What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 7
Woodgrove Bank
Company Overview
Woodgrove Bank is an international investment banking institution. Woodgrove Bank has a partner
company named Contoso, Ltd.
Physical Location
Woodgrove Bank has a main office and 10 branch office. Each branch office has a WAN link to the
main office.
Existing Environment
Active Directory Environment
The Woodgrove Bank network contains an Active Directory forest named woodgrovebank.com. The
forest contains multiple domains and one Active Directory site. The functional level of the forest is
Windows Server 2003.
Each office has domain controllers for the forest root domain. Each office also contains domain
controllers for at least one other domain.
The Contoso network contains an Active Directory forest. The forest contains one domain named
contoso.com. The functional level of the domain is Windows Server 2003.
Network Infrastructure
The woodgrove Bank network contains the following applications and servers:
• A line-of-business application named App1.
• Servers that run either Windows Server 2003 or Windows Server 2008.
• Domain controllers in the main office run Windows Server 2003.
• An enterprise root certification authority (CA) that runs Windows Server 2003. The
certificate revocation list (CRL) is published to an internal Web site.
All client computers in the contoso.com run a 64-bit version of Windows 7.
Security Model
Users in Woodgrove Bank’s research department are required to use smart card authenticate to log
on to the network.
Requirements
Planned Changes
Woodgrove Bank plans to implement the following changes:
• Provide Contoso users access to App1.
• Deploy a satellite office that will have one domain controller.
• Provide users in both companies access to the resources in either forest by using a single set
of credentials.
• Implement e-mail notification for department managers when new versions of shared
documents are saved to a network location.
Technical Requirements
All users in the planned satellite office must always attempt to authenticate to their local domain
controller first.
Security Requirements
• Woodgrove Bank must meet the following security requirements:
• Server in contoso.com must be able to trust certificates issued by the CA of
woodgrovebank.com.
• App1 must only be available to Contoso users when the users are connected to the
Woodgrove Bank network.
• Users in contoso.com must be able to automatically enroll for certificates from the CA of
Woodgrove Bank.
• Internal auditors must have full administrative rights on all client computers in the finance
department.
• Only client computers that have Microsoft Forefront EndPoint Protection installed must be
able to remotely connect to the Woodgrove Bank network.
###EndCaseStudy###
You are evaluating the deployment of a domain controller in the planned satellite office.
You need to recommend changes to the physical topology of Active Directory that meet the
company’s technical requirements.
What should you include in the recommendation?
What should you recommend?
###BeginCaseStudy###
Case Study: 7
Woodgrove Bank
Company Overview
Woodgrove Bank is an international investment banking institution. Woodgrove Bank has a partner
company named Contoso, Ltd.
Physical Location
Woodgrove Bank has a main office and 10 branch office. Each branch office has a WAN link to the
main office.
Existing Environment
Active Directory Environment
The Woodgrove Bank network contains an Active Directory forest named woodgrovebank.com. The
forest contains multiple domains and one Active Directory site. The functional level of the forest is
Windows Server 2003.
Each office has domain controllers for the forest root domain. Each office also contains domain
controllers for at least one other domain.
The Contoso network contains an Active Directory forest. The forest contains one domain named
contoso.com. The functional level of the domain is Windows Server 2003.
Network Infrastructure
The woodgrove Bank network contains the following applications and servers:
• A line-of-business application named App1.
• Servers that run either Windows Server 2003 or Windows Server 2008.
• Domain controllers in the main office run Windows Server 2003.
• An enterprise root certification authority (CA) that runs Windows Server 2003. The
certificate revocation list (CRL) is published to an internal Web site.
All client computers in the contoso.com run a 64-bit version of Windows 7.
Security Model
Users in Woodgrove Bank’s research department are required to use smart card authenticate to log
on to the network.
Requirements
Planned Changes
Woodgrove Bank plans to implement the following changes:
• Provide Contoso users access to App1.
• Deploy a satellite office that will have one domain controller.
• Provide users in both companies access to the resources in either forest by using a single set
of credentials.
• Implement e-mail notification for department managers when new versions of shared
documents are saved to a network location.
Technical Requirements
All users in the planned satellite office must always attempt to authenticate to their local domain
controller first.
Security Requirements
• Woodgrove Bank must meet the following security requirements:
• Server in contoso.com must be able to trust certificates issued by the CA of
woodgrovebank.com.
• App1 must only be available to Contoso users when the users are connected to the
Woodgrove Bank network.
