Which two actions should you perform?
###BeginCaseStudy###
Case Study: 15
Trey Research
COMPANY OVERVIEW
Trey Research is a data warehousing company that has three data centers named Datacenter1,
Datacenter2, and Datacenter3. The data centers are located in different cities.
Trey recently acquired another company named A. Datum Corporation.
PLANNED CHANGES
Several applications are installed on the internal network servers. Trey Research plans to make the
applications accessible to the users who work from home.
Trey Research plans to migrate all of the user accounts in the adatum.com and east.adatum.com
domains to treyreseach.com.
Trey Research plans to deploy smart cards to all of the users on the network.
Trey Research plans to deploy a document storage solution that meets the following requirements:
The solution must be accessible to all client computers by using a Web browser.
The solution must be able to notify administrators when sensitive documents are modified.
Trey Research plans to deploy a Failover Clustering solution to host a Web application named
WebAppl, WebAppl must meet the following requirements:
Remain available if a single server fails.
Remain available if a single data center fails.
EXISTING ENVIRONMENT
Business Goals
Changes to the environment must require minimal hardware and software costs.
Existing Active Directory Environment
The network contains two Active Directory forests named treyresearch.com and adatum.com. A
two-way forest trust exists between the forests.
Adatum.com contains two domains named adatum.com and east.adatum.com. Treyreasearch.com
contains a single domain.
The network contains an internal enterprise root certification authority (CA).
Existing Network Infrastructure
The network contains client computers that run either Windows 7 or a UNIX-based operating
system. Some users work from home on client computers that are members of a workgroup.
REQUIREMENTS
Technical Requirements
Trey Research must meet the following technical requirements:
Users who work from home must be able to use local print devices.
The amount of disk space used on the users’ home computers must be minimized.
Users who work from home must have the same desktop experience as users who are connected to
the internal network.
Users must be able to access the shares in the adatum.com domain after their user accounts are
migrated to treyresearch.com.
Security Requirements
Trey Research must meet the following security requirements:
If a user forgets his or her password, he or she must be able to reset the password on his or her own.
If a user forgets his or her smart card PIN, he or she must be able to reset the PIN on his or her own.
###EndCaseStudy###
You need to ensure that the migration of the user accounts from adatum.com and east.adatum.com
to treyresearch.com meets the company’s technical requirements.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 15
Trey Research
COMPANY OVERVIEW
Trey Research is a data warehousing company that has three data centers named Datacenter1,
Datacenter2, and Datacenter3. The data centers are located in different cities.
Trey recently acquired another company named A. Datum Corporation.
PLANNED CHANGES
Several applications are installed on the internal network servers. Trey Research plans to make the
applications accessible to the users who work from home.
Trey Research plans to migrate all of the user accounts in the adatum.com and east.adatum.com
domains to treyreseach.com.
Trey Research plans to deploy smart cards to all of the users on the network.
Trey Research plans to deploy a document storage solution that meets the following requirements:
The solution must be accessible to all client computers by using a Web browser.
The solution must be able to notify administrators when sensitive documents are modified.
Trey Research plans to deploy a Failover Clustering solution to host a Web application named
WebAppl, WebAppl must meet the following requirements:
Remain available if a single server fails.
Remain available if a single data center fails.
EXISTING ENVIRONMENT
Business Goals
Changes to the environment must require minimal hardware and software costs.
Existing Active Directory Environment
The network contains two Active Directory forests named treyresearch.com and adatum.com. A
two-way forest trust exists between the forests.
Adatum.com contains two domains named adatum.com and east.adatum.com. Treyreasearch.com
contains a single domain.
The network contains an internal enterprise root certification authority (CA).
Existing Network Infrastructure
The network contains client computers that run either Windows 7 or a UNIX-based operating
system. Some users work from home on client computers that are members of a workgroup.
REQUIREMENTS
Technical Requirements
Trey Research must meet the following technical requirements:
Users who work from home must be able to use local print devices.
The amount of disk space used on the users’ home computers must be minimized.
Users who work from home must have the same desktop experience as users who are connected to
the internal network.
Users must be able to access the shares in the adatum.com domain after their user accounts are
migrated to treyresearch.com.
