an enterprise desktop support technician for Humongous Insurance.
Active Directory Configuration
The company has two offices named Office1 and Office2.
The network contains an Active Directory forest named humongousinsurance.com. An
Active Directory site exists for each office. The sites are named Site1 and Site2.
Server Configuration
All servers run Windows Server 2008 R2 and are joined to the domain. The relevant servers
are configured as shown in the following table.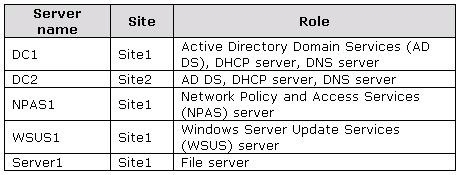
The corporate security policy states that all domain controllers must have only the following roles:
• AD DS
• DNS server
• DHCP server
Network Configuration
Site1 and Site2 connect to each other by using a WAN link.
Client Computer Configuration
All client computers run Windows 7 Enterprise and are members of the domain. Some client
computers are portable computers and some are desktop computers. The computers do not
support hardware virtualization.
All computers are configured to receive Windows Updates from WSUS1.
Remote Access Configuration
Users can connect to NPAS1 from the Internet by using all of the VPN protocols that are
supported by Windows Server 2008 R2.
Fabrikam, Inc. is a customer of Humongous Insurance. Several Humongous Insurance users
work at the Fabrikam office and access resources on the Humongous Insurance network by
using direct VPN connections to NPAS1. Fabrikam contains several wireless access points.
Application Configuration
All computers in the finance department run a custom application suite named App1.
Several users in the sales department install an application named App2. App2 runs as a
service and logs on by using the credentials of the user who installed the application.
###EndCaseStudy###
Several users in the sales department report that their user accounts are locked out shortly after
they change their user passwords. You need to minimize the number of account lockouts that occur
after the users change their passwords. What should you instruct the users to do?