• Users in contoso.com must be able to automatically enroll for certificates from the CA of
Woodgrove Bank.
• Internal auditors must have full administrative rights on all client computers in the finance
department.
• Only client computers that have Microsoft Forefront EndPoint Protection installed must be
able to remotely connect to the Woodgrove Bank network.
###EndCaseStudy###
You are evaluating implementing a high-availability solution for smart card authentication.
You need to recommend changes to the network infrastructure to ensure that all research
department users can log on if a single server fails.
What should you recommend?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 7
Woodgrove Bank
Company Overview
Woodgrove Bank is an international investment banking institution. Woodgrove Bank has a partner
company named Contoso, Ltd.
Physical Location
Woodgrove Bank has a main office and 10 branch office. Each branch office has a WAN link to the
main office.
Existing Environment
Active Directory Environment
The Woodgrove Bank network contains an Active Directory forest named woodgrovebank.com. The
forest contains multiple domains and one Active Directory site. The functional level of the forest is
Windows Server 2003.
Each office has domain controllers for the forest root domain. Each office also contains domain
controllers for at least one other domain.
The Contoso network contains an Active Directory forest. The forest contains one domain named
contoso.com. The functional level of the domain is Windows Server 2003.
Network Infrastructure
The woodgrove Bank network contains the following applications and servers:
• A line-of-business application named App1.
• Servers that run either Windows Server 2003 or Windows Server 2008.
• Domain controllers in the main office run Windows Server 2003.
• An enterprise root certification authority (CA) that runs Windows Server 2003. The
certificate revocation list (CRL) is published to an internal Web site.
All client computers in the contoso.com run a 64-bit version of Windows 7.
Security Model
Users in Woodgrove Bank’s research department are required to use smart card authenticate to log
on to the network.
Requirements
Planned Changes
Woodgrove Bank plans to implement the following changes:
• Provide Contoso users access to App1.
• Deploy a satellite office that will have one domain controller.
• Provide users in both companies access to the resources in either forest by using a single set
of credentials.
• Implement e-mail notification for department managers when new versions of shared
documents are saved to a network location.
Technical Requirements
All users in the planned satellite office must always attempt to authenticate to their local domain
controller first.
Security Requirements
• Woodgrove Bank must meet the following security requirements:
• Server in contoso.com must be able to trust certificates issued by the CA of
woodgrovebank.com.
• App1 must only be available to Contoso users when the users are connected to the
Woodgrove Bank network.
• Users in contoso.com must be able to automatically enroll for certificates from the CA of
Woodgrove Bank.
• Internal auditors must have full administrative rights on all client computers in the finance
department.
• Only client computers that have Microsoft Forefront EndPoint Protection installed must be
able to remotely connect to the Woodgrove Bank network.
###EndCaseStudy###
You need to recommend a document management solution that supports the company’s planned
changes for the department managers.
What should you include in the recommendation?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 7
Woodgrove Bank
Company Overview
Woodgrove Bank is an international investment banking institution. Woodgrove Bank has a partner
company named Contoso, Ltd.
Physical Location
Woodgrove Bank has a main office and 10 branch office. Each branch office has a WAN link to the
main office.
Existing Environment
Active Directory Environment
The Woodgrove Bank network contains an Active Directory forest named woodgrovebank.com. The
forest contains multiple domains and one Active Directory site. The functional level of the forest is
Windows Server 2003.
Each office has domain controllers for the forest root domain. Each office also contains domain
controllers for at least one other domain.
The Contoso network contains an Active Directory forest. The forest contains one domain named
contoso.com. The functional level of the domain is Windows Server 2003.
Network Infrastructure
The woodgrove Bank network contains the following applications and servers:
• A line-of-business application named App1.
• Servers that run either Windows Server 2003 or Windows Server 2008.
• Domain controllers in the main office run Windows Server 2003.
• An enterprise root certification authority (CA) that runs Windows Server 2003. The
certificate revocation list (CRL) is published to an internal Web site.
All client computers in the contoso.com run a 64-bit version of Windows 7.
Security Model
Users in Woodgrove Bank’s research department are required to use smart card authenticate to log
on to the network.
Requirements
Planned Changes
Woodgrove Bank plans to implement the following changes:
• Provide Contoso users access to App1.
• Deploy a satellite office that will have one domain controller.
• Provide users in both companies access to the resources in either forest by using a single set
of credentials.
• Implement e-mail notification for department managers when new versions of shared
documents are saved to a network location.
Technical Requirements
All users in the planned satellite office must always attempt to authenticate to their local domain
controller first.