Security Requirements
Trey Research must meet the following security requirements:
If a user forgets his or her password, he or she must be able to reset the password on his or her own.
If a user forgets his or her smart card PIN, he or she must be able to reset the PIN on his or her own.
###EndCaseStudy###
You need to recommend an access solution for the users who work at home that meets the
company’s technical requirements.
What should you include in the recommendation?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 15
Trey Research
COMPANY OVERVIEW
Trey Research is a data warehousing company that has three data centers named Datacenter1,
Datacenter2, and Datacenter3. The data centers are located in different cities.
Trey recently acquired another company named A. Datum Corporation.
PLANNED CHANGES
Several applications are installed on the internal network servers. Trey Research plans to make the
applications accessible to the users who work from home.
Trey Research plans to migrate all of the user accounts in the adatum.com and east.adatum.com
domains to treyreseach.com.
Trey Research plans to deploy smart cards to all of the users on the network.
Trey Research plans to deploy a document storage solution that meets the following requirements:
The solution must be accessible to all client computers by using a Web browser.
The solution must be able to notify administrators when sensitive documents are modified.
Trey Research plans to deploy a Failover Clustering solution to host a Web application named
WebAppl, WebAppl must meet the following requirements:
Remain available if a single server fails.
Remain available if a single data center fails.
EXISTING ENVIRONMENT
Business Goals
Changes to the environment must require minimal hardware and software costs.
Existing Active Directory Environment
The network contains two Active Directory forests named treyresearch.com and adatum.com. A
two-way forest trust exists between the forests.
Adatum.com contains two domains named adatum.com and east.adatum.com. Treyreasearch.com
contains a single domain.
The network contains an internal enterprise root certification authority (CA).
Existing Network Infrastructure
The network contains client computers that run either Windows 7 or a UNIX-based operating
system. Some users work from home on client computers that are members of a workgroup.
REQUIREMENTS
Technical Requirements
Trey Research must meet the following technical requirements:
Users who work from home must be able to use local print devices.
The amount of disk space used on the users’ home computers must be minimized.
Users who work from home must have the same desktop experience as users who are connected to
the internal network.
Users must be able to access the shares in the adatum.com domain after their user accounts are
migrated to treyresearch.com.
Security Requirements
Trey Research must meet the following security requirements:
If a user forgets his or her password, he or she must be able to reset the password on his or her own.
If a user forgets his or her smart card PIN, he or she must be able to reset the PIN on his or her own.
###EndCaseStudy###
You need to recommend a Failover Clustering solution that supports the company’s planned
changes.
What should you include in the recommendation?
You need to add a server to the existing Remote Desktop Session Host server farm
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
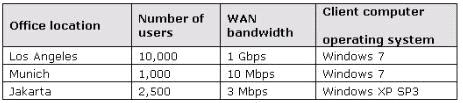
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
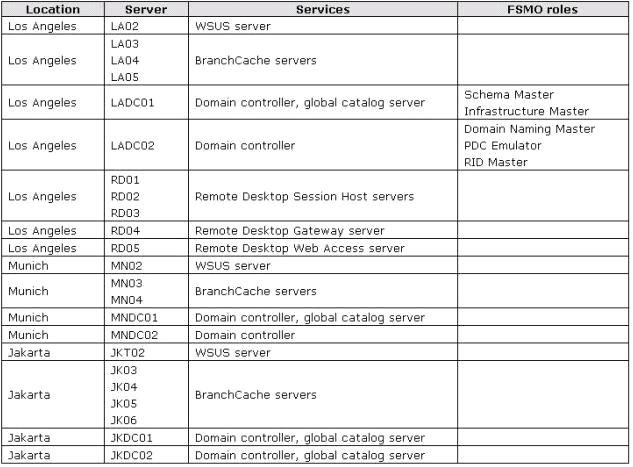
The company’s servers include those shown in the following table.