Security Requirements
• Woodgrove Bank must meet the following security requirements:
• Server in contoso.com must be able to trust certificates issued by the CA of
woodgrovebank.com.
• App1 must only be available to Contoso users when the users are connected to the
Woodgrove Bank network.
• Users in contoso.com must be able to automatically enroll for certificates from the CA of
Woodgrove Bank.
• Internal auditors must have full administrative rights on all client computers in the finance
department.
• Only client computers that have Microsoft Forefront EndPoint Protection installed must be
able to remotely connect to the Woodgrove Bank network.
###EndCaseStudy###
You are evaluating implementing a solution for the internal auditors.
You need to recommend a solution to delegate the appropriate rights to the auditors.
What should you include in the recommendation?
What should you recommend?
###BeginCaseStudy###
Case Study: 7
Woodgrove Bank
Company Overview
Woodgrove Bank is an international investment banking institution. Woodgrove Bank has a partner
company named Contoso, Ltd.
Physical Location
Woodgrove Bank has a main office and 10 branch office. Each branch office has a WAN link to the
main office.
Existing Environment
Active Directory Environment
The Woodgrove Bank network contains an Active Directory forest named woodgrovebank.com. The
forest contains multiple domains and one Active Directory site. The functional level of the forest is
Windows Server 2003.
Each office has domain controllers for the forest root domain. Each office also contains domain
controllers for at least one other domain.
The Contoso network contains an Active Directory forest. The forest contains one domain named
contoso.com. The functional level of the domain is Windows Server 2003.
Network Infrastructure
The woodgrove Bank network contains the following applications and servers:
• A line-of-business application named App1.
• Servers that run either Windows Server 2003 or Windows Server 2008.
• Domain controllers in the main office run Windows Server 2003.
• An enterprise root certification authority (CA) that runs Windows Server 2003. The
certificate revocation list (CRL) is published to an internal Web site.
All client computers in the contoso.com run a 64-bit version of Windows 7.
Security Model
Users in Woodgrove Bank’s research department are required to use smart card authenticate to log
on to the network.
Requirements
Planned Changes
Woodgrove Bank plans to implement the following changes:
• Provide Contoso users access to App1.
• Deploy a satellite office that will have one domain controller.
• Provide users in both companies access to the resources in either forest by using a single set
of credentials.
• Implement e-mail notification for department managers when new versions of shared
documents are saved to a network location.
Technical Requirements
All users in the planned satellite office must always attempt to authenticate to their local domain
controller first.
Security Requirements
• Woodgrove Bank must meet the following security requirements:
• Server in contoso.com must be able to trust certificates issued by the CA of
woodgrovebank.com.
• App1 must only be available to Contoso users when the users are connected to the
Woodgrove Bank network.
• Users in contoso.com must be able to automatically enroll for certificates from the CA of
Woodgrove Bank.
• Internal auditors must have full administrative rights on all client computers in the finance
department.
• Only client computers that have Microsoft Forefront EndPoint Protection installed must be
able to remotely connect to the Woodgrove Bank network.
###EndCaseStudy###
You are evaluating implementing fine-grained password policies on the Woodgrove Bank network.
You need to recommend changes to the network to ensure that the fine-grained password policies
can be used.
What should you recommend?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 8
Blue yonder Airlines
COMPANY OVERVIEW
Blue Yonder Airlines has a main office and four branch offices.
PLANNED CHANGES
Blue Yonder Airlines plans to implement the following changes:
• Upgrade all client computers to Windows 7.
• Deploy a virtualization solution for the company’s developers.
• Implement coexistence between the users in Fabrikam and the users in Blue Yonder Airlines.
EXISTING ENVIRONMENT
One user in each office runs a point-of-sale (POS) application named Appl. App 1 requires access to a
local USB device and only runs on Windows XP Service Pack 3 (SP3).
Blue Yonder Airlines has a finance department.
Business Goals
Blue Yonder Airlines plans to acquire a company named Fabrikam, Inc. Fabrikam has an Active
Directory forest named fabrikam.com. Fabrikam.com contains only domain controllers that run
Windows Server 2003 Service Pack 2 (SP2).
Fabrikam.com contains multiple Web servers that are secured by using certificates. All server
certificates are issued by the internal CA of Fabrikam.
Existing Active Directory Environment
The network contains an Active Directory forest named blueyonderairlines.com. The forest contains
a single domain.
The domain contains domain controllers that run Windows Server 2008. The domain controllers are
configured as shown in the following table.
The forest contains a single Active Directory site. A subnet object is defined for each office.
The forest contains a certification authority (CA).
Existing Network Infrastructure
Each office has a file server and a print server.
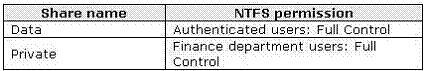
The main office has a file server named Server1. The shared folders on Server1 are configured as
shown in the following table.
Blueyonderairlines.com has a standalone DFS root named \\serverl\corp that contains a link named
sales. Replicas of \\serverl\corp\sales are deployed in each office.
Current Administration Model
Administrators manage the Active Directory objects by using the Active Directory module for
Windows Power Shell.
TECHNICAL REQUIREMENTS
Blue Yonder Airlines must meet the following requirements for coexistence between Blue Yonder
Airlines and Fabrikam:
• Only specific users in Fabrikam must be allowed to access specific shares in
blueyonderairlines.com.
• Users in Blue Yonder Airlines must be able to access the secure Web servers in fabrikam.com
without receiving a warning message about the certificate.
• All administrators in Blue Yonder Airlines must be able to administer Active Directory objects
in fabrikam.com by using their default administrative tools.
The corporate security policy states that when a domain controller fails, all references to the domain
controller must be permanently removed from the domain before the domain controller is replaced.
Blue Yonder Airlines must meet the following virtualization requirements:
• Ensure that each developer can create and manage his own virtual machine (VM).
• Prevent the developers from configuring the settings of other developers’ VMs.
• Prevent the developers from creating VMs that use more than 2 GB of memory,
• Minimize the amount of bandwidth used when users access files over WAN links.
###EndCaseStudy###
You need recommend a software solution for App1 that supports the company’s planned changes.
What should you include in the recommendation?
Which two tasks should you recommend?
###BeginCaseStudy###
Case Study: 8
Blue yonder Airlines
COMPANY OVERVIEW
Blue Yonder Airlines has a main office and four branch offices.
PLANNED CHANGES
Blue Yonder Airlines plans to implement the following changes:
• Upgrade all client computers to Windows 7.
• Deploy a virtualization solution for the company’s developers.
• Implement coexistence between the users in Fabrikam and the users in Blue Yonder Airlines.
EXISTING ENVIRONMENT
One user in each office runs a point-of-sale (POS) application named Appl. App 1 requires access to a
local USB device and only runs on Windows XP Service Pack 3 (SP3).
Blue Yonder Airlines has a finance department.
Business Goals
Blue Yonder Airlines plans to acquire a company named Fabrikam, Inc. Fabrikam has an Active
Directory forest named fabrikam.com. Fabrikam.com contains only domain controllers that run
Windows Server 2003 Service Pack 2 (SP2).
Fabrikam.com contains multiple Web servers that are secured by using certificates. All server
certificates are issued by the internal CA of Fabrikam.
Existing Active Directory Environment
The network contains an Active Directory forest named blueyonderairlines.com. The forest contains
a single domain.
The domain contains domain controllers that run Windows Server 2008. The domain controllers are
configured as shown in the following table.
The forest contains a single Active Directory site. A subnet object is defined for each office.
The forest contains a certification authority (CA).
Existing Network Infrastructure
Each office has a file server and a print server.
The main office has a file server named Server1. The shared folders on Server1 are configured as
shown in the following table.
Blueyonderairlines.com has a standalone DFS root named \\serverl\corp that contains a link named
sales. Replicas of \\serverl\corp\sales are deployed in each office.
Current Administration Model
Administrators manage the Active Directory objects by using the Active Directory module for
Windows Power Shell.
TECHNICAL REQUIREMENTS
Blue Yonder Airlines must meet the following requirements for coexistence between Blue Yonder
Airlines and Fabrikam:
• Only specific users in Fabrikam must be allowed to access specific shares in
blueyonderairlines.com.
• Users in Blue Yonder Airlines must be able to access the secure Web servers in fabrikam.com
without receiving a warning message about the certificate.
• All administrators in Blue Yonder Airlines must be able to administer Active Directory objects
in fabrikam.com by using their default administrative tools.
The corporate security policy states that when a domain controller fails, all references to the domain
controller must be permanently removed from the domain before the domain controller is replaced.
Blue Yonder Airlines must meet the following virtualization requirements:
• Ensure that each developer can create and manage his own virtual machine (VM).
• Prevent the developers from configuring the settings of other developers’ VMs.
• Prevent the developers from creating VMs that use more than 2 GB of memory,
• Minimize the amount of bandwidth used when users access files over WAN links.