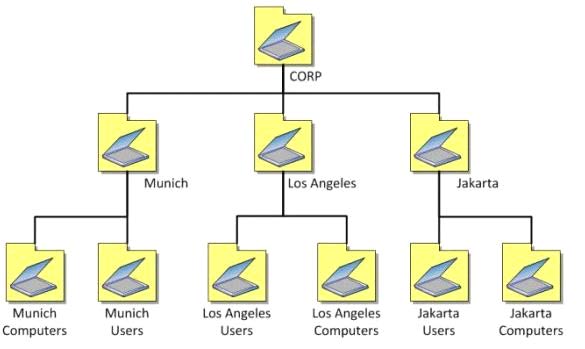
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to add a server to the existing Remote Desktop Session Host server farm.
What should you do?
You need to resolve the problem
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You create the new wireless network for the Jakarta office.
The network link between the Los Angeles and Jakarta offices becomes congested after users start
connecting to the new wireless network.
You need to resolve the problem.
What should you do?
You need to design the deployment for the retail locations
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to design the deployment for the retail locations.
What should you do? (Each correct answer presents part of the solution. Choose two.)
Which subnet mask should you use?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You are planning to deploy the new network in Munich.
Which subnet mask should you use?
You need to resolve the problem
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You create the new wireless network for the Jakarta office.
The network link between the Los Angeles and Jakarta offices becomes congested after users start
connecting to the new wireless network.
You need to resolve the problem.
What should you do?
Which subnet mask should you use?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You are planning to deploy the new network in Munich.
Which subnet mask should you use?
which server or servers should you install certificates?
###BeginCaseStudy###
Case Study: 16
Wingtip Toys Case B
General Background
You are the Enterprise Administrator for Wingtip Toys. The company has a main office and two
branch offices, as described in the following table.
Wingtip Toys is planning the acquisition of Tailspin Toys. The acquisition will add 100 users to the Los
Angeles office, 10 users to the Munich office, and 6,000 users to the Jakarta office. As part of the
acquisition, seven new buildings will be added to the existing Jakarta office complex.
Technical Background
Wingtip Toys has an Active Directory Domain Services (AD DS) domain with a NETBIOS name of CORP
and a DNS name ofwingtiptoys.com. Each office is represented by an Active Directory site. AD
operational tasks such as schema changes, domain additions, and computer and user object creation
are performed in the Los Angeles office.
DHCP servers are centrally located in the Los Angeles office. All DHCP servers run Windows Server
2008 R2 in a failover cluster configuration.
The company uses Windows Server Update Services (WSUS) to distribute updates.
A Remote Desktop Services (RDS) farm located in Los Angeles includes a load-balanced host named
RD.wingtiptoys.com.
The company’s servers include those shown in the following table.
An application named App1 is installed on RD01, RD02, and RD03. Organizational units (OUs) are
created as shown in the following diagram.
The company has reserved the 172.16.0.0/16 network IP range to support a future wireless network
in Jakarta.
A public web server named WEB1 is located on a dedicated subnet in the Los Angeles office. The
dedicated subnet is enabled for Network Address Translation (NAT) with IP address port forwarding
to WEB1. No servers on the dedicated NAT subnet are members of any domain.
Each site deploys wired network segments with class C subnets as necessary.
Business requirements
You have the following business requirements:
Provide the highest possible level of security for all new computing services. All external connections
must be encrypted.
Utilize a single network administration topology.
Centralize Active Directory administration in the Los Angeles office.
Wingtip Toys is planning to set up several retail locations around Jakarta. The retail locations do not
have physically secure areas for servers and networking equipment. You must minimize logon time
for retail location employees and minimize the security impact in the event of a server theft at the
retail location.
Technical Requirements
To support the acquisition, you plan to deploy the following items:
A new AD DS environment.
A dual-stack implementation of IPv6 networking in the Munich office.
A new perimeter network dedicated for public web servers.
The computing environment must meet the following requirements:
Each office must have at least one domain controller per physical location.
There must be one global catalog server for every 1000 users.
Computer policies for the perimeter network must be enforced without exposing internal user
account credentials.
The perimeter networks must not allow connections to computers or accounts on the CORP
network.
All software updates must be distributed from Los Angeles.
All client computers must acquire IP addresses from DHCP.
Users in the Munich office must have full Internet access.
All users must have remote web access to Appl.
Force all new users to change their password on first login.
###EndCaseStudy###
You need to meet the remote application and administration requirements.
On which server or servers should you install certificates?