###EndCaseStudy###
You need to recommend an interoperability strategy for the Blue Yonder Airlines administrator that
meets the company’s technical requirements.
Which two tasks should you recommend? (Each correct answer presents part of the solution.)
(Choose two.)
What should you recommend?
###BeginCaseStudy###
Case Study: 8
Blue yonder Airlines
COMPANY OVERVIEW
Blue Yonder Airlines has a main office and four branch offices.
PLANNED CHANGES
Blue Yonder Airlines plans to implement the following changes:
• Upgrade all client computers to Windows 7.
• Deploy a virtualization solution for the company’s developers.
• Implement coexistence between the users in Fabrikam and the users in Blue Yonder Airlines.
EXISTING ENVIRONMENT
One user in each office runs a point-of-sale (POS) application named Appl. App 1 requires access to a
local USB device and only runs on Windows XP Service Pack 3 (SP3).
Blue Yonder Airlines has a finance department.
Business Goals
Blue Yonder Airlines plans to acquire a company named Fabrikam, Inc. Fabrikam has an Active
Directory forest named fabrikam.com. Fabrikam.com contains only domain controllers that run
Windows Server 2003 Service Pack 2 (SP2).
Fabrikam.com contains multiple Web servers that are secured by using certificates. All server
certificates are issued by the internal CA of Fabrikam.
Existing Active Directory Environment
The network contains an Active Directory forest named blueyonderairlines.com. The forest contains
a single domain.
The domain contains domain controllers that run Windows Server 2008. The domain controllers are
configured as shown in the following table.
The forest contains a single Active Directory site. A subnet object is defined for each office.
The forest contains a certification authority (CA).
Existing Network Infrastructure
Each office has a file server and a print server.
The main office has a file server named Server1. The shared folders on Server1 are configured as
shown in the following table.
Blueyonderairlines.com has a standalone DFS root named \\serverl\corp that contains a link named
sales. Replicas of \\serverl\corp\sales are deployed in each office.
Current Administration Model
Administrators manage the Active Directory objects by using the Active Directory module for
Windows Power Shell.
TECHNICAL REQUIREMENTS
Blue Yonder Airlines must meet the following requirements for coexistence between Blue Yonder
Airlines and Fabrikam:
• Only specific users in Fabrikam must be allowed to access specific shares in
blueyonderairlines.com.
• Users in Blue Yonder Airlines must be able to access the secure Web servers in fabrikam.com
without receiving a warning message about the certificate.
• All administrators in Blue Yonder Airlines must be able to administer Active Directory objects
in fabrikam.com by using their default administrative tools.
The corporate security policy states that when a domain controller fails, all references to the domain
controller must be permanently removed from the domain before the domain controller is replaced.
Blue Yonder Airlines must meet the following virtualization requirements:
• Ensure that each developer can create and manage his own virtual machine (VM).
• Prevent the developers from configuring the settings of other developers’ VMs.
• Prevent the developers from creating VMs that use more than 2 GB of memory,
• Minimize the amount of bandwidth used when users access files over WAN links.
###EndCaseStudy###
You need to recommend a certificate strategy that meets the company’s technical requirements.
What should you recommend?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 8
Blue yonder Airlines
COMPANY OVERVIEW
Blue Yonder Airlines has a main office and four branch offices.
PLANNED CHANGES
Blue Yonder Airlines plans to implement the following changes:
• Upgrade all client computers to Windows 7.
• Deploy a virtualization solution for the company’s developers.
• Implement coexistence between the users in Fabrikam and the users in Blue Yonder Airlines.
EXISTING ENVIRONMENT
One user in each office runs a point-of-sale (POS) application named Appl. App 1 requires access to a
local USB device and only runs on Windows XP Service Pack 3 (SP3).
Blue Yonder Airlines has a finance department.
Business Goals
Blue Yonder Airlines plans to acquire a company named Fabrikam, Inc. Fabrikam has an Active
Directory forest named fabrikam.com. Fabrikam.com contains only domain controllers that run
Windows Server 2003 Service Pack 2 (SP2).
Fabrikam.com contains multiple Web servers that are secured by using certificates. All server
certificates are issued by the internal CA of Fabrikam.
Existing Active Directory Environment
The network contains an Active Directory forest named blueyonderairlines.com. The forest contains
a single domain.
The domain contains domain controllers that run Windows Server 2008. The domain controllers are
configured as shown in the following table.
The forest contains a single Active Directory site. A subnet object is defined for each office.
The forest contains a certification authority (CA).
Existing Network Infrastructure
Each office has a file server and a print server.
The main office has a file server named Server1. The shared folders on Server1 are configured as
shown in the following table.
Blueyonderairlines.com has a standalone DFS root named \\serverl\corp that contains a link named
sales. Replicas of \\serverl\corp\sales are deployed in each office.
Current Administration Model
Administrators manage the Active Directory objects by using the Active Directory module for
Windows Power Shell.
TECHNICAL REQUIREMENTS
Blue Yonder Airlines must meet the following requirements for coexistence between Blue Yonder
Airlines and Fabrikam:
• Only specific users in Fabrikam must be allowed to access specific shares in
blueyonderairlines.com.
• Users in Blue Yonder Airlines must be able to access the secure Web servers in fabrikam.com
without receiving a warning message about the certificate.
• All administrators in Blue Yonder Airlines must be able to administer Active Directory objects
in fabrikam.com by using their default administrative tools.
The corporate security policy states that when a domain controller fails, all references to the domain
controller must be permanently removed from the domain before the domain controller is replaced.
Blue Yonder Airlines must meet the following virtualization requirements:
• Ensure that each developer can create and manage his own virtual machine (VM).
• Prevent the developers from configuring the settings of other developers’ VMs.
• Prevent the developers from creating VMs that use more than 2 GB of memory,
• Minimize the amount of bandwidth used when users access files over WAN links.
###EndCaseStudy###
You need to recommend changes to the Active Directory infrastructure to ensure that the user is
redirected to the replica in his office.
What should you include in the recommendation?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 8
Blue yonder Airlines
COMPANY OVERVIEW
Blue Yonder Airlines has a main office and four branch offices.
PLANNED CHANGES
Blue Yonder Airlines plans to implement the following changes:
• Upgrade all client computers to Windows 7.
• Deploy a virtualization solution for the company’s developers.
• Implement coexistence between the users in Fabrikam and the users in Blue Yonder Airlines.
EXISTING ENVIRONMENT
One user in each office runs a point-of-sale (POS) application named Appl. App 1 requires access to a
local USB device and only runs on Windows XP Service Pack 3 (SP3).
Blue Yonder Airlines has a finance department.
Business Goals
Blue Yonder Airlines plans to acquire a company named Fabrikam, Inc. Fabrikam has an Active
Directory forest named fabrikam.com. Fabrikam.com contains only domain controllers that run
Windows Server 2003 Service Pack 2 (SP2).
Fabrikam.com contains multiple Web servers that are secured by using certificates. All server
certificates are issued by the internal CA of Fabrikam.
Existing Active Directory Environment
The network contains an Active Directory forest named blueyonderairlines.com. The forest contains
a single domain.
The domain contains domain controllers that run Windows Server 2008. The domain controllers are
configured as shown in the following table.
The forest contains a single Active Directory site. A subnet object is defined for each office.
The forest contains a certification authority (CA).
Existing Network Infrastructure
Each office has a file server and a print server.
The main office has a file server named Server1. The shared folders on Server1 are configured as
shown in the following table.
Blueyonderairlines.com has a standalone DFS root named \\serverl\corp that contains a link named
sales. Replicas of \\serverl\corp\sales are deployed in each office.
Current Administration Model
Administrators manage the Active Directory objects by using the Active Directory module for
Windows Power Shell.
TECHNICAL REQUIREMENTS
Blue Yonder Airlines must meet the following requirements for coexistence between Blue Yonder
Airlines and Fabrikam:
• Only specific users in Fabrikam must be allowed to access specific shares in
blueyonderairlines.com.
• Users in Blue Yonder Airlines must be able to access the secure Web servers in fabrikam.com
without receiving a warning message about the certificate.
• All administrators in Blue Yonder Airlines must be able to administer Active Directory objects
in fabrikam.com by using their default administrative tools.
The corporate security policy states that when a domain controller fails, all references to the domain
controller must be permanently removed from the domain before the domain controller is replaced.
Blue Yonder Airlines must meet the following virtualization requirements:
• Ensure that each developer can create and manage his own virtual machine (VM).
• Prevent the developers from configuring the settings of other developers’ VMs.
• Prevent the developers from creating VMs that use more than 2 GB of memory,
• Minimize the amount of bandwidth used when users access files over WAN links.
###EndCaseStudy###
You need to recommend a management strategy for the planned virtualization solution. The
strategy must meet the company’s technical requirements.
What should you include in the recommendation